Cloud-Native Architecture: The 5 Key Principles Explained
Learn the 5 key principles of cloud-native architecture, emphasizing scalability, stateless design, and modern security.
Once upon a time, hosting applications was a challenging endeavor. Picture this: you had an innovative application idea, but the infrastructure to bring it to life was elusive. Applications were tailored to fit specific hardware, primarily because that's all you had at your disposal. This rigidity posed significant hurdles, especially when it came to scaling or transitioning them across varied environments.
Fast forward to today, and the landscape has dramatically transformed thanks to the magic of cloud computing. No longer are we bound by the constraints of limited infrastructure. With just a few clicks, we can now set up the required infrastructure in a jiffy. This newfound flexibility means applications can effortlessly scale across multiple servers or transition between diverse environments, catering to our ever-evolving needs.
However, there's a catch. To truly harness the power of the cloud, our applications need a special touch. They must be designed with scalability, portability, and maintainability at their core. Enter the realm of Cloud-Native Architecture.
Scalability, Portability, Maintainability
Cloud-native architecture isn't just a buzzword; it's a paradigm shift in how we approach application design.
It's about crafting applications that not only thrive in the cloud but also leverage all the robust capabilities these platforms offer.
Whether you're working with an on-premises private cloud, giants like AWS, Azure, and GCP, or exploring hybrid models, cloud-native is the way forward, ensuring your applications are always at their peak performance. So, as we sail into this new era, let's embrace cloud-native and unlock a world of possibilities!
In today's blog post, we will delve into the five fundamental principles of cloud-native architecture, as articulated by Tom Grey from Google. Tom's insights provide a comprehensive understanding of the core tenets that underpin cloud-native systems. So, let's dive in and explore these principles in detail.
Hold on a moment! If you prefer a visual deep dive into this topic, Mumshad Mannambeth has crafted an engaging video version. Feel free to check it out for a more dynamic perspective.
1. The Shift to Automation in Cloud Architecture
Gone are the days when setting up a server was a drawn-out process. Previously, we'd order, wait, install, and configure, often taking weeks. A single error could lead to major issues down the line.
Now, with modern cloud platforms, server provisioning is a matter of a few clicks. This shift underscores the importance of designing architectures with automation at the forefront. Doing so ensures quick resource allocation and consistent infrastructure.
To truly leverage automation:
- Choose automation-friendly tools and services.
- Adopt an 'infrastructure as code' approach.
- Implement continuous integration and delivery.
By focusing on automation, we reduce errors, enhance consistency, and speed up processes, allowing more time for application development and improvement.
Choose automation-friendly tools and services.
Example: Using Docker for containerization. Docker allows you to package an application with all its dependencies into a standardized unit for software development.
# Dockerfile
FROM node:14
WORKDIR /app
COPY . .
RUN npm install
CMD ["npm", "start"]# Build the Docker image
docker build -t myapp:latest .Adopt an 'infrastructure as code' approach.
Example: Using Terraform to provision AWS EC2 instances.
provider "aws" {
region = "us-west-1"
}
resource "aws_instance" "example" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
tags = {
Name = "ExampleInstance"
}
}# Initialize and apply Terraform configuration
terraform init
terraform applyImplement continuous integration and delivery.
Example: Using Jenkins to automate the build and deployment process.
// Jenkinsfile
pipeline {
agent any
stages {
stage('Build') {
steps {
echo 'Building the project...'
// Your build commands here
}
}
stage('Deploy') {
steps {
echo 'Deploying the project...'
// Your deployment commands here
}
}
}
}Once the Jenkinsfile is in place, Jenkins can automatically pick up the changes from your repository, build the project, and deploy it based on the defined pipeline.
These are basic examples to illustrate the concepts. In real-world scenarios, the configurations and scripts would be more detailed and tailored to specific project requirements.
