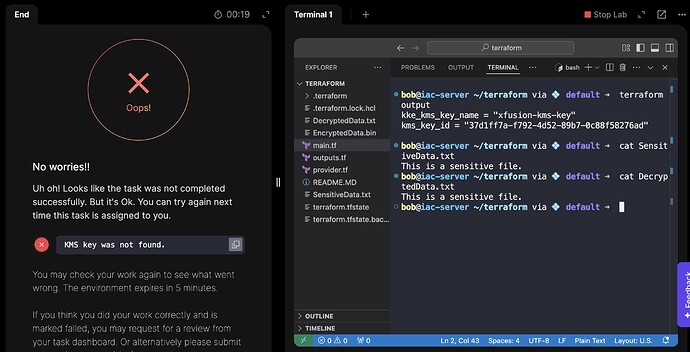
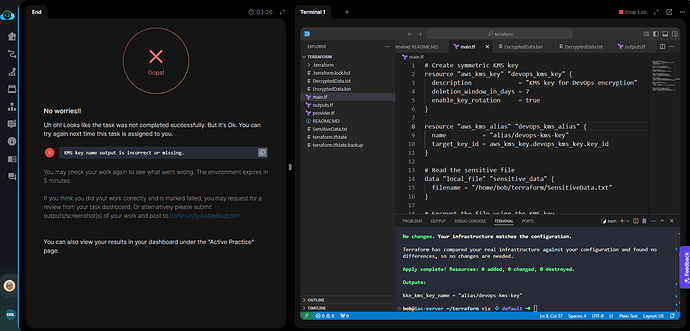
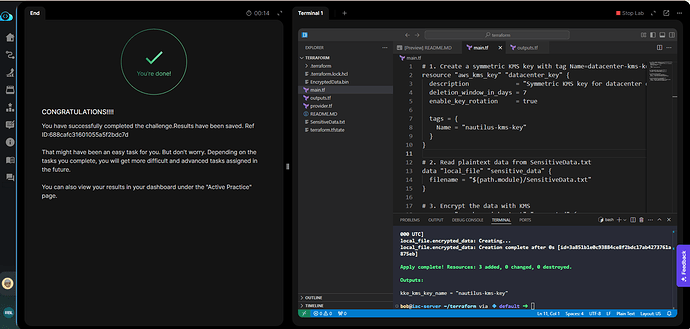
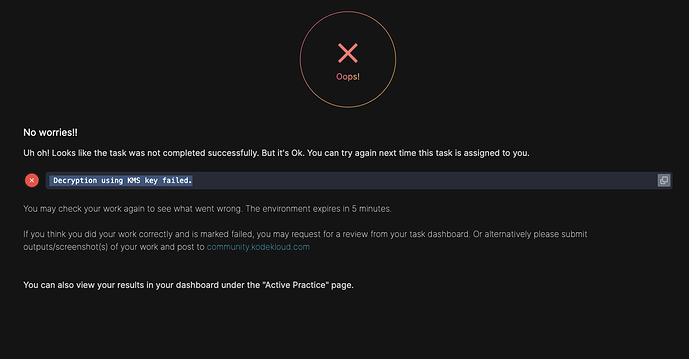
bob@iac-server ~/terraform via 💠 default ➜ terraform plan
Terraform used the selected providers to generate the following execution plan.
