Nowadays, it's extremely easy to generate SSH keys. No matter if you're using Windows, MacOS, or a Linux-based operating system.
You just need to go through 3 steps:
- Run the
ssh-keygencommand. - Pick an optional passphrase to encrypt your private key.
- Copy / Paste the public key where you need it.
So let's get right into it, and see how to generate a public/private SSH key pair. Then we'll explore how to add the public key to a GitHub repository.
And just in case you need these keys for a Linux server, instead of a GitHub repository, the steps to generate them are the same. So you can follow this tutorial for that purpose too.
How to Generate SSH Keys on Windows, MacOS, and Linux
Whatever your operating system is, the steps to generate these keys are almost the same. Because we'll use the same tool, called ssh-keygen – a command-line application that is pre-installed on most modern platforms.
On Windows:
Press the Windows key (or click on the Start Menu), type "cmd", and open Command Prompt.
On MacOS, and Linux:
Open up your favorite terminal emulator.

That's about the only significant difference between these platforms.
Generate Public/Private Key Pair with ssh-keygen
In Command Prompt, or the terminal emulator, type this command:
ssh-keygenNext, press Enter at this first prompt:
This will save the key in the default location displayed on-screen. Make note of the exact path and filename where this key is saved. In my case it was:
C:\Users\Alex/.ssh/id_ed25519But this will differ on your machine depending on:
- What your user's directory is. This will give you the starting path to your private/public key files. Usually, you will just have to replace the username (
alexorAlexin these examples).- On Windows
C:\Users\Alexwill be replaced by your actual user directory. - On Linux
/home/alexwill be replaced by your actual user directory. - And on MacOS
/Users/Alexwill be replaced by your user directory on that platform.
- On Windows
- Next, the name of your files (which store the public and private keys) will depend on the algorithm used to generate them. Since the
ed25519algorithm was used in this case, the private key is saved in a file calledid_ed25519. And the public key inid_ed25519.pub.
In the past, the default algorithm used to generate these keys was RSA. So the files were called id_rsa and id_rsa.pub.
This default changes as the years go by. It depends on what algorithm is considered "best" in the future. If the default changes, the default filenames might also change. But they will be displayed on-screen as you generate them, so it's not an issue.
Encrypt Your Private Key File with a Passphrase (Optional)
At the next two prompts you have two choices:
- Either press Enter (twice) if you don't want to protect your private key with a passphrase (password).
- Or type a passphrase if you want to encrypt your private key. And then repeat the passphrase a second time, to make sure you typed it right.
So what does this do?
Let's say you carry the private key (that you generated) on an USB stick. If someone plugs it in their computer, while you leave it unattended, they could steal your private key (which is just a text file).
But if you opt to pick a passphrase here, then that file will be encrypted. A person is still able to steal that file from an unattended USB stick. But they cannot use it without the correct passphrase. Because they won't be able to decrypt the content and retrieve the original data.
At this point, job done! You generated your keys with a simple command and an (optional) passphrase.
At the end of all this you'll get some pretty ASCII art:
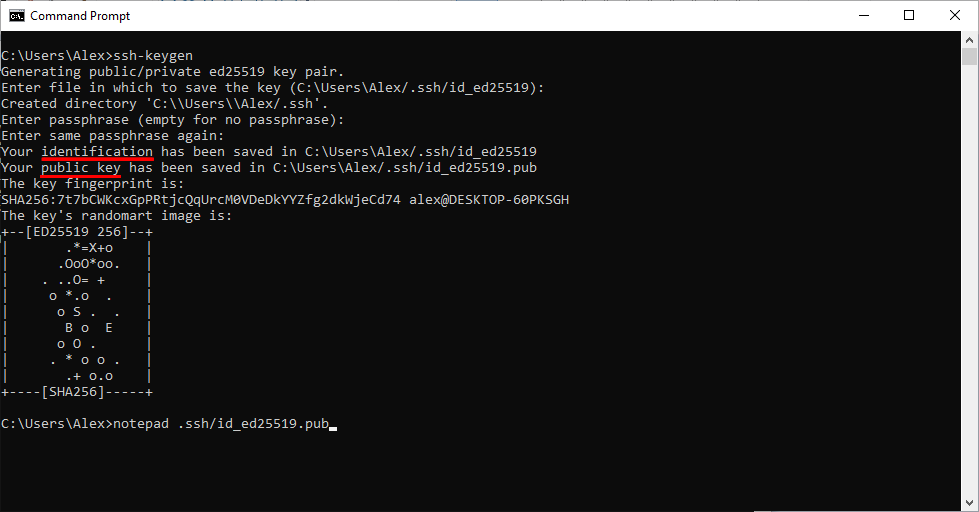
And it will tell you where your keys were saved.