2. Design Components to be Stateless
In earlier days, infrastructure limitations often meant applications weren't designed for simultaneous multi-instance running. We leaned on sticky sessions, where load balancers kept track of user-instance interactions. This led to applications heavily depending on shared state across components. A hiccup in one component? The entire application risked crashing.
Enter cloud-native architecture, and the game changed. We transitioned from bulky monolithic applications to the sleek world of microservices. At the heart of this shift lies the principle of stateless design.
But what does "stateless" mean? And what exactly is a "state"? Simply put, a state represents a user's current situation within an application. Is the user logged in? What's in their shopping cart? Previously, if this state data resided in the application's local memory or disk and the application crashed, all user progress vanished.
In today's era of hyperscale applications, such setbacks are unacceptable. Applications must function seamlessly, regardless of the instance serving a client. Hence, detaching state from the application instance is crucial.
Opting for a stateless architecture enhances application resilience, fault tolerance, and scalability. It's not just a trend; it's the future of efficient application design.
Stateless vs. Stateful: A Practical E-commerce Example
Imagine you're crafting an e-commerce platform. Users flock to your site, searching for products and filling their shopping carts. Now, how do you manage this shopping cart data?
In a traditional stateful setup, this data would nestle within the user's session on the application server. While many e-commerce platforms opt for database storage, let's assume for a moment that our cart data resides solely in the user's session. The catch? If that server faces an outage or gets overwhelmed, all that precious cart data vanishes. And if you're thinking of scaling out, you're in for a challenge. Every new instance needs access to this shared session data.
Enter the stateless approach. Instead of anchoring cart data to user sessions, we'd store it in Redis. Each user request would then carry the necessary identifiers to fetch and modify this centralized data. Let's illustrate with a Python code snippet using Flask and Redis:
from flask import Flask, request, jsonify
import redis
app = Flask(__name__)
r = redis.StrictRedis(host='localhost', port=6379, db=0)
@app.route('/add_to_cart', methods=['POST'])
def add_to_cart():
user_id = request.json.get('user_id')
product_id = request.json.get('product_id')
# Store cart data in Redis
r.sadd(f'cart:{user_id}', product_id)
return jsonify({"message": "Product added to cart successfully!"})
@app.route('/get_cart', methods=['GET'])
def get_cart():
user_id = request.args.get('user_id')
# Retrieve cart data from Redis
cart_items = r.smembers(f'cart:{user_id}')
return jsonify({"cart_items": list(cart_items)})By leveraging Redis in a stateless architecture, we not only ensure data safety but also gain the benefits of speed and effortless scalability. It's a testament to the elegance and efficiency of contemporary application design.
3. Favour Managed Services
In the past, setting up an IT infrastructure was a daunting task. Imagine ordering servers, installing software, and configuring networks. It wasn't just about the initial setup; the ongoing management was equally taxing. Fast forward to today, and the cloud has revolutionized how we approach IT infrastructure. Enter the principle of "Favour Managed Services."
What Are Managed Services?
Managed services are essentially ready-to-use cloud solutions that cater to specific functionalities. Think databases, message queues, or machine learning models. The beauty of these services? The cloud provider shoulders the responsibility of the underlying infrastructure. Your role is simply to integrate these services into your application.
