In the solution , under why egress changes are required? we expect only incoming traffic on port 80 from “-n default cyan-white-cka28-trb”?
Also why the ipblock is included in the egress? is that must ?
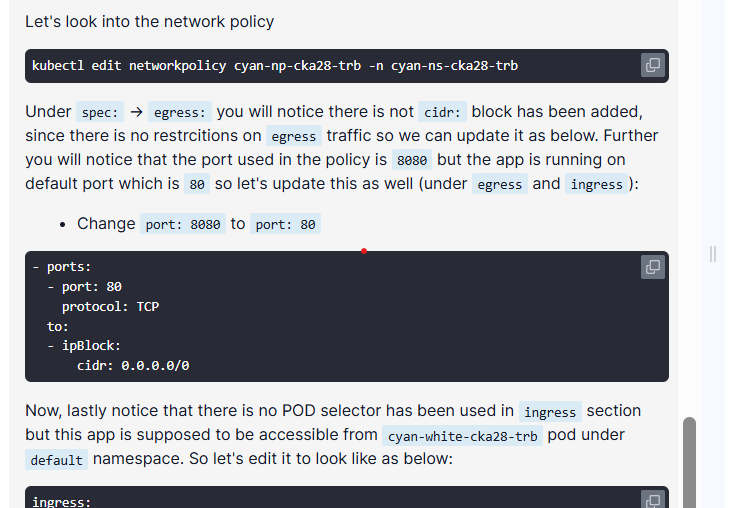
Under spec: → egress: you will notice there is not cidr: block has been added, since there is no restrcitions on egress traffic so we can update it as below
why?
In Q16, we can modify the existing network policy in the cyan-ns-cka28-trb namespace. It has an egress section, which we can ignore – it won’t affect the access to the target pod in that namespace. The part we modify is in the ingress block, and you need to do something like this:
ingress:
- from:
- namespaceSelector:
matchLabels:
kubernetes.io/metadata.name: default
podSelector:
matchLabels:
app: cyan-white-cka28-trb
ports:
- port: 80
protocol: TCP
Note that I changed the port for the ingress section, and that I added (to create an “AND” with the default namespace section) the tag for the cyan-white pod in default. This makes the requested permission that excludes the cyan-black pod, and the grader accepts this.