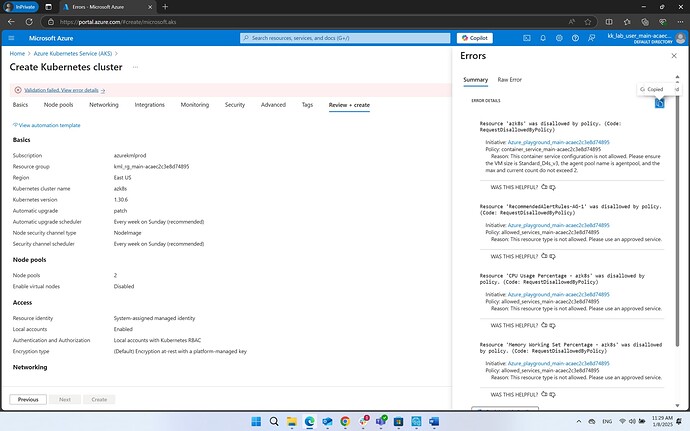
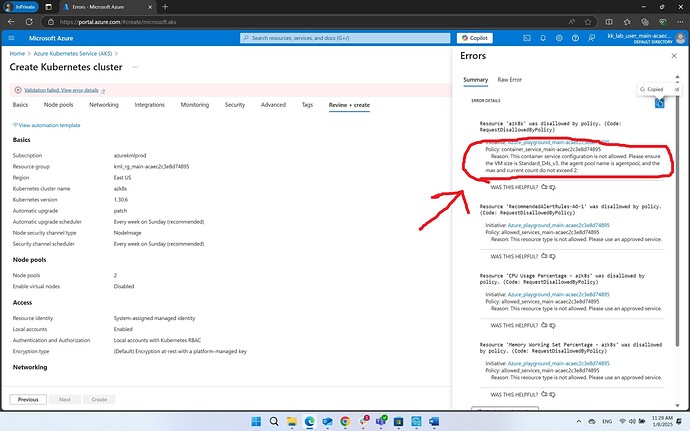
Dear team I am trying to create a k8s cluster on azure playground. Each time I see this error
{“code”:“InvalidTemplateDeployment”,“details”:[{“code”:“RequestDisallowedByPolicy”,“target”:“azk8s”,“message”:“Resource ‘azk8s’ was disallowed by policy. Reasons: ‘This container service configuration is not allowed. Please ensure the VM size is Standard_D4s_v3, the agent pool name is agentpool, and the max and current count do not exceed 2.’. See error details for policy resource IDs.”,“additionalInfo”:[{“type”:“PolicyViolation”,“info”:{“evaluationDetails”:{“evaluatedExpressions”:[{“result”:“True”,“expressionKind”:“Field”,“expression”:“type”,“path”:“type”,“expressionValue”:“Microsoft.ContainerService/managedClusters”,“targetValue”:“Microsoft.ContainerService/managedClusters”,“operator”:“Equals”},{“result”:“False”,“expressionKind”:“Field”,“expression”:“Microsoft.ContainerService/managedClusters/agentPoolProfiles[].vmSize",“path”:"properties.agentPoolProfiles[].vmSize”,“expressionValue”:[“Standard_D8ds_v5”,“Standard_D4s_v3”],“targetValue”:[“Standard_D4s_v3”],“operator”:“In”}],“reason”:“This container service configuration is not allowed. Please ensure the VM size is Standard_D4s_v3, the agent pool name is agentpool, and the max and current count do not exceed 2.”},“policyDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policyDefinitions/container_service_main-acaec2c3e8d74895”,“policySetDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policySetDefinitions/Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionReferenceId”:“container_service_main-acaec2c3e8d74895_ref”,“policySetDefinitionName”:“Azure_playground_main-acaec2c3e8d74895”,“policySetDefinitionDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionName”:“container_service_main-acaec2c3e8d74895”,“policyDefinitionDisplayName”:“container_service_main-acaec2c3e8d74895”,“policyDefinitionEffect”:“deny”,“policyAssignmentId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895/providers/Microsoft.Authorization/policyAssignments/Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentScope”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895”,“policyAssignmentParameters”:{},“policyExemptionIds”:[]}}]},{“code”:“RequestDisallowedByPolicy”,“target”:“RecommendedAlertRules-AG-1”,“message”:“Resource ‘RecommendedAlertRules-AG-1’ was disallowed by policy. Reasons: ‘This resource type is not allowed. Please use an approved service.’. See error details for policy resource IDs.”,“additionalInfo”:[{“type”:“PolicyViolation”,“info”:{“evaluationDetails”:{“evaluatedExpressions”:[{“result”:“False”,“expressionKind”:“Field”,“expression”:“type”,“path”:“type”,“expressionValue”:“microsoft.insights/actionGroups”,“targetValue”:[“Microsoft.Compute/virtualMachines”,“Microsoft.Compute/virtualMachineScaleSets”,“Microsoft.Compute/availabilitySets”,“Microsoft.Compute/disks”,“Microsoft.Compute/sshPublicKeys”,“Microsoft.Compute/virtualMachines/extensions”,“Microsoft.Storage”,“Microsoft.Storage/storageAccounts”,“Microsoft.Network/networkInterfaces”,“Microsoft.Network/networkSecurityGroups”,“Microsoft.Network/publicIPAddresses”,“Microsoft.Network/virtualNetworks”,“Microsoft.Network/privateEndpoints”,“Microsoft.Network/privateDnsZones”,“Microsoft.Network/privateDnsZones/virtualNetworkLinks”,“Microsoft.Network/loadBalancers”,“Microsoft.Network/routeTables”,“Microsoft.Network/applicationGateways”,“Microsoft.DocumentDB/databaseAccounts”,“Microsoft.Web/serverFarms”,“Microsoft.Web/sites”,“Microsoft.Sql/servers”,“Microsoft.Sql/servers/databases”,“Microsoft.ManagedIdentity/userAssignedIdentities”,“Microsoft.ContainerService/managedClusters”,“Microsoft.ContainerService/managedClusters/agentPools”,“Microsoft.DataLakeAnalytics/accounts”,“Microsoft.Synapse/workspaces”,“Microsoft.Logic/workflows”,“Microsoft.KeyVault/vaults”,“Microsoft.MachineLearningServices/workspaces”,“Microsoft.OperationalInsights/workspaces”,“Microsoft.SecurityInsights/workspaces”,“Microsoft.ContainerRegistry/registries”,“Microsoft.ContainerRegistry/registries/replications”,“Microsoft.ServiceBus/namespaces”,“Microsoft.EventHub/namespaces”],“operator”:“In”}],“reason”:“This resource type is not allowed. Please use an approved service.”