This is related to the Namespace-Based Isolation with Kubernetes Network Policies 2/3
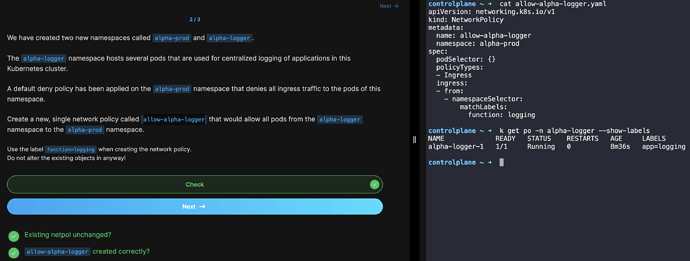
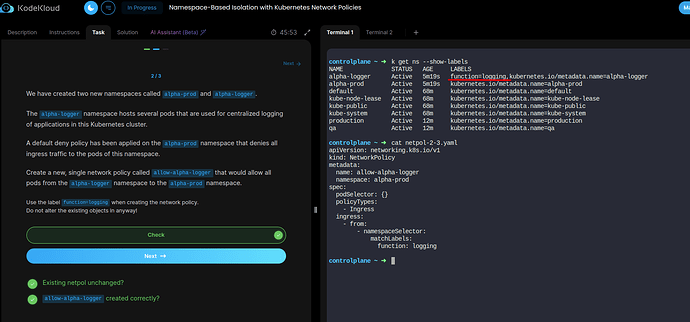
of Learn-By-Doing Kubernetes Network Policies course. It is advised to use the label function=logging for the namespaceSelector but the pod in the alpha-logger namespace has label app=logging.
The screenshot shows that all tasks have been met BUT before modifying my yaml file, the matchLabels was set to app: logging and allow-alpha-logger created correctly? failed.
Obviously this is not that big of a deal but I wanted to bring this up.
Thanks,
Liz
Hi @ewiklund
The question asks to allow all pods from the alpha-logger namespace to the alpha-prod namespace. In such scenarios when asked to allow traffic from the particular namespace, it means to us the namespaceSelector with label function=logging available for the alpha-logger namespace.
Of course, you currently have one pod labeled app=logging, but what if new pods with different labels come up in that namespace? That would deny traffic from any other Pods that do not have app=logging as the label.
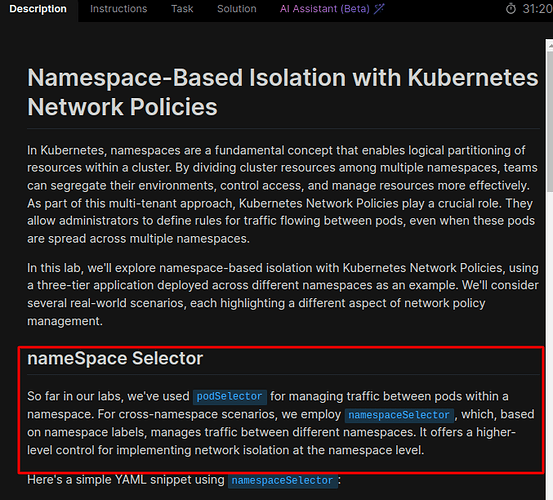
PS: Please take a look at the the description tab highlighting uses of namespaceSelector in cross-namespace scenarios:
Regards
Ok. Fair enough. Thanks Santosh.
1 Like