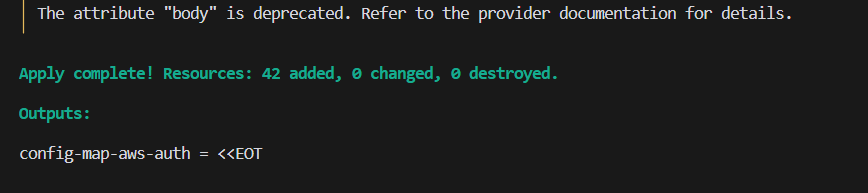
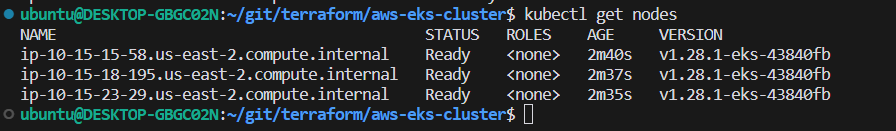
I’m trying to create an EKS cluster.
I’m using the instructions provided in [Playground Series] How to create an EKS cluster in KodeKloud Playground?
At the step of creating the self managed roles through the Cloud Formation stack, it fails.
I think it is because I am unable to provide an IAM Role having the policies AmazonEKSWorkerNodePolicy, AmazonEC2ContainerRegistryReadOnly and AmazonEKS_CNI_Policy.
When I try to create such a role through the IAM, the user does not have the permissions to do so.
Error:
- Policy AmazonEKSWorkerNodePolicy not attached.
User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role eks with an explicit deny in an identity-based policy.
Can you suggest how to overcome this issue?
It fails while trying through Terraform as well.
Following the instructions here - https://github.com/kodekloudhub/certified-kubernetes-administrator-course/tree/master/managed-clusters/eks
Error in terraform apply:
aws_vpc_security_group_egress_rule.node_egress_all: Creation complete after 1s [id=sgr-0e2e36c11a331a313]
aws_vpc_security_group_ingress_rule.node_security_group_ingress: Creation complete after 1s [id=sgr-049d7adf478b04a70]
╷
│ Error: attaching policy arn:aws:iam::aws:policy/AmazonEKSClusterPolicy to IAM Role demo-eks: AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks with an explicit deny in an identity-based policy
│ status code: 403, request id: e9886458-8f96-46f8-91e1-b598b47dac0a
│
│ with aws_iam_role_policy_attachment.demo_eks_AmazonEKSClusterPolicy,
│ on eks.tf line 25, in resource “aws_iam_role_policy_attachment” “demo_eks_AmazonEKSClusterPolicy”:
│ 25: resource “aws_iam_role_policy_attachment” “demo_eks_AmazonEKSClusterPolicy” {
│
╵
╷
│ Error: attaching policy arn:aws:iam::aws:policy/AmazonEKSVPCResourceController to IAM Role demo-eks: AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks with an explicit deny in an identity-based policy
│ status code: 403, request id: 76c3472f-0804-45fb-8977-9bb07f37faaa
│
│ with aws_iam_role_policy_attachment.demo_eks_AmazonEKSVPCResourceController,
│ on eks.tf line 32, in resource “aws_iam_role_policy_attachment” “demo_eks_AmazonEKSVPCResourceController”:
│ 32: resource “aws_iam_role_policy_attachment” “demo_eks_AmazonEKSVPCResourceController” {
│
╵
╷
│ Error: creating IAM Role (demo-eks-node): 4 errors occurred:
│ * attaching managed policy (arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore): AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: 12d010f3-8f3c-4500-87b9-d67aee393cd6
│ * attaching managed policy (arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy): AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: 8c1cb30b-7c48-4a19-a06f-67972d7e8abf
│ * attaching managed policy (arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly): AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: fa17f70e-c197-4bd3-998c-eeda8cfbdcd0
│ * attaching managed policy (arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy): AccessDenied: User: arn:aws:iam::907291881199:user/odl_user_1135026 is not authorized to perform: iam:AttachRolePolicy on resource: role demo-eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: 5160d6c1-ed8c-4638-945f-7a24b583e0e5
│
│
│
│ with aws_iam_role.node_instance_role,
│ on nodes.tf line 50, in resource “aws_iam_role” “node_instance_role”:
│ 50: resource “aws_iam_role” “node_instance_role” {
│
╵
can you try use the next one repository to create a eks cluster with terraform:
i modified this for work with the kodekloud permissions
Both the KodeKloud endorsed methods above should work.