},“policyDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policyDefinitions/allowed_services_main-acaec2c3e8d74895”,“policySetDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policySetDefinitions/Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionReferenceId”:“allowed_services_main-acaec2c3e8d74895_ref”,“policySetDefinitionName”:“Azure_playground_main-acaec2c3e8d74895”,“policySetDefinitionDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionDisplayName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionEffect”:“deny”,“policyAssignmentId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895/providers/Microsoft.Authorization/policyAssignments/Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentScope”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895”,“policyAssignmentParameters”:{},“policyExemptionIds”:[]}}]},{“code”:“RequestDisallowedByPolicy”,“target”:“CPU Usage Percentage - azk8s”,“message”:“Resource ‘CPU Usage Percentage - azk8s’ was disallowed by policy. Reasons: ‘This resource type is not allowed. Please use an approved service.’. See error details for policy resource IDs.”,“additionalInfo”:[{“type”:“PolicyViolation”,“info”:{“evaluationDetails”:{“evaluatedExpressions”:[{“result”:“False”,“expressionKind”:“Field”,“expression”:“type”,“path”:“type”,“expressionValue”:“microsoft.insights/metricAlerts”,“targetValue”:[“Microsoft.Compute/virtualMachines”,“Microsoft.Compute/virtualMachineScaleSets”,“Microsoft.Compute/availabilitySets”,“Microsoft.Compute/disks”,“Microsoft.Compute/sshPublicKeys”,“Microsoft.Compute/virtualMachines/extensions”,“Microsoft.Storage”,“Microsoft.Storage/storageAccounts”,“Microsoft.Network/networkInterfaces”,“Microsoft.Network/networkSecurityGroups”,“Microsoft.Network/publicIPAddresses”,“Microsoft.Network/virtualNetworks”,“Microsoft.Network/privateEndpoints”,“Microsoft.Network/privateDnsZones”,“Microsoft.Network/privateDnsZones/virtualNetworkLinks”,“Microsoft.Network/loadBalancers”,“Microsoft.Network/routeTables”,“Microsoft.Network/applicationGateways”,“Microsoft.DocumentDB/databaseAccounts”,“Microsoft.Web/serverFarms”,“Microsoft.Web/sites”,“Microsoft.Sql/servers”,“Microsoft.Sql/servers/databases”,“Microsoft.ManagedIdentity/userAssignedIdentities”,“Microsoft.ContainerService/managedClusters”,“Microsoft.ContainerService/managedClusters/agentPools”,“Microsoft.DataLakeAnalytics/accounts”,“Microsoft.Synapse/workspaces”,“Microsoft.Logic/workflows”,“Microsoft.KeyVault/vaults”,“Microsoft.MachineLearningServices/workspaces”,“Microsoft.OperationalInsights/workspaces”,“Microsoft.SecurityInsights/workspaces”,“Microsoft.ContainerRegistry/registries”,“Microsoft.ContainerRegistry/registries/replications”,“Microsoft.ServiceBus/namespaces”,“Microsoft.EventHub/namespaces”],“operator”:“In”}],“reason”:“This resource type is not allowed. Please use an approved service.”