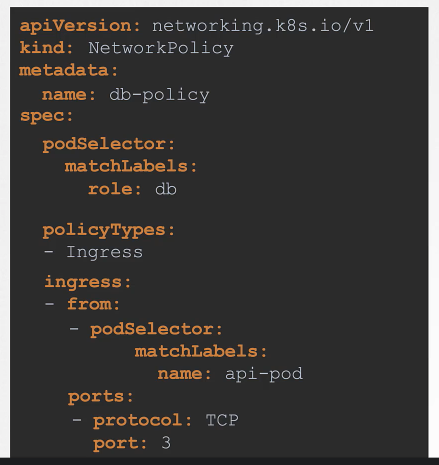
joeypiccola:
I am reviewing network policies. Is my understanding correct that in the following policy definition file where only an ingress rule is defined and applied to pods that match role: db that those pods will be unable to send egress traffic?
In other words, will pods with labels matching role: db only be able to receive traffic from pods with labels name: api-pod and pods with labels matching role: db CANNOT communicate outbound to anything with exception to their stateful and permitted return traffic?
Track Buddy:
Pods with label db will only recieve traffic from pods with label api-pod sending data on port 3
joeypiccola:
@Track Buddy, thanks for the response. I agree with what you explained. But what can pod(s) with label db send traffic to?
Track Buddy:
Anyone …u define egress: - {}
Vaibhav S:
@joeypiccola By default, a pod is non-isolated for egress; all outbound connections are allowed.
You can read further at https://kubernetes.io/docs/concepts/services-networking/network-policies/
Radoslaw Czajkowski:
If