Redis: A Case Study
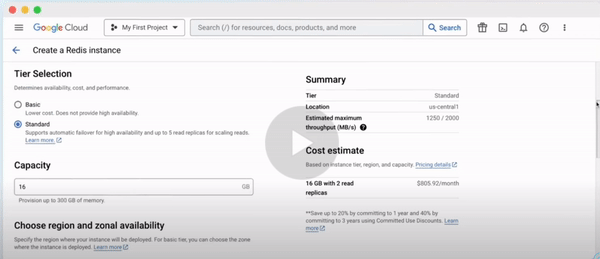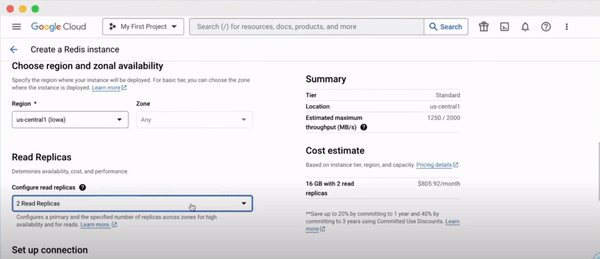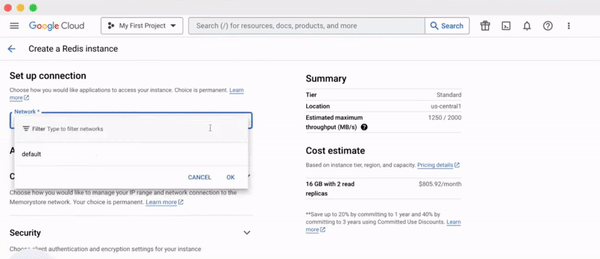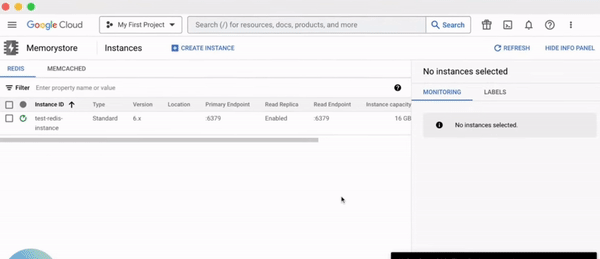
Consider Redis, a popular in-memory data structure store. The traditional approach would involve setting up a server, configuring it, installing Redis, and then continuously monitoring and maintaining it. Sounds exhausting, right?
Now, with managed Redis services like those on Google Cloud or AWS, you can bypass these tedious steps. Within minutes, you have access to a Redis instance, ready to power your application.
The Advantages of Managed Services
- Efficiency and Resource Saving: No more getting bogged down with infrastructure management. This means more time and resources to channel into your core application development.
- Scalability and Reliability: Managed services are designed to be robust. Whether it's handling increased user loads or ensuring minimal downtime, cloud providers have got you covered.
- Enhanced Security: With the vast resources at their disposal, cloud providers invest heavily in security. By using managed services, you're essentially leveraging their security expertise, ensuring your data remains safe and compliant.
4. Practice Defence in Depth
In the evolving landscape of cloud-native applications, security has taken center stage. Gone are the days when a simple perimeter-based approach was enough. Welcome to the era of 'Defense in Depth.'
The Shortcomings of Traditional Security
Historically, security models were built on the belief in a fortified perimeter. Imagine a castle with tall walls and a moat. Everything inside the walls was deemed 'trusted,' while everything outside was 'untrusted.' This approach, however, had its pitfalls. It was vulnerable to insider threats and external tactics like spear phishing. The shift towards flexible and mobile working further eroded the sanctity of this perimeter.
Why Cloud-Native Demands More
Cloud-native architectures, born in the realm of internet-facing services, have always been on the frontline, battling external threats. This exposure necessitated a more robust security model. Instead of a single barrier, cloud-native security emphasizes a multi-layered defense strategy. Every layer, every component, is fortified. From firewalls and intrusion detection systems to access controls and encryption, security is omnipresent.
But what truly sets cloud-native security apart is its inherent distrust. In this model, there's no 'inside' or 'outside.' Every component, even if deemed 'internal,' is treated with caution. Authentication is required at every interaction, ensuring that each component is isolated and protected from its peers.
Beyond Just Authentication
Cloud-native security doesn't stop at authentication. It delves deeper, incorporating measures like rate limiting and protection against script injections. The philosophy is simple: every component should be its own guardian, shielding itself from potential threats, be it from other components or external actors. This self-reliant approach not only bolsters security but also streamlines deployment in cloud environments where a trusted network might be absent.
The Multi-Layered Firewall: A Technical Dive into Defense in Depth
Let's delve into the world of network security and consider a multi-layered firewall system, a staple in many organizations' cybersecurity strategies. This system can serve as a technical analogy for the Defense in Depth approach in cloud-native architectures.