},“policyDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policyDefinitions/allowed_services_main-acaec2c3e8d74895”,“policySetDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policySetDefinitions/Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionReferenceId”:“allowed_services_main-acaec2c3e8d74895_ref”,“policySetDefinitionName”:“Azure_playground_main-acaec2c3e8d74895”,“policySetDefinitionDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionDisplayName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionEffect”:“deny”,“policyAssignmentId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895/providers/Microsoft.Authorization/policyAssignments/Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentScope”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895”,“policyAssignmentParameters”:{},“policyExemptionIds”:[]}}]},{“code”:“RequestDisallowedByPolicy”,“target”:“Memory Working Set Percentage - azk8s”,“message”:“Resource ‘Memory Working Set Percentage - azk8s’ was disallowed by policy. Reasons: ‘This resource type is not allowed. Please use an approved service.’. See error details for policy resource IDs.”,“additionalInfo”:[{“type”:“PolicyViolation”,“info”:{“evaluationDetails”:{“evaluatedExpressions”:[{“result”:“False”,“expressionKind”:“Field”,“expression”:“type”,“path”:“type”,“expressionValue”:“microsoft.insights/metricAlerts”,“targetValue”:[“Microsoft.Compute/virtualMachines”,“Microsoft.Compute/virtualMachineScaleSets”,“Microsoft.Compute/availabilitySets”,“Microsoft.Compute/disks”,“Microsoft.Compute/sshPublicKeys”,“Microsoft.Compute/virtualMachines/extensions”,“Microsoft.Storage”,“Microsoft.Storage/storageAccounts”,“Microsoft.Network/networkInterfaces”,“Microsoft.Network/networkSecurityGroups”,“Microsoft.Network/publicIPAddresses”,“Microsoft.Network/virtualNetworks”,“Microsoft.Network/privateEndpoints”,“Microsoft.Network/privateDnsZones”,“Microsoft.Network/privateDnsZones/virtualNetworkLinks”,“Microsoft.Network/loadBalancers”,“Microsoft.Network/routeTables”,“Microsoft.Network/applicationGateways”,“Microsoft.DocumentDB/databaseAccounts”,“Microsoft.Web/serverFarms”,“Microsoft.Web/sites”,“Microsoft.Sql/servers”,“Microsoft.Sql/servers/databases”,“Microsoft.ManagedIdentity/userAssignedIdentities”,“Microsoft.ContainerService/managedClusters”,“Microsoft.ContainerService/managedClusters/agentPools”,“Microsoft.DataLakeAnalytics/accounts”,“Microsoft.Synapse/workspaces”,“Microsoft.Logic/workflows”,“Microsoft.KeyVault/vaults”,“Microsoft.MachineLearningServices/workspaces”,“Microsoft.OperationalInsights/workspaces”,“Microsoft.SecurityInsights/workspaces”,“Microsoft.ContainerRegistry/registries”,“Microsoft.ContainerRegistry/registries/replications”,“Microsoft.ServiceBus/namespaces”,“Microsoft.EventHub/namespaces”],“operator”:“In”}],“reason”:“This resource type is not allowed. Please use an approved service.”},“policyDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policyDefinitions/allowed_services_main-acaec2c3e8d74895”,“policySetDefinitionId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/providers/Microsoft.Authorization/policySetDefinitions/Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionReferenceId”:“allowed_services_main-acaec2c3e8d74895_ref”,“policySetDefinitionName”:“Azure_playground_main-acaec2c3e8d74895”,“policySetDefinitionDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyDefinitionName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionDisplayName”:“allowed_services_main-acaec2c3e8d74895”,“policyDefinitionEffect”:“deny”,“policyAssignmentId”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895/providers/Microsoft.Authorization/policyAssignments/Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentDisplayName”:“Azure_playground_main-acaec2c3e8d74895”,“policyAssignmentScope”:“/subscriptions/a2b28c85-1948-4263-90ca-bade2bac4df4/resourceGroups/kml_rg_main-acaec2c3e8d74895”,“policyAssignmentParameters”:{},“policyExemptionIds”:[]}}]}],“message”:“The template deployment failed with multiple errors. Please see details for more information.”} Seems like my user don’t have access to create something.