Resource actions are indicated with the following symbols:
+ create
<= read (data resources)
Terraform will perform the following actions:
# data.aws_kms_secrets.decrypted_data will be read during apply
# (config refers to values not yet known)
<= data "aws_kms_secrets" "decrypted_data" {
+ id = (known after apply)
+ plaintext = (sensitive value)
+ secret {
+ name = "decrypted"
+ payload = (known after apply)
}
}
# aws_kms_alias.alias will be created
+ resource "aws_kms_alias" "alias" {
+ arn = (known after apply)
+ id = (known after apply)
+ name = "alias/devops-kms-key"
+ name_prefix = (known after apply)
+ target_key_arn = (known after apply)
+ target_key_id = (known after apply)
}
# aws_kms_ciphertext.encrypted_data will be created
+ resource "aws_kms_ciphertext" "encrypted_data" {
+ ciphertext_blob = (known after apply)
+ id = (known after apply)
+ key_id = (known after apply)
+ plaintext = (sensitive value)
}
# aws_kms_key.devops-kms-key will be created
+ resource "aws_kms_key" "devops-kms-key" {
+ arn = (known after apply)
+ bypass_policy_lockout_safety_check = false
+ customer_master_key_spec = "SYMMETRIC_DEFAULT"
+ description = (known after apply)
+ enable_key_rotation = false
+ id = (known after apply)
+ is_enabled = true
+ key_id = (known after apply)
+ key_usage = "ENCRYPT_DECRYPT"
+ multi_region = (known after apply)
+ policy = (known after apply)
+ rotation_period_in_days = (known after apply)
+ tags = {
+ "Name" = "devops-kms-key"
}
+ tags_all = {
+ "Name" = "devops-kms-key"
}
}
# local_file.decrypted_file will be created
+ resource "local_file" "decrypted_file" {
+ content = (sensitive value)
+ content_base64sha256 = (known after apply)
+ content_base64sha512 = (known after apply)
+ content_md5 = (known after apply)
+ content_sha1 = (known after apply)
+ content_sha256 = (known after apply)
+ content_sha512 = (known after apply)
+ directory_permission = "0777"
+ file_permission = "0777"
+ filename = "/home/bob/terraform/DecryptedData.txt"
+ id = (known after apply)
}
# local_file.encrypted_file will be created
+ resource "local_file" "encrypted_file" {
+ content = (known after apply)
+ content_base64sha256 = (known after apply)
+ content_base64sha512 = (known after apply)
+ content_md5 = (known after apply)
+ content_sha1 = (known after apply)
+ content_sha256 = (known after apply)
+ content_sha512 = (known after apply)
+ directory_permission = "0777"
+ file_permission = "0777"
+ filename = "/home/bob/terraform/EncryptedData.bin"
+ id = (known after apply)
}
Plan: 5 to add, 0 to change, 0 to destroy.
Changes to Outputs:
+ kke_kms_key_name = "alias/devops-kms-key"
────────────────────────────────────────────────────────────────────────────────
bob@iac-server ~/terraform via 💠 default ✖ terraform apply
Terraform used the selected providers to generate the following execution plan.
Resource actions are indicated with the following symbols:
+ create
<= read (data resources)
Terraform will perform the following actions:
# data.aws_kms_secrets.decrypted_data will be read during apply
# (config refers to values not yet known)
<= data "aws_kms_secrets" "decrypted_data" {
+ id = (known after apply)
+ plaintext = (sensitive value)
+ secret {
+ name = "decrypted"
+ payload = (known after apply)
}
}
# aws_kms_alias.alias will be created
+ resource "aws_kms_alias" "alias" {
+ arn = (known after apply)
+ id = (known after apply)
+ name = "alias/devops-kms-key"
+ name_prefix = (known after apply)
+ target_key_arn = (known after apply)
+ target_key_id = (known after apply)
}
# aws_kms_ciphertext.encrypted_data will be created
+ resource "aws_kms_ciphertext" "encrypted_data" {
+ ciphertext_blob = (known after apply)
+ id = (known after apply)
+ key_id = (known after apply)
+ plaintext = (sensitive value)
}
# aws_kms_key.devops-kms-key will be created
+ resource "aws_kms_key" "devops-kms-key" {
+ arn = (known after apply)
+ bypass_policy_lockout_safety_check = false
+ customer_master_key_spec = "SYMMETRIC_DEFAULT"
+ description = (known after apply)
+ enable_key_rotation = false
+ id = (known after apply)
+ is_enabled = true
+ key_id = (known after apply)
+ key_usage = "ENCRYPT_DECRYPT"
+ multi_region = (known after apply)
+ policy = (known after apply)
+ rotation_period_in_days = (known after apply)
+ tags = {
+ "Name" = "devops-kms-key"
}
+ tags_all = {
+ "Name" = "devops-kms-key"
}
}
# local_file.decrypted_file will be created
+ resource "local_file" "decrypted_file" {
+ content = (sensitive value)
+ content_base64sha256 = (known after apply)
+ content_base64sha512 = (known after apply)
+ content_md5 = (known after apply)
+ content_sha1 = (known after apply)
+ content_sha256 = (known after apply)
+ content_sha512 = (known after apply)
+ directory_permission = "0777"
+ file_permission = "0777"
+ filename = "/home/bob/terraform/DecryptedData.txt"
+ id = (known after apply)
}
# local_file.encrypted_file will be created
+ resource "local_file" "encrypted_file" {
+ content = (known after apply)
+ content_base64sha256 = (known after apply)
+ content_base64sha512 = (known after apply)
+ content_md5 = (known after apply)
+ content_sha1 = (known after apply)
+ content_sha256 = (known after apply)
+ content_sha512 = (known after apply)
+ directory_permission = "0777"
+ file_permission = "0777"
+ filename = "/home/bob/terraform/EncryptedData.bin"
+ id = (known after apply)
}
Plan: 5 to add, 0 to change, 0 to destroy.
