For the question below:
We have created a service account called green-sa-cka22-arch , a cluster role called green-role-cka22-arch and a cluster role binding called green-role-binding-cka22-arch .
Update the permissions of this service account so that it can only get all the namespaces in cluster1 .
I modified the resource to "namespaces and in the role green-role-cka22-arch I even recreated the role binding but still I ma getting a “no” when testing permissions.
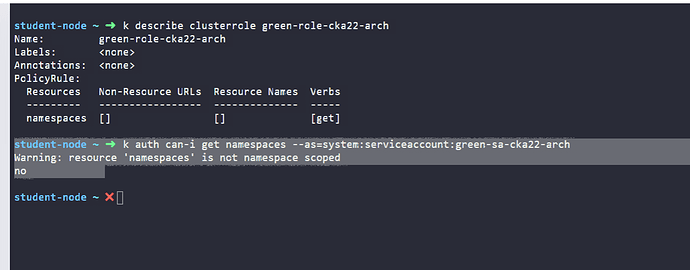
student-node ~ ➜ k auth can-i get namespaces --as=system:serviceaccount:green-sa-cka22-arch
Warning: resource ‘namespaces’ is not namespace scoped
no
student-node ~ ➜ k describe clusterrole green-role-cka22-arch
Name: green-role-cka22-arch
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
namespaces [] [] [get]
k auth can-i get namespaces --as system:serviceaccount:default:green-sa-cka22-arch
Your error appears to be not the role edit, but how you put the SA name in the k auth command
-
system:serviceaccount:green-sa-cka22-arch 
-
system:serviceaccount:default:green-sa-cka22-arch 
Format is system:serviceaccount:<namespace>:<sa-name> where <namespace> is the namespace where the SA is created.
1 Like