More than likely, yes. If you put an incorrect firewall rule, you can end up blocking all connections to the terminal and it will freeze.
but the Q6 i copied the answer from the HINT. so i dont think it can be wrong
Please paste the link to this lab.
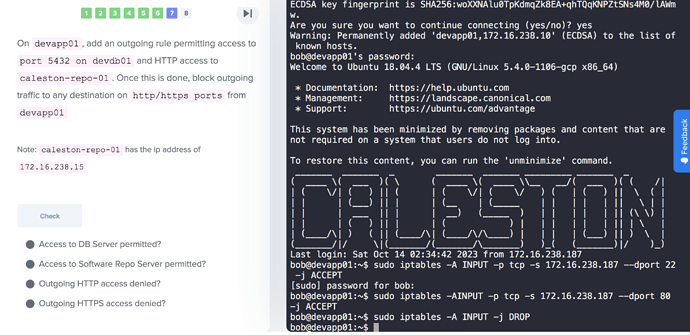
From what I can see in your screenshot, you have created input rules, not output rules as asked in the question.
The three rules you have in order do the following
- Allow from
devdb01todevapp01on 22 - Allow from
devdb01todevapp01on 80 - Block all other incoming traffic
That last rule will definitely lock the terminal!
I suspect if you change all the -A INPUT to -A OUTPUT then it will work
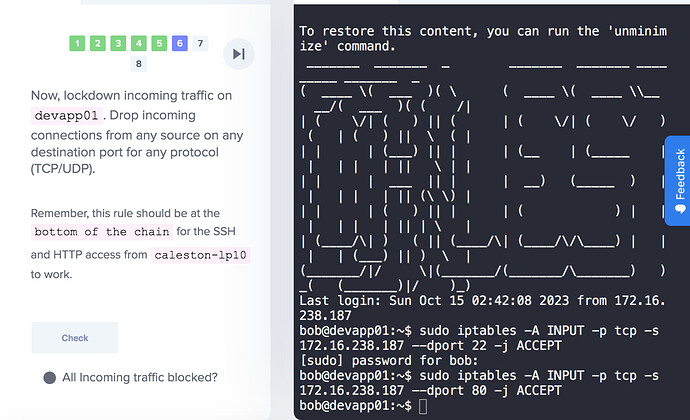
so this is the q6. they ask to lockdown all the income traffic. so after i type command: sudo iptables -A INPUT -j DROP
my screen will froze as the one i up above
I can’t help you until you paste the link to this lab. I can’t find a lab out of the hundreds we have from a screenshot.
here is the link to the lab
Thank you. That makes things a lot easier!
I have to go do stuff now. I will look at it in an hour or so.
yes. thank you so much. looking forward for your reply
First point. What is not shown on the diagram is the connection between you (browser terminal) and “bob’s laptop”. If you manage to firewall that connection, the terminal will lock.
Note also that all the questions require you to add rules to devapp01 so that is where the iptables commands must be run. Note that iptables is already present on bob’s laptop as a trap for the unwary. If you accidentally run any rule there, you can lock the terminal!
If you put an incorrect rule on devapp01 then you can block the connection from bob’s laptop to that server and the terminal will also lock.
My solution
#3
ssh devapp01
sudo apt install -y iptables
exit
ssh devdb01
sudo apt install -y iptables
exit
#5
ssh devapp01
sudo -i
iptables -A INPUT -p tcp -s 172.16.238.187 --dport ssh -j ACCEPT
iptables -A INPUT -p tcp -s 172.16.238.187 --dport http -j ACCEPT
Note I used sudo -i which will log me in as root. Then I do not need to put sudo in front of every command, so less typing.
#6
iptables -A INPUT -j DROP
#7
iptables -A OUTPUT -p tcp -d 172.16.238.11 --dport 5432 -j ACCEPT
iptables -A OUTPUT -p tcp -d 172.16.238.15 --dport http -j ACCEPT
iptables -A OUTPUT -p tcp --dport http -j DROP
iptables -A OUTPUT -p tcp --dport https -j DROP
#8
iptables -I OUTPUT -p tcp -d google.com --dport https -j ACCEPT
At any point you can run
iptables -L
to see the rules you have already put.
i want to ask -y in this command? what does it mean? because i dont see it from the slide in the lecture.
in the lecture there only the command: sudo apt install iptables.
so when i need to use -y?
-y stops apt from asking
Is this ok [y/n]
And just does it.
i want to ask what is different between command ssh bob@devapp01 and ssh devapp01 command?
Nothing - if you are logged in as bob no the machine where you run the ssh command.
ssh defaults to the current user. You only need to give a user name if you want to log into remote system as an different user.