Edge Firewall (Perimeter Security):
As the first line of defense, the edge firewall filters out the most common types of attacks from the internet, such as DDoS attacks or port scans. This is akin to the traditional perimeter-based security.
Internal Network Segmentation (Authentication):
Once past the edge firewall, traffic doesn't get free rein. The internal network is segmented into various zones (e.g., DMZ, production, development). To move between these zones, proper authentication and specific rules are required, reflecting the authentication layer in cloud-native systems.
Application Firewall (Internal Checks):
Even if traffic has the right credentials to pass through network segments, it faces another hurdle: the application firewall. This layer inspects the traffic for any application-specific attacks, such as SQL injection or cross-site scripting. It's a testament to the Defense in Depth principle that there's no real 'inside' or 'outside'.
Endpoint Security (Multi-layered Security):
On individual servers and devices, endpoint security solutions are deployed. These tools, like antivirus or intrusion prevention systems, provide another layer of defense, ensuring that even if malicious traffic gets this far, it's stopped before causing harm.
Data Encryption (Self-Protecting Data):
Data, both at rest and in transit, is encrypted. Even if an attacker manages to access the data, without the decryption keys, it's gibberish. This mirrors the principle where each component in a cloud-native system has its own protective measures.
Security Information and Event Management (SIEM) System (Continuous Monitoring):
All activities across the network are continuously monitored and logged by the SIEM system. It uses advanced algorithms to detect any anomalies or suspicious patterns, allowing for swift action if something seems amiss.
In this technical analogy, the multi-layered firewall system showcases how, at every step, there are robust security measures in place. Even if an attacker bypasses one layer, they're immediately faced with another challenge. This layered approach, where each component has its own defense mechanism, embodies the essence of Defense in Depth in cloud-native architectures.
5. Always Be Architecting
In the dynamic realm of cloud-native systems, the adage "if it's not broken, don't fix it" takes a backseat. Instead, the mantra is "Always Be Architecting." Here's why.
The Ever-Changing Cloud Landscape
Cloud-native environments are in a state of perpetual evolution. With the constant influx of new technologies and shifting customer demands, resting on one's laurels isn't an option. The architecture of applications needs regular scrutiny and refinement.
Proactive Over Reactive
Rather than adopting a reactive stance—waiting for issues to arise and then addressing them—the focus is on proactive optimization. Continuous monitoring and analysis of the architecture spotlight potential bottlenecks or areas ripe for enhancement. This proactive approach not only prevents system breakdowns but also ensures that the architecture is primed to handle future challenges.
Staying Ahead in the Game
In a market that's always on the move, frequent architectural updates are the key to staying relevant. Ensuring that systems are contemporary and aligned with customer needs is paramount.
In Essence
"Always Be Architecting" isn't just a principle; it's a mindset. It's about being vigilant, agile, and committed to delivering the best to customers by ensuring systems are at their optimal best.
A Real-World Example: Streaming Services
Consider the world of online streaming services. A few years ago, 1080p was the gold standard for video quality. Fast forward to today, and we have 4K, HDR, and even 8K streams. A streaming service that adhered to the "if it's not broken, don't fix it" mindset would still be offering just 1080p streams, losing subscribers to competitors offering higher resolutions.
But by embracing the "Always Be Architecting" principle, these platforms continuously refine their infrastructure. They adapt to new video codecs, optimize their content delivery networks for faster streaming, and regularly update their user interfaces based on user feedback. This constant evolution ensures they remain leaders in a fiercely competitive market.
Conclusion:
That concludes our deep dive into the five core principles of cloud-native architecture. We appreciate you taking the time to read our insights. For more in-depth discussions on cloud-native computing and DevOps, explore other articles on our blog.
If you've found our content valuable, consider subscribing for weekly updates. Have any questions or thoughts? Drop them in the comments section below.
Until our next post, farewell! :)