Changes to Outputs:
+ kke_kms_key_name = "alias/devops-kms-key"
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_kms_key.devops-kms-key: Creating...
aws_kms_key.devops-kms-key: Creation complete after 4s [id=02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5]
aws_kms_ciphertext.encrypted_data: Creating...
aws_kms_alias.alias: Creating...
aws_kms_alias.alias: Creation complete after 0s [id=alias/devops-kms-key]
aws_kms_ciphertext.encrypted_data: Creation complete after 0s [id=2025-11-01 06:18:35.37190183 +0000 UTC]
data.aws_kms_secrets.decrypted_data: Reading...
data.aws_kms_secrets.decrypted_data: Read complete after 0s [id=us-east-1]
local_file.encrypted_file: Creating...
local_file.encrypted_file: Creation complete after 0s [id=42d2d1007660cc5788bbfb529d29c4ab3362018d]
local_file.decrypted_file: Creating...
local_file.decrypted_file: Creation complete after 0s [id=33629e1969e087f33d261aa7324ea8f4b5507821]
Apply complete! Resources: 5 added, 0 changed, 0 destroyed.
Outputs:
kke_kms_key_name = "alias/devops-kms-key"
bob@iac-server ~/terraform via 💠 default ➜ cat DecryptedData.txt
This is a sensitive file.
bob@iac-server ~/terraform via 💠 default ➜ cat EncryptedData.bin
MDJhZDllM2UtMjMzNS00ZTBlLWIzN2YtZTVlYTBlY2U3Y2M1Wc/z8830qp7fa6wELoPiI1iBX3J5CNa6QQMyeFxgsuApUx4/5UPqW2Wf5cBS3tLPhuAruLNNwM0taUFnoStQsw==
bob@iac-server ~/terraform via 💠 default ➜ cat SensitiveData.txt
This is a sensitive file.
bob@iac-server ~/terraform via 💠 default ➜ cat terraform.tfstate
{
"version": 4,
"terraform_version": "1.11.0",
"serial": 7,
"lineage": "1d3d0666-0948-00e9-dfaf-8979fcce5c3c",
"outputs": {
"kke_kms_key_name": {
"value": "alias/devops-kms-key",
"type": "string"
}
},
"resources": [
{
"mode": "data",
"type": "aws_kms_secrets",
"name": "decrypted_data",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"id": "us-east-1",
"plaintext": {
"decrypted": "This is a sensitive file."
},
"secret": [
{
"context": {},
"encryption_algorithm": "",
"grant_tokens": [],
"key_id": "",
"name": "decrypted",
"payload": "MDJhZDllM2UtMjMzNS00ZTBlLWIzN2YtZTVlYTBlY2U3Y2M1Wc/z8830qp7fa6wELoPiI1iBX3J5CNa6QQMyeFxgsuApUx4/5UPqW2Wf5cBS3tLPhuAruLNNwM0taUFnoStQsw=="
}
]
},
"sensitive_attributes": [
[
{
"type": "get_attr",
"value": "plaintext"
}
]
]
}
]
},
{
"mode": "managed",
"type": "aws_kms_alias",
"name": "alias",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"arn": "arn:aws:kms:us-east-1:000000000000:alias/devops-kms-key",
"id": "alias/devops-kms-key",
"name": "alias/devops-kms-key",
"name_prefix": "",
"target_key_arn": "arn:aws:kms:us-east-1:000000000000:key/02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5",
"target_key_id": "02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5"
},
"sensitive_attributes": [],
"private": "bnVsbA==",
"dependencies": [
"aws_kms_key.devops-kms-key"
]
}
]
},
{
"mode": "managed",
"type": "aws_kms_ciphertext",
"name": "encrypted_data",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"ciphertext_blob": "MDJhZDllM2UtMjMzNS00ZTBlLWIzN2YtZTVlYTBlY2U3Y2M1Wc/z8830qp7fa6wELoPiI1iBX3J5CNa6QQMyeFxgsuApUx4/5UPqW2Wf5cBS3tLPhuAruLNNwM0taUFnoStQsw==",
"context": null,
"id": "2025-11-01 06:18:35.37190183 +0000 UTC",
"key_id": "arn:aws:kms:us-east-1:000000000000:key/02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5",
"plaintext": "This is a sensitive file."
