export rg=‘kml_rg_main-e84951e0e1554797’
export vname=‘datacenter-25586’
export kname=‘datacenter-key’
az keyvault key decrypt --vault-name “$vname” --name “$kname” --algorithm RSA-OAEP --data-type plaintext --value “$(cat /root/EncryptedData.bin)” | jq -r ‘.result’ | base64 --decode > /root/DecryptedData.txt
While executing above command, I am getting below Error.
ERROR: (Forbidden) Caller is not authorized to perform action on resource.
…
“code”: “ForbiddenByRbac”
More to that KK Labs were not allow to Assign Required Role to the Caller
Let me know how to resolve this issue.
Hi @suryaeshwaran
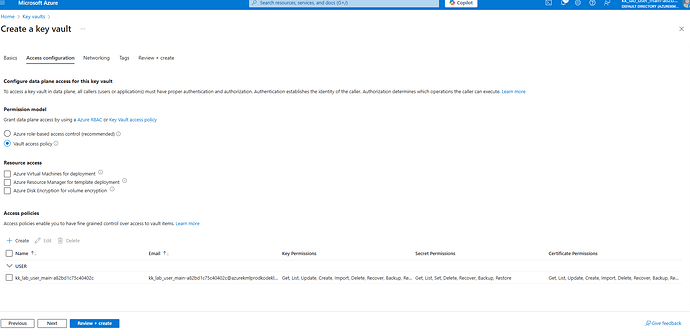
You created the Key Vault but didn’t set up the access policies. That’s why you couldn’t create a Key Vault key.
After enabling the Access policy and giving principle.
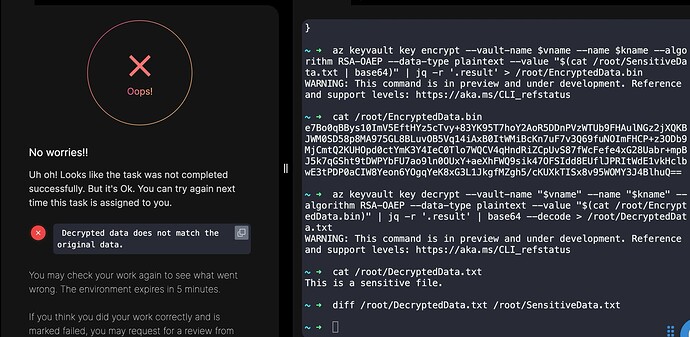
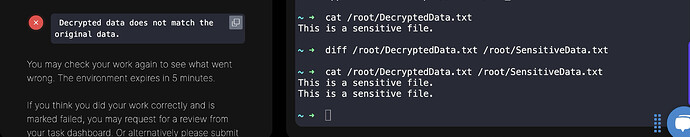
While running the Validation getting exception, Even though there is no difference in the files.
I don’t see any issues with your commands either. Let me check and I’ll keep you updated.
Hi @suryaeshwaran,
It’s worked properly from my end, please try again and let me know if it persists.
Hi @raymond.baoly
Have tried again, it still fail here…
That’s strange, I don’t see any issue with your CLI either. How did you create the Key Vault and the key?
Here are the commands:
export rg=‘kml_rg_main-23217082424b48ff’
export vname=‘devops-26914’
export kname=‘devops-key’
- Create a Key Vault
az keyvault create --name $vname --resource-group $rg --location eastus --sku Standard --retention-days 7 --public-network-access Enabled --enable-rbac-authorization false
1.2 Add Access Policy On Console
“createdBy”: “1b49c611-f96c-423b-ad21-745bbf902813”
- Create Symmetric Key
az keyvault key create --vault-name $vname --name $kname --kty RSA --size 2048 --ops encrypt decrypt
1 Like
Hi @suryaeshwaran,
I’m still unable to replicate the issue on my end and don’t notice any errors in your code. Could you please try again? I’m not sure this is an ongoing problem.