Location of SSH Private and Public Key Files
In the previous screenshot, you can see two things:
- Identification is the private key. In my case, it was saved in
C:\Users\Alex/.ssh/id_ed25519. As the name suggests, the private key should be kept safe, and in a private spot. Not to be shared with anyone! The private key is what you normally use to unlock, or log in, to get access, or privileges to something. - Public key shows you where the public key was saved. In my case, it was stored in
C:\Users\Alex/.ssh/id_ed25519.pub. This is like the lock on a door. So it's not meant to be kept secret. You can "install" this lock anywhere. You can share it with an admin that asks for it to give you access to something. Maybe add it to a server, so you're able to log in. Or a GitHub repository.
So the private key is like a unique key that can unlock the unique "lock", the public key. They match each other.
Since it's only the public key that you need to move around and "install" it as a lock to a GitHub repository, or Linux server (or whatever you want to log in to), you can open it up with Notepad (or any text editor on MacOS / Linux).
.ssh is the name of a directory. A weird name, because it starts with a "." dot. Something you don't often see on Windows, but it's common practice on Unix-like systems (for certain special directories).notepad .ssh/id_ed25519.pubAnd copy this entire text, which you will then paste wherever you need it:
Let's see how we can add it to a GitHub repository.
Add SSH (Public) Key to GitHub Repository
As you view the id_ed25519.pub file, where your public key is stored, you can go through an optional step.
Optional: Add a Comment to Your Public Key (For Easier Identification)
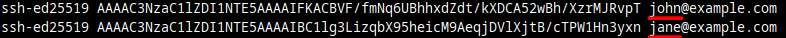
If your key looks like this:
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJF2J5vFF79VqwDEqIiV7KdUTMuTEcxhWRXDW2KKS1Je alex@DESKTOP-60PKSGH
You can change the last part, alex@DESKTOP-60PKSGH, and replace it with your actual email instead.
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJF2J5vFF79VqwDEqIiV7KdUTMuTEcxhWRXDW2KKS1Je alexandru@example.com
This last field is called a comment for your SSH key. Another way to look at it: You can consider it a human-readable identifier.
It's not used for cryptographic purposes. That's why you can freely edit it. But the rest of the text has to remain exactly how it is.
When can this comment / identifier be useful? Well, imagine you add 10 public keys to a server, or repository. Since you can authorize multiple people / keys this way. And it's common practice to do so. This can end up being a file with 10 different lines inside. With identifiers like these, at the end of each line, it makes it easier to see what key belongs to which person.
How to Add Your Public Key to a GitHub Repository
Jump to the GitHub repository you want to use. And go to the Settings tab:
In the left-side menu, click on the Deploy Keys entry:
Here, click on the Add deploy key button:
Three things you need to do here.
- For the Title, you can use anything you like. Just pick a name that will remind you, months from now, what this key is (the person it belongs to, or the key's purpose; whatever is important to remember).
- In the Key field paste the public key you copied from the
id_ed25519.pubfile. - And, very important, tick (enable) the Allow write access box. This will allow you to push / write to your repository from your local machine (or wherever your private key is; the one associated with the public key from
id_ed25519.pub)
Click Add key, and that's it. Job done!
Conclusion
As you can see, creating SSH keys is very easy, nowadays. It was harder in the past when platforms like Windows did not have ssh-keygen pre-installed. And you needed to install additional applications (like PuTTY). But that's no longer necessary. Everything is ready to go.
And just in case you don't need these SSH keys for GitHub, but need them to log in to a remote Linux server instead, that's also easy to do. If you use AWS, Google Cloud, or Microsoft Azure, there's usually a web page where you can add your public SSH key, from the id_ed25519.pub file. Just copy it from your computer, and paste it there.
And when you spin up your compute instance (and enable that key), it will be pre-configured to let you log in, from your computer, with a simple:
ssh your_user@your_IP_addresscommand.
The ssh utility is also pre-installed on Windows, Linux, and MacOS, and it will automatically find the private key necessary to authorize this login (if you saved it in the default location).















Discussion