},
"sensitive_attributes": [
[
{
"type": "get_attr",
"value": "plaintext"
}
]
],
"private": "bnVsbA==",
"dependencies": [
"aws_kms_key.devops-kms-key"
]
}
]
},
{
"mode": "managed",
"type": "aws_kms_key",
"name": "devops-kms-key",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"arn": "arn:aws:kms:us-east-1:000000000000:key/02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5",
"bypass_policy_lockout_safety_check": false,
"custom_key_store_id": "",
"customer_master_key_spec": "SYMMETRIC_DEFAULT",
"deletion_window_in_days": null,
"description": "",
"enable_key_rotation": false,
"id": "02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5",
"is_enabled": true,
"key_id": "02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5",
"key_usage": "ENCRYPT_DECRYPT",
"multi_region": false,
"policy": "{\"Id\":\"key-default-1\",\"Statement\":[{\"Action\":\"kms:*\",\"Effect\":\"Allow\",\"Principal\":{\"AWS\":\"arn:aws:iam::000000000000:root\"},\"Resource\":\"*\",\"Sid\":\"Enable IAM User Permissions\"}],\"Version\":\"2012-10-17\"}",
"rotation_period_in_days": 0,
"tags": {
"Name": "devops-kms-key"
},
"tags_all": {
"Name": "devops-kms-key"
},
"timeouts": null,
"xks_key_id": ""
},
"sensitive_attributes": [],
"private": "eyJlMmJmYjczMC1lY2FhLTExZTYtOGY4OC0zNDM2M2JjN2M0YzAiOnsiY3JlYXRlIjoxMjAwMDAwMDAwMDB9fQ=="
}
]
},
{
"mode": "managed",
"type": "local_file",
"name": "decrypted_file",
"provider": "provider[\"registry.terraform.io/hashicorp/local\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"content": "This is a sensitive file.",
"content_base64": null,
"content_base64sha256": "v/KmeQqMArGTSFTMAZERJYZuKezDN2kwKDPKrDhEpgk=",
"content_base64sha512": "wGn5IGMHscwyqgjwvy11t+0Apr8jMw25uQB1bgT4bEc70/cDbKSfltAwhXdsXUEVlvE/7q1Cdry4P/TlAfvLrA==",
"content_md5": "fb78248c0fdf1e8cc7d9b81af2423b16",
"content_sha1": "33629e1969e087f33d261aa7324ea8f4b5507821",
"content_sha256": "bff2a6790a8c02b1934854cc01911125866e29ecc33769302833caac3844a609",
"content_sha512": "c069f9206307b1cc32aa08f0bf2d75b7ed00a6bf23330db9b900756e04f86c473bd3f7036ca49f96d03085776c5d411596f13feead4276bcb83ff4e501fbcbac",
"directory_permission": "0777",
"file_permission": "0777",
"filename": "/home/bob/terraform/DecryptedData.txt",
"id": "33629e1969e087f33d261aa7324ea8f4b5507821",
"sensitive_content": null,
"source": null
},
"sensitive_attributes": [
[
{
"type": "get_attr",
"value": "sensitive_content"
}
],
[
{
"type": "get_attr",
"value": "content"
}
]
],
"dependencies": [
"aws_kms_ciphertext.encrypted_data",
"aws_kms_key.devops-kms-key",
"data.aws_kms_secrets.decrypted_data"
]
}
]
},
{
"mode": "managed",
"type": "local_file",
"name": "encrypted_file",
"provider": "provider[\"registry.terraform.io/hashicorp/local\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"content": "MDJhZDllM2UtMjMzNS00ZTBlLWIzN2YtZTVlYTBlY2U3Y2M1Wc/z8830qp7fa6wELoPiI1iBX3J5CNa6QQMyeFxgsuApUx4/5UPqW2Wf5cBS3tLPhuAruLNNwM0taUFnoStQsw==",
"content_base64": null,
"content_base64sha256": "fgpQSvUoel1Skou1Ln+OGjCPKe3I9OZ6ncBzaNbgxug=",
