Shakti:
In a pod, if no securityContext is mentioned then what is the default value of AllowPrivilegeEscalation?
Shakti:
Thanks for respoding. I already saw that page but the thing what I didn’t understand is, for the below sample podspec, if the yaml is immutable or stateful.
Shakti:
spec:
containers:
- name: sec-ctx-demo
image: nginx:1.28
Shakti:
In the above podspec no user is provided so the user inside the container will be root. So that means, this podspec is also privieged.
Am I correct?
In the similar lines, if I am not providing any allowPrivilegeEscalation, the default is tru. so for the below yaml is also not a good yaml from, immutablity and stateful
spec:
containers:
- name: sec-ctx-demo
image: nginx:3.38
securityContext:
readOnlyRootFilesystem: true
unnivkn:
In the above podspec no user is provided so the user inside the container will be root. So that means, this podspec is also privieged.
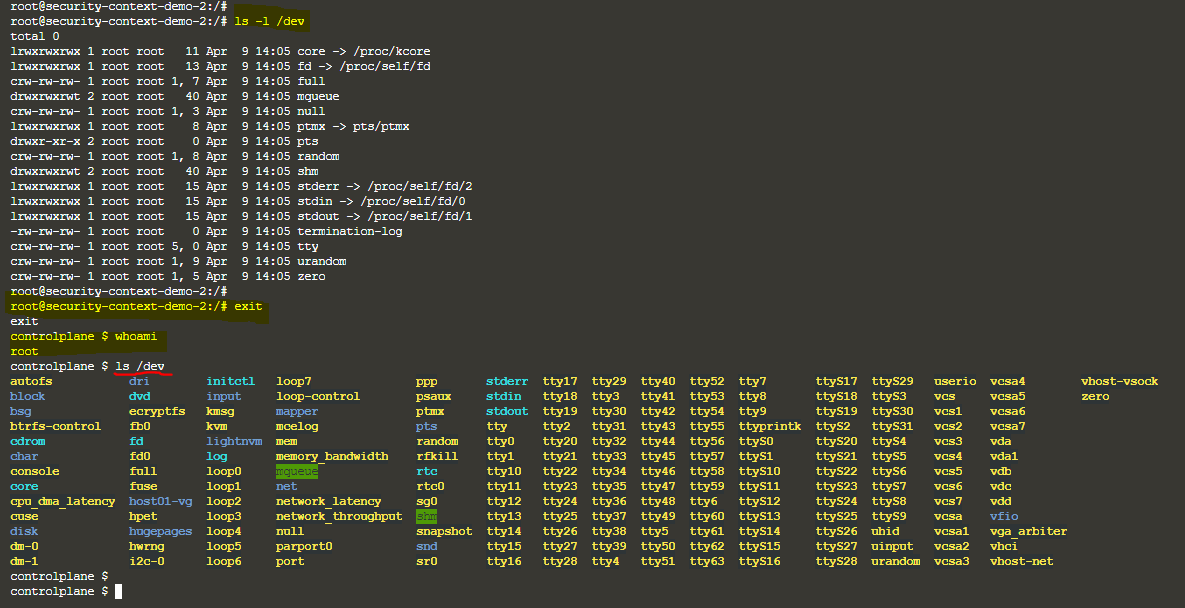
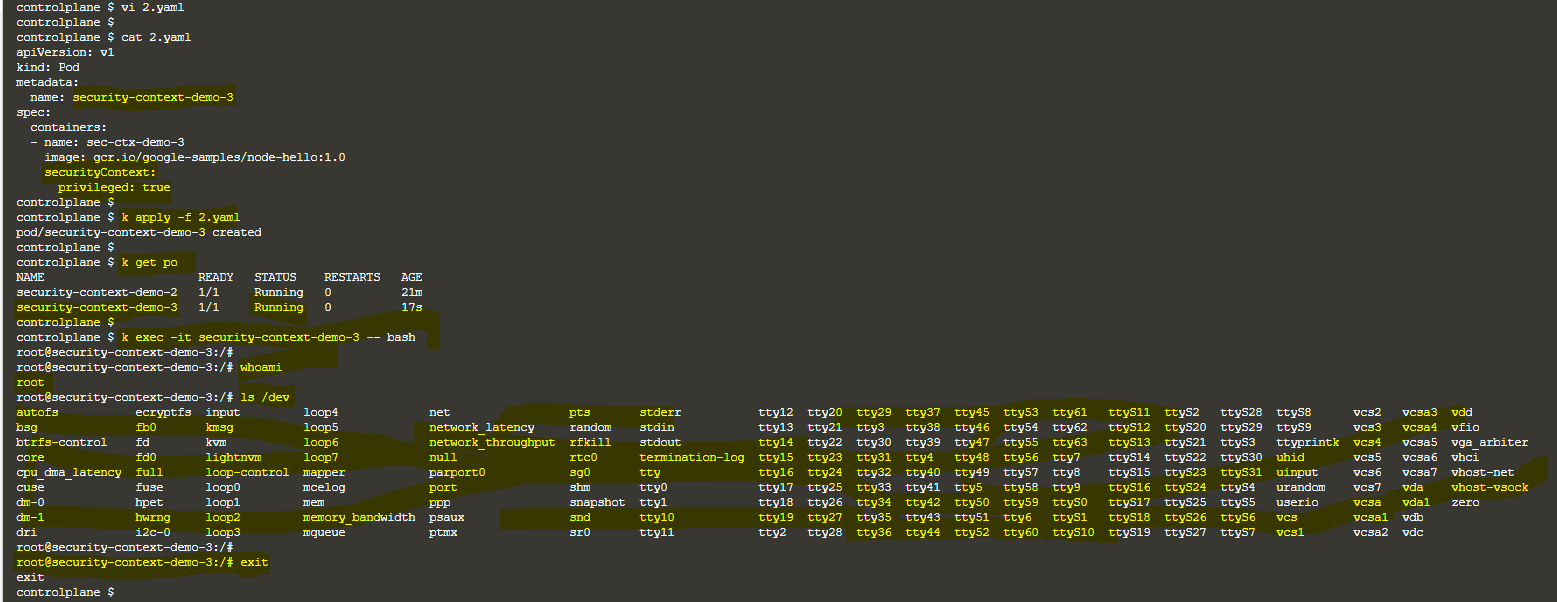
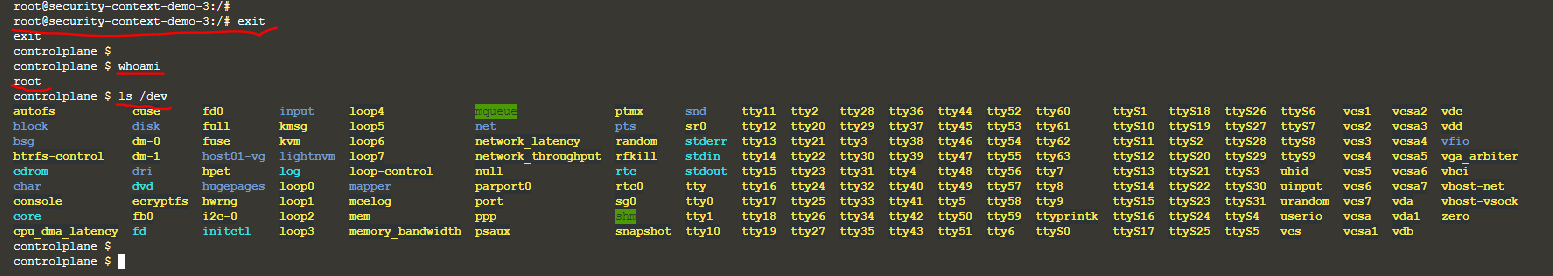
Am I correct? —> No, you are not correct. Even though the user is root, you can see the container root user is having limited privilege. See below image & find the difference. You can see that the container root user is having limited privilege[image 1&2], where as full privileges to container root user[image 3&4]
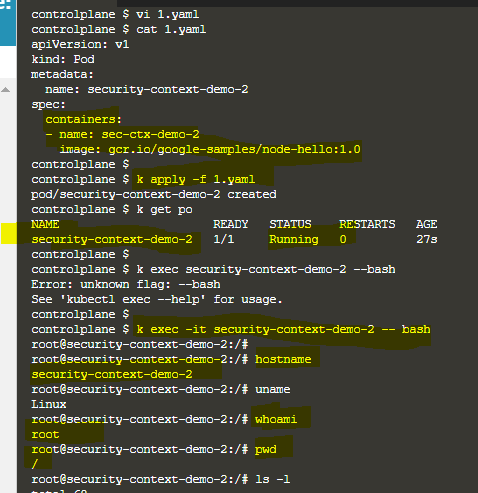
Shakti:
Thanks you so much for the detail explanation. Appreciate your effort.
seand:
nice one