Dear team,
I recently completed the “Implementing Encryption at Rest with AWS KMS Using Terraform” task, but it was marked as failed due to the output “KKE Kms key Missing or incorrect”. I cross checked and tried multiple times with different output values like aws_kms_key.nautilus_kms_key.key_id or aws_kms_key.nautilus_kms_key.name. I belive everything was executed correctly. The KMS was created, Attached Screenshot for reference. Kindly review and let me know if there’s anything I may have missed.
Regards
Tamizh
Hi @tamilzhnationalist
Please share the course name and level.
Course name: kodekloud engineer practice
Level: Terraform level3
Task name: Implementing Encryption at Rest with AWS KMS Using Terraform
1 Like
Hi @tamilzhnationalist
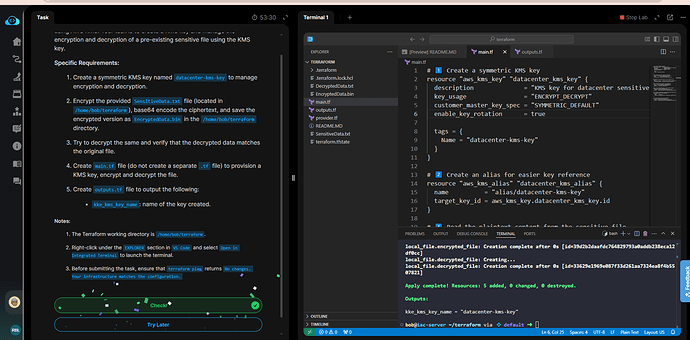
It’s working fine on my end. Please refer to the Terraform files below and try again.
main.tf
# 1️⃣ Create a symmetric KMS key
resource "aws_kms_key" "datacenter_kms_key" {
description = "KMS key for datacenter sensitive data encryption"
key_usage = "ENCRYPT_DECRYPT"
customer_master_key_spec = "SYMMETRIC_DEFAULT"
enable_key_rotation = true
tags = {
Name = "datacenter-kms-key"
}
}
# 2️⃣ Create an alias for easier key reference
resource "aws_kms_alias" "datacenter_kms_alias" {
name = "alias/datacenter-kms-key"
target_key_id = aws_kms_key.datacenter_kms_key.id
}
# 3️⃣ Read the plaintext content from the sensitive file
locals {
sensitive_file_path = "/home/bob/terraform/SensitiveData.txt"
sensitive_plaintext = file(local.sensitive_file_path)
}
# 4️⃣ Encrypt the file content using the KMS key
resource "aws_kms_ciphertext" "encrypted_data" {
key_id = aws_kms_key.datacenter_kms_key.arn
plaintext = local.sensitive_plaintext
}
# 5️⃣ Save the encrypted data to a file (base64 encoded)
resource "local_file" "encrypted_file" {
filename = "/home/bob/terraform/EncryptedData.bin"
content = aws_kms_ciphertext.encrypted_data.ciphertext_blob
}
# 6️⃣ Decrypt the ciphertext using aws_kms_secrets data source
data "aws_kms_secrets" "decrypted_data" {
secret {
name = "decrypted"
payload = aws_kms_ciphertext.encrypted_data.ciphertext_blob
}
}
# 7️⃣ Save decrypted data for verification
resource "local_file" "decrypted_file" {
filename = "/home/bob/terraform/DecryptedData.txt"
content = data.aws_kms_secrets.decrypted_data.plaintext["decrypted"]
}
outputs.tf
output "kke_kms_key_name" {
description = "Name tag of the KMS key created"
value = aws_kms_key.datacenter_kms_key.tags["Name"]
}
1 Like