Shwetha Shenoy:
Is it necessary to include groups: system:authenticated in the CSR request if the cert will be used by a user to access k8s cluster?
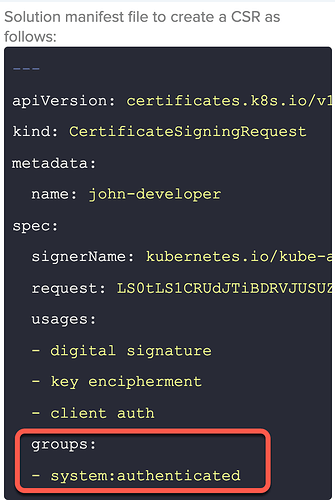
This is related to Q6 in Mock lab 2. ~My solution which didn’t include the system:authenticated group was marked incorrect.~
The reason it was marked incorrect was because i used a different name for the CSR and role, not because of the groups. ![]()
Shwetha Shenoy:
@unnivkn I followed this example in the docs which is also for a user accessing the cluster. But without the sys:authenticated group. ![]() https://kubernetes.io/docs/reference/access-authn-authz/certificate-signing-requests/#create-certificatesigningrequest
https://kubernetes.io/docs/reference/access-authn-authz/certificate-signing-requests/#create-certificatesigningrequest
Shwetha Shenoy:
Let me try creating a kubeconfig for this user (CSR signed without the sys:authenticated group in it) and access the cluster. I’ll let you know of my findings soon. ![]()
Shwetha Shenoy:
So, I added john to the kubeconfig, swtiched context to this user and was able to create, list pods in the development ns (role and rb created to limit john’s access to pods in development ns)
Shwetha Shenoy:
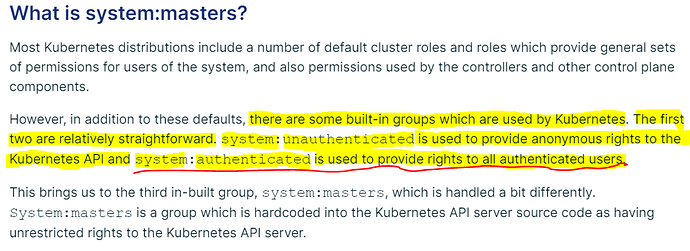
Additional finding, I didn’t add the system:authenticated group in the CSR. HOWEVER, the cert approval process added system:masters and system:authenticated groups on the CSR.
I see it when i output the yaml for CSR john.
unnivkn:
Okie… that means, if we skip, system:authenticated by default it will be added by k8s. Keep in mind, we can also categorize the users as, authorized, unauthorized, authorized+unauthorized etc, Thanks for bringing this up. Nice discussion @Shwetha Shenoy
RAJAN GARG:
Even, I faced the same issue. My answer was marked incorrect because I used different name for role and role-binding.
Shwetha Shenoy:
Yes, read the question fully before answering it. Important during the exams too to avoid losing points unnecessarily. ![]()