Hi team
I am unable to compete last question in “Use audit logs to monitor access”. Please send me solution to deploy audit policy /clear solution with snap shots. Also please tell ,how to restart kube-apiserver & also how to check.
while executing below command for creating policy ,getting below message
controlplane ~ ➜ kubectl create -f /etc/kubernetes/prod-audit.yaml
error: resource mapping not found for name: “” namespace: “” from “/etc/kubernetes/prod-audit.yaml”: no matches for kind “Policy” in version “audit.k8s.io”
ensure CRDs are installed first
Question 7.
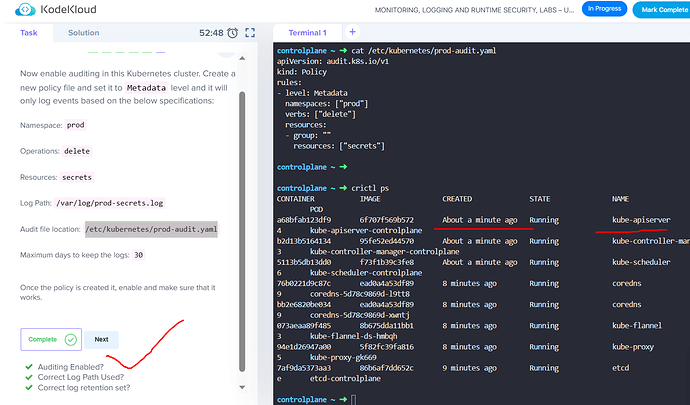
Now enable auditing in this Kubernetes cluster. Create a new policy file and set it to Metadata level and it will only log events based on the below specifications:
Namespace: prod
Operations: delete
Resources: secrets
Log Path: /var/log/prod-secrets.log
Audit file location: /etc/kubernetes/prod-audit.yaml
Maximum days to keep the logs: 30
Once the policy is created it, enable and make sure that it works.
Did you check the solution tab? @erdinesh1488
It seems like the value defined for the kind is not correct.
Hi Tej
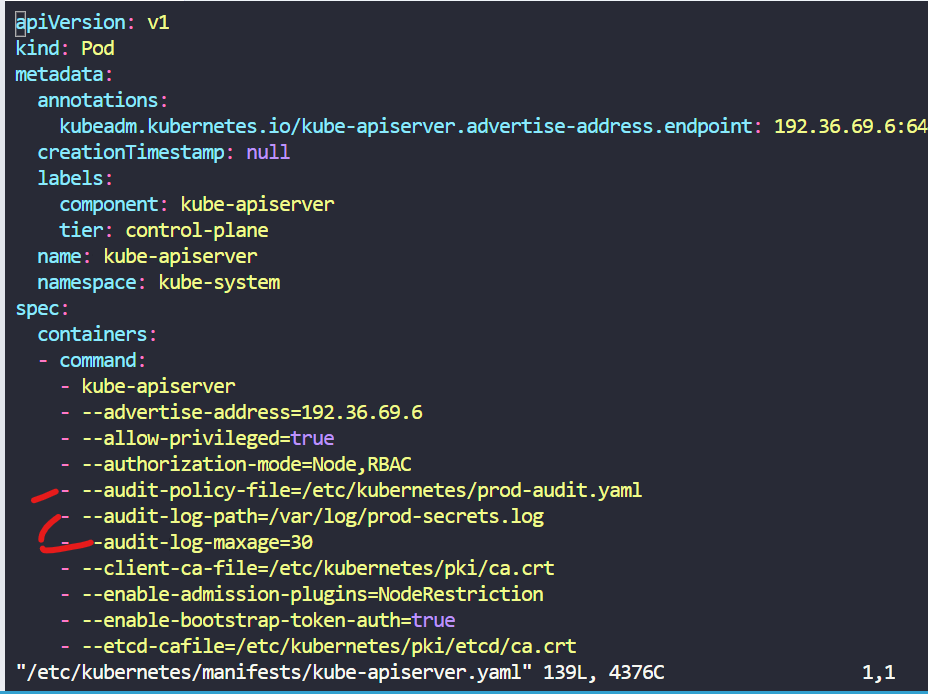
For audit policy ,below yaml file updated
vi /etc/kubernetes/prod-audit.yaml
apiVersion: audit.k8s.io/v1
kind: Policy
rules:
- level: Metadata
namespaces: [“prod”]
verbs: [“delete”]
resources:
- group: “”
resources: [“secrets”]
For enable logging in api-server
vi /etc/kubernetes/manifests/kube-apiserver.yaml
Also volume & volumeMount updated in kube-apiserver.yaml as per Solution given
Still it showing incorrect answer. Please let me know how to restart kube-apiserver
I tested it and I didn’t face any problem.
Whenever you make any changes to the k8s internal component manifest files, kubelet will get an alert about the changes, kill the pod, and recreate it with new changes.
systemctl restart kubelet
this will work ? or any other command
kubelet will take care of this; you don’t need to do anything.
See here. In this case, you create the policy and leave it for the API-Server. Don’t try to create with kubectl create/apply.