Hi Team,
Have tried again still validation give failure.
Hi @suryaeshwaran,
Sorry for the trouble. Could you please record a video showing the issue? It looks like it might only be happening with your account.
Hi @raymond.baoly
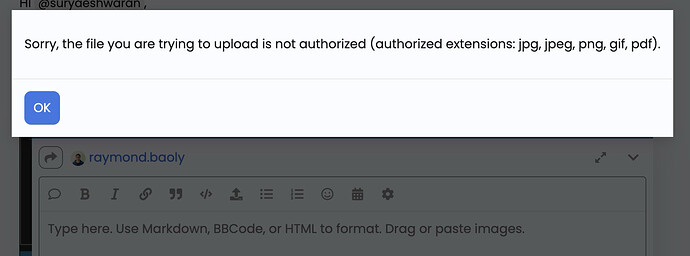
I have recorded the video but not able to share in this portal since only photos/pdf were allowed. Please advice.
Hi @suryaeshwaran,
Have you tried to used this button?
Yes i tried, this is how it shows.
Hi @suryaeshwaran,
In this case, please use the Feedback button and include a screenshot. After that, you’ll receive a response email with a Userback link, then send me that link via DM.
Hi @suryaeshwaran,
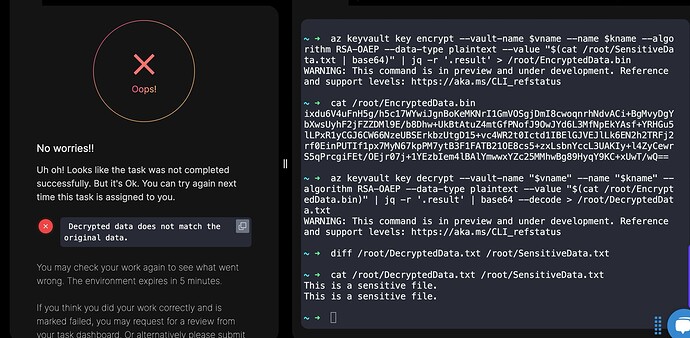
I noticed there’s a small difference between my command and yours. Could you please try the command below? It worked for me and helped me complete the task.
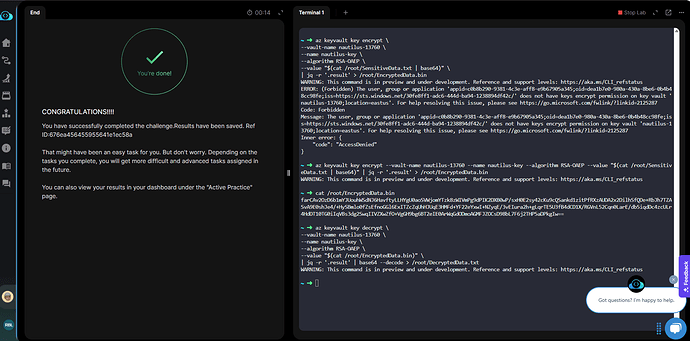
Encrypt the file using Azure Key Vault
az keyvault key encrypt
–vault-name nautilus-13760
–name nautilus-key
–algorithm RSA-OAEP
–value “$(cat /root/SensitiveData.txt | base64)”
| jq -r ‘.result’ > /root/EncryptedData.bin
Verify encrypted data
cat /root/EncryptedData.bin
Decrypt the file using Azure Key Vault
az keyvault key decrypt
–vault-name nautilus-13760
–name nautilus-key
–algorithm RSA-OAEP
–value “$(cat /root/EncryptedData.bin)”
| jq -r ‘.result’ | base64 --decode > /root/DecryptedData.txt
1 Like
Hi Raymond,
After removing –data-type plaintext tag able to complete the task successfully.
Thank you very much for your support 
1 Like
Glad to hear that! I’ll look into this further and let the team know if the validation needs to be updated.