"content_base64sha512": "0s1i2pQjr2KP82iYFfWmFZ+O5QREQqj7ewQx4GVAoJ0MMDIYge2+o8YdtMwLAVtyBWD8gotLm49PFyc4GOx3nA==",
"content_md5": "c0542f8c1dc8d85bc45b7b9629ca047e",
"content_sha1": "42d2d1007660cc5788bbfb529d29c4ab3362018d",
"content_sha256": "7e0a504af5287a5d52928bb52e7f8e1a308f29edc8f4e67a9dc07368d6e0c6e8",
"content_sha512": "d2cd62da9423af628ff3689815f5a6159f8ee5044442a8fb7b0431e06540a09d0c30321881edbea3c61db4cc0b015b720560fc828b4b9b8f4f17273818ec779c",
"directory_permission": "0777",
"file_permission": "0777",
"filename": "/home/bob/terraform/EncryptedData.bin",
"id": "42d2d1007660cc5788bbfb529d29c4ab3362018d",
"sensitive_content": null,
"source": null
},
"sensitive_attributes": [
[
{
"type": "get_attr",
"value": "sensitive_content"
}
]
],
"dependencies": [
"aws_kms_ciphertext.encrypted_data",
"aws_kms_key.devops-kms-key"
]
}
]
}
],
"check_results": null
}
bob@iac-server ~/terraform via 💠 default ➜ terraform apply
aws_kms_key.devops-kms-key: Refreshing state... [id=02ad9e3e-2335-4e0e-b37f-e5ea0ece7cc5]
aws_kms_ciphertext.encrypted_data: Refreshing state... [id=2025-11-01 06:18:35.37190183 +0000 UTC]
aws_kms_alias.alias: Refreshing state... [id=alias/devops-kms-key]
data.aws_kms_secrets.decrypted_data: Reading...
local_file.encrypted_file: Refreshing state... [id=42d2d1007660cc5788bbfb529d29c4ab3362018d]
data.aws_kms_secrets.decrypted_data: Read complete after 0s [id=us-east-1]
local_file.decrypted_file: Refreshing state... [id=33629e1969e087f33d261aa7324ea8f4b5507821]
No changes. Your infrastructure matches the configuration.
Terraform has compared your real infrastructure against your configuration and found no
differences, so no changes are needed.
Apply complete! Resources: 0 added, 0 changed, 0 destroyed.
Outputs:
kke_kms_key_name = "alias/devops-kms-key"
bob@iac-server ~/terraform via 💠 default ➜
bob@iac-server ~/terraform via 💠 default ➜
resource "aws_kms_key" "devops-kms-key" {
key_usage = "ENCRYPT_DECRYPT"
customer_master_key_spec = "SYMMETRIC_DEFAULT"
tags = {
Name = "devops-kms-key"
}
}
resource "aws_kms_alias" "alias" {
name = "alias/devops-kms-key"
target_key_id = aws_kms_key.devops-kms-key.id
}
locals {
sensitive_file_path = "/home/bob/terraform/SensitiveData.txt"
sensitive_plaintext = file(local.sensitive_file_path)
}
resource "aws_kms_ciphertext" "encrypted_data" {
key_id = aws_kms_key.devops-kms-key.arn
plaintext = local.sensitive_plaintext
}
resource "local_file" "encrypted_file" {
filename = "/home/bob/terraform/EncryptedData.bin"
content = resource.aws_kms_ciphertext.encrypted_data.ciphertext_blob
}
data "aws_kms_secrets" "decrypted_data" {
secret {
name = "decrypted"
payload = resource.aws_kms_ciphertext.encrypted_data.ciphertext_blob
}
}
resource "local_file" "decrypted_file" {
filename = "/home/bob/terraform/DecryptedData.txt"
content = data.aws_kms_secrets.decrypted_data.plaintext["decrypted"]
}
output "kke_kms_key_name" {
description = "Name of the KMS key created"
value = aws_kms_alias.alias.name
}