Were you using the us-east-1 region? They are not guaranteed to work in any other region
Something’s changed in how the playgrounds are configured. This was working last week. I will inform the lab team
@Thelman-Sanchez Suggest you test your version again to see if it is affected by this.
Thanks to both @Alistair_KodeKloud and @Thelman-Sanchez for offering to help.
@Alistair_KodeKloud is right. This worked till last week. There has been some change this week in the way the IAM permissions are set on the playground that denies a policy to be attached to a role.
Thanks for forwarding the issue to the lab team, I’ll wait for the fix.
@Thelman-Sanchez I have tried the steps you shared and it fails with the same issue of missing the access to attach a policy to a role.
╷
│ Error: attaching policy arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy to IAM Role eks-node: AccessDenied: User: arn:aws:iam::098664842351:user/odl_user_1136513 is not authorized to perform: iam:AttachRolePolicy on resource: role eks-node with an explicit deny in an identity-ba ed policy
│ status code: 403, request id: bd81fb76-97ca-4029-9e55-8beb2e3feb57
│
│ with aws_iam_role_policy_attachment.eks-node-AmazonEKSWorkerNodePolicy,
│ on iam.tf line 76, in resource “aws_iam_role_policy_attachment” “eks-node-AmazonEKSWorkerNodePolicy”:
│ 76: resource “aws_iam_role_policy_attachment” “eks-node-AmazonEKSWorkerNodePolicy” {
│
╵
╷
│ Error: attaching policy arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy to IAM Role eks-node: AccessDenied: User: arn:aws:iam::098664842351:user/odl_user_1136513 is not authorized to perform: iam:AttachRolePolicy on resource: role eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: 8f413d54-165e-4210-855d-30f46de98ee6
│
│ with aws_iam_role_policy_attachment.eks-node-AmazonEKS_CNI_Policy,
│ on iam.tf line 81, in resource “aws_iam_role_policy_attachment” “eks-node-AmazonEKS_CNI_Policy”:
│ 81: resource “aws_iam_role_policy_attachment” “eks-node-AmazonEKS_CNI_Policy” {
│
╵
╷
│ Error: attaching policy arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly to IAM Role eks-node: AccessDenied: User: arn:aws:iam::098664842351:user/odl_user_1136513 is not authorized to perform: iam:AttachRolePolicy on resource: role eks-node with an explicit deny in an identity-based policy
│ status code: 403, request id: 0e2b5770-43e5-48c8-9457-5f2748f12f0a
│
│ with aws_iam_role_policy_attachment.eks-node-AmazonEC2ContainerRegistryReadOnly,
│ on iam.tf line 86, in resource “aws_iam_role_policy_attachment” “eks-node-AmazonEC2ContainerRegistryReadOnly”:
│ 86: resource “aws_iam_role_policy_attachment” “eks-node-AmazonEC2ContainerRegistryReadOnly” {
@ adityasamant.learnin @ Alistair_KodeKloud
i dont have the problem, all is okay for me, i used us-east-2 region
@Thelman-Sanchez @Alistair_KodeKloud The labs have been fixed now, I do not face the IAM issue anymore.
Thank you both for your help.
This issue can be marked closed.
I am facing the same issue now. User: arn:aws:iam::211125465619:user/kk_labs_user_574432 is not authorized to perform: iam:PassRole on resource: arn:aws:iam::211125465619:role/AmazonEKSAutoClusterRole
You cannot build with EKS Auto mode in playground
You must follow exactly the instructions here to build a cluster that falls within the playground restrictions