Failed to delete user “kk_labs_user_780366”. User: arn:aws:iam::992382659763:user/kk_labs_user_780366 is not authorized to perform: iam:DeleteLoginProfile on resource: user kk_labs_user_780366 because no identity-based policy allows the iam:DeleteLoginProfile action ( Can you please delete this service from the lab experiments from you’re end because i unable to delete this services and i created this a few months ago but i don’t have administrative access to delete it. So that, it can be helpful for me
i unable to delete this services and i created this a few months ago but i don’t administrative access to delete it.
All the resources created during a session in Cloud Playgrounds are cleared out at timeout.
Cloud Playgrounds have limited access due to security and cost concerns and I believe it does not provide users access to delete user credentials unless asked for a specific task.
Regards.
Iam literally disappointed for your service moreover then why do you charged a money from me if you can’t access the entire resources providing to me moreover I’m pretty much struggling about this one , if you can’t delete that resources, I can’t move forward to next part of the video without having the full access. So kindly delete it from your end of IAM resources if you can’t delete the IAM profile resources from your end I unable to create the EC2 resources of vault and it is asking a permissions to create new one . I was learning about the Aws services so please don’t waste my time about this silly things .
Can you please share the link to the lab you are working on ?
https://us-east-1.console.aws.amazon.com/iam/home?region=us-east-1#/users , Hey just look at the following link which i have been encountering the issue for a long days ago and Especially delete the IAM resources from the services and fix the issue ASAP moreover when the session was timeout it won’t be clear the data what i had created the resources in aws console probably there is lot of issue’s in the kodekloud not only one thing to rectify about it .
Thanks for sharing the link.
I’ll escalate the issue to check how can we assist you with this.
Nobody can respond about the issue and i still waiting for you’re team to fix the issue and its already 48 hours are passedaway then who will be fix the issue, if you cant be respond as quickly .
Failed to delete user “kk_labs_user_780366”. User: arn:aws:iam::992382659763:user/kk_labs_user_780366 is not authorized to perform: iam:DeleteLoginProfile on resource: user kk_labs_user_780366
You cannot delete or modify the user you are logged in as.
You can do limited things with IAM users.
The following operations are permitted, as long as you create a new user whose name starts with iamuser, e.g.
The operations you can perform on such users are limited to
"iam:CreateUser",
"iam:TagUser",
"iam:ListUserTags",
"iam:DeleteUser"
"iam:CreateLoginProfile",
"iam:DeleteLoginProfile",
"iam:UpdateLoginProfile"
"iam:CreateAccessKey",
"iam:GetAccessKeyLastUsed",
"iam:GetLoginProfile",
"iam:ListSigningCertificates",
"iam:GetAccountSummary",
"iam:ListAccountAliases"
You can only attach the following managed polices (from the list of policies) to a new user
"ReadOnlyAccess",
"AmazonS3ReadOnlyAccess",
"ViewOnlyAccess",
But you can attach inline polices (create yourself), as long as the permissions you give do not exceed those of the kk_labs user you log in with or it will error. To allow otherwise would be privilege escalation.
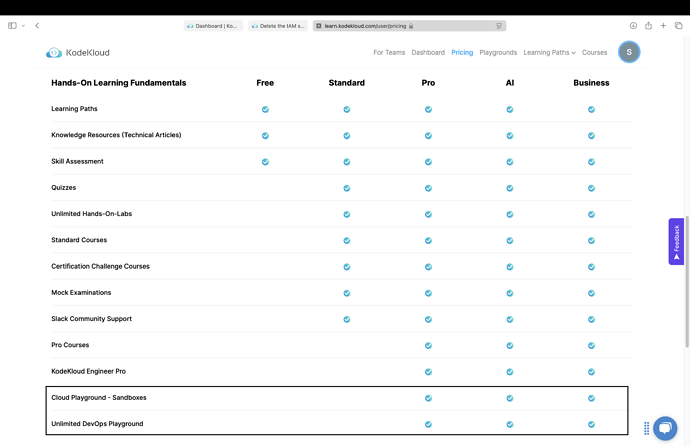
On the other hand you had provided the unlimited resourcess with out having any restrictions for exceeding the limit then how did you say like that for limited access for users , you’re policies can’t be unacceptable as you gave me unlimited resources, while i had bought it from you, kindly cross-check you’re plan’s & services says that unlimited playground services for pro subscribers & thats why i have purchased the plan as i wish for unlimited services without any interruptions.
It actually says this
A sandbox is not an unlimited environment. It is a controlled and limited one. Giving unlimited access to a cloud account would be a very stupid thing to do! I could very easily create a terraform script that would create sufficient resources to burn several thousand dollars in the 3 hours the lab is active for. Limitations on cloud sandboxes prevent people from doing that. Nobody’s going to provide that for the current cost of the pro subscription.
Additionally, resources are NOT preserved from one session to the next for the same reason - cost! If you leave infrastructure running, it is billed per second! Persistent sessions would massively increase subscription costs for everyone.
If you know previously for limited access , you should tell us earlier this all restrictions for pro user’s, then whose fault is this ? why don’t you provide the informartion about the restrictions and then how did i suppose to learn from you’re labs for limited access to user’s for different serivices can’t be accessible , therefore, Iam not asking to get free resources but you mentioned that the unlimited access for pro user’s noboby expect like this restrictions after i being purchased facing a issue’s .
Please tell me where on this page it says you have unlimited access in cloud playgrounds?
Also note that this page lists services that can be used and the restrictions applied to those services.
Pricing | KodeKloud , i appreciate you’re response quickly get in touch with me meanwhile to check it out my further details.Please review this link and let me know as soon as possible. Additionally, check the pricing section below to locate the information. There is a checklist of pricing details for various fundamentals related to labs and courses, based on the pricing list provided by your team to the users.
That is exactly the page I linked to you
![]()
Nowhere does it say cloud playgrounds are unlimited
Perhaps you didn’t review it clearly. I’m attaching the screenshot for your reference; please take a look and provide feedback as per the requirements.
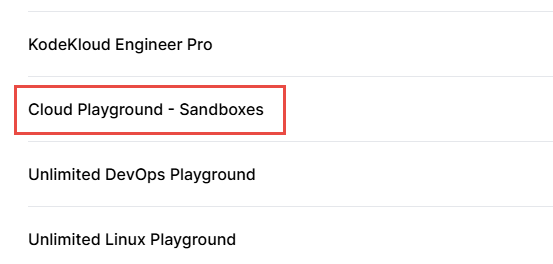
It is you are not reviewing it clearly. Cloud playground and devops playground are two separate line items in your image above.
A cloud playground is not a devops playground. Any playground with access to a cloud account is a cloud playground and the associated cloud account has the same restrictions as the plain AWS/Azure/GCP playground. That includes those playgrounds such as Hashicorp, Crossplane, pulumi etc if the name includes “+ AWS”, “+ Azure” or " + GCP"
Cloud playgrounds are limited and controlled. Always have been, always will be. We absolutely can not give unlimited access on any cloud account, or they will be abused costing vast sums of money.
The only thing that is unrestricted in any of these playgrounds are those with an associated Linux instance running in our infrastructure. You have root access to these, therefore they are unrestricted.
hey , AWS Cloud Practitioner (CLF-C02) Course | KodeKloud ,take a look at the video this doesn’t even explain to get the sufficiently visual code to get the instances to add on it and he directly explaining about some other stuff Without referring to the same video for better understanding.
What exactly would you like explained about that video? Any specific question you have?