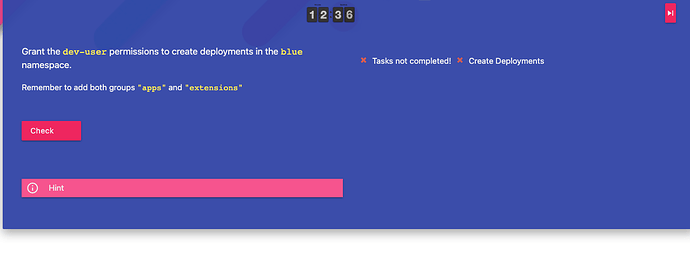
Samir:
What is wrong here (my answer in commentar=
Samir:
apiVersion: <http://rbac.authorization.k8s.io/v1|rbac.authorization.k8s.io/v1>
kind: Role
metadata:
creationTimestamp: "2021-05-05T10:10:23Z"
name: developer
namespace: blue
resourceVersion: "8535"
selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/blue/roles/developer
uid: 660bc6a8-446b-400e-9934-831fb66b6ab4
rules:
- apiGroups:
- apps
- extensions
resourceNames:
- blue-app
- dark-blue-app
resources:
- pods
- deployments
verbs:
- get
- watch
- create
- delete
Mohamed Ayman:
You have to create Role and Role binding as below in order to bind the user named « dev-user » with the « deploy-role » role created
kind: Role
apiVersion: http://rbac.authorization.k8s.io/v1|rbac.authorization.k8s.io/v1
metadata:
namespace: blue
name: deploy-role
rules:
- apiGroups: [“apps”, “extensions”]
resources: [“deployments”]
verbs: [“create”]
kind: RoleBinding
apiVersion: http://rbac.authorization.k8s.io/v1|rbac.authorization.k8s.io/v1
metadata:
name: dev-user-deploy-binding
namespace: blue
subjects:
- kind: User
name: dev-user
apiGroup: http://rbac.authorization.k8s.io|rbac.authorization.k8s.io
roleRef:
kind: Role
name: deploy-role