When creating role for instance profile. KKlab user does not have IAM policy to put role policy to the role.
The task can’t be finished without that permission.
What commands were you using? I was able to associate the role with the instance without getting this error.
Hi @Alistair_KodeKloud ,
Thanks for the reply
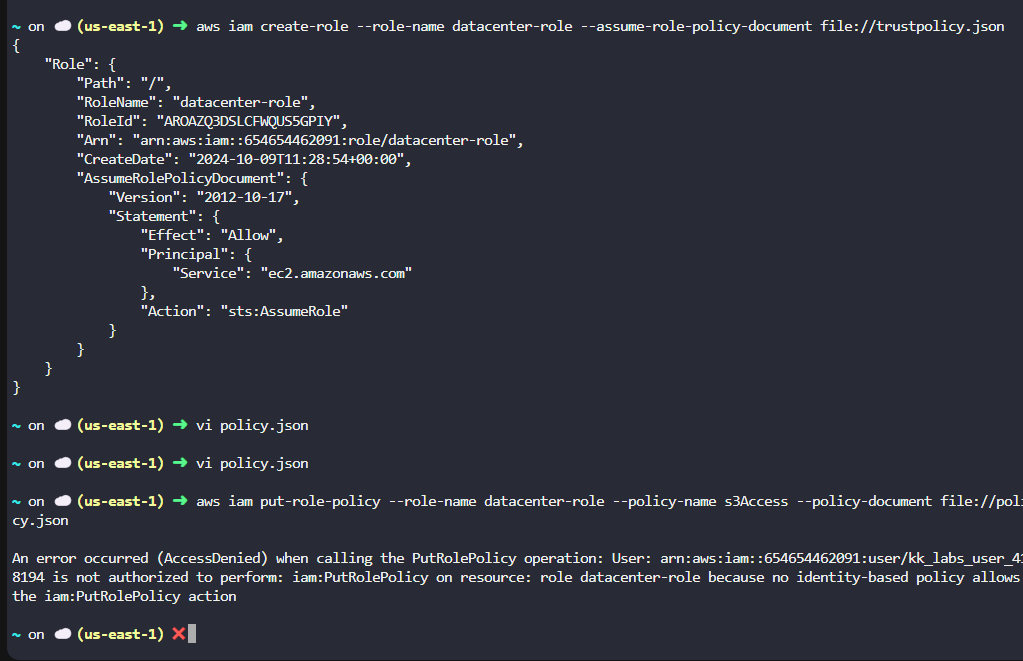
I was following AWS documentation to create a role with the cli.
First, I was able to issue a command like:
aws iam create-role --role-name Test-Role-for-EC2 --assume-role-policy-document file://C:\policies\trustpolicyforec2.json. So I was able to create a role.
But I wanted to put a policy to that role with something like this:
aws iam put-role-policy --role-name Test-Role-for-EC2 --policy-name Permissions-Policy-For-Ec2 --policy-document file://C:\policies\permissionspolicyforec2.json
And it is returning: UserkK.labs has not resources based policy attached that allows PutRolePolicy.
My concern is that it might be working sometimes but some other times are not.
Thanks very much again.
In my case this is the policy.json
{
“Statement”: [
{
“Effect”: “Allow”,
“Principal”: “",
“Action”: [“s3:GetObject”,“s3:PutObject”,“s3:ListBuckets”],
“Resource”: ["arn:aws:s3:::datacenter-s3-30063/”,“arn:aws:s3:::datacenter-s3-30063”]
}
]
}
An error occurred (AccessDenied) when calling the PutRolePolicy operation: User: arn:aws:iam::654654462091:user/kk_labs_user_418194 is not authorized to perform: iam:PutRolePolicy on resource: role datacenter-role because no identity-based policy allows the iam:PutRolePolicy action
The task explicitly mentions that we should put this policy to that role and then attach that role as the instance profile.
Even if I do it with the console I get the same error
Since PutRolePolicy isn’t allowed, you need to add the policy at the time of role creation. The aws cli doesn’t have support for adding anything other than the trust policy, therefore you’re going to need to do it in the AWS console where you can define the permissions as you create the role.
Hi @Alistair_KodeKloud ,
I think i found the issue. I was able to run with the CLI attachRolePolicy API and it worked fine.
I looked for the difference and it lays on the fact that PutRolePolicy attaches an Inline policy.
What I did was,
- Create the policy with aws iam create policy
2.Attach it with aws iam attach role policy - Create instance profile
- Associate role with instance
I was able to solve the issue.
I think AWS API is still a bit confusing haha
Thanks for taking the time.
KR