hello Team ,
In Play ground, i am trying to create a Lambda function and you are blocking me to update IAM role or create lambda with desired minimum set of permissions also.
I have tried the same from CLI, even failing there . How can i test if i wanted to run a Lambda function ?
Sorry but these are too much of restrictions - i feel.
I’ve tried this myself and agree it is difficult to figure out what is actually permitted. One thing to try, since you’re a Pro customer, is to look at the AWS Lambda course and see if you can find something in the course that you cannot do in the playground. In the meantime, I will ask one of our engineers about this as well.
HI Rob ,
thanks for the response.
I am just trying to use a function to encrypt log groups in the account. that a simple function. very generic one - not i any of lab i am trying this out of interest.
Also - Help me understand why cant we delete Log groups ? created for testing in Play grounds
I’ve been put in touch with our playgrounds expert; I’ll ask him.
I’ve documented some issues for the playground engineer. One thing he asked me for: could we please see what’s in your role that you wanted to pass to Lambda? My guess is that we probably won’t be able to allow arbitrary roles to be submitted, but what we can do is create some sample roles that we explicitly allow, that would make using lambda in the playground more productive. So if you can post your role in a code block (use the </> key to create the block), it will help us improve the playground’s support for Lambda.
Hello Rob,
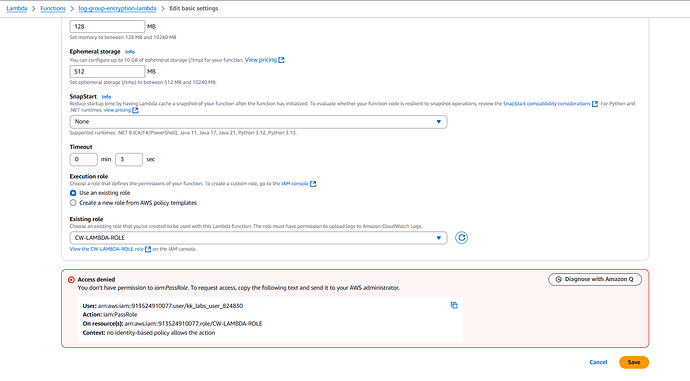
I have tried console to create role with necessary permissions and got denied to Passrole as attached in the snapshot in my first question.
Also tired to see if i can do it from console :
used below code
<
def create_lambda_role(role_name):
print(f"Processing IAM role: {role_name}")
# Check if the role exists
try:
response = iam_client.get_role(RoleName=role_name)
role_arn = response['Role']['Arn']
print(f"IAM role {role_name} already exists. Skipping creation.")
return role_arn
except ClientError as e:
if e.response['Error']['Code'] == 'NoSuchEntity':
print(f"IAM role {role_name} does not exist. Creating role.")
else:
print(f"Error retrieving IAM role {role_name}: {e}")
return None
assume_role_policy = {
"Version": "2012-10-17",
"Statement": [{
"Action": "sts:AssumeRole",
"Principal": {"Service": "lambda.amazonaws.com"},
"Effect": "Allow"
}]
}
try:
response = iam_client.create_role(
RoleName=role_name,
AssumeRolePolicyDocument=json.dumps(assume_role_policy),
Tags=get_tags(role_name, 'IAM Role')
)
# Attach policies
policy_arn = 'arn:aws:iam::aws:policy/service-role/AWSLambdaBasicExecutionRole'
iam_client.attach_role_policy(
RoleName=role_name,
PolicyArn=policy_arn
)
# Inline policy for additional permissions
policy_document = {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogGroups",
"logs:AssociateKmsKey"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"kms:ListAliases",
"kms:DescribeKey"
],
"Resource": "*"
}
]
}
iam_client.put_role_policy(
RoleName=role_name,
PolicyName='LambdaPermissions',
PolicyDocument=json.dumps(policy_document)
)
# Wait for role to be assumable
print("Waiting for IAM role to propagate...")
time.sleep(15)
role_arn = response['Role']['Arn']
print(f"IAM role created with ARN: {role_arn}")
return role_arn
except ClientError as e:
print(f"Error creating IAM role {role_name}: {e}")
return None
Here is the error message i am getting when i run above script.
IAM role EnforceLogGroupEncryptionRole does not exist. Creating role.
Error creating IAM role EnforceLogGroupEncryptionRole: An error occurred (AccessDenied) when calling the PutRolePolicy operation: User: arn:aws:iam::637423409202:user/kk_labs_user_396410 is not authorized to perform: iam:PutRolePolicy on resource: role EnforceLogGroupEncryptionRole because no identity-based policy allows the iam:PutRolePolicy action
Failed to create or locate IAM role. Exiting.
Thanks for your response; I’ve passed this on to the engineer.
OK, I’ve gotten information from the engineer how to do this (he’s also made some changes in the restrictions):
- User can create the role name which can be lambda_execution_role and it will have PassRole access as well, hope this solves the issues.
- It should be possible to set up a destination for the lambda as well.