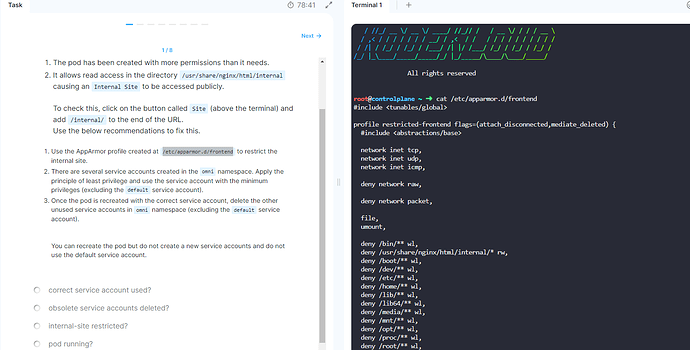
Lab 1 question 1 for apparmo: security context doesn’t work if defined in container .
The solution says to use in annotations , but the kubernetes.io say to use in container/pod definition spec. but is i define in container spec it doesn’t work
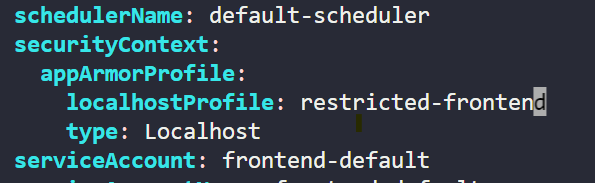
Snapshot attached for reference.
Is it due to change in version .?
I assume you actually mean Q12 of this lab; if you don’t, then I need a link to where you mean.
If so: then you need to check the name of the apparmor profile. I do it like this:
root@controlplane ~ ✦ ✖ head /etc/apparmor.d/usr.sbin.nginx-updated
#include <tunables/global>
profile restricted-nginx flags=(attach_disconnected,mediate_deleted) {
#include <abstractions/base>
network inet tcp,
network inet udp,
network inet icmp,
deny network raw,
So the correct profile name is restricted-nginx.
This is the question i am referring to , for this how do you define the apparmor profile in container? i used the correct name as defined in profile , but it doesn’t seem to work .
and the solution says to use in annotation as below :
annotations:
container.apparmor.security.beta.kubernetes.io/nginx: localhost/restricted-frontend #Apply profile ‘restricted-fronend’ on ‘nginx’ container:
but i use it as defined in container as per k8s docs which doesn’t work (snapshot attache d above)
A picture of the lab is very nice, but I can’t click on it and get to your lab  So, a link please.
So, a link please.
In my opinion, the lab’s solution for Q1/8 is wrong, since the annotation is no longer the way to specify it; the feature is now beta and therefore active by default, and you now specify the apparmor profile in regular yaml, as you did above.
The grader, however, accepts your answer, so the grader is fine; it’s the solution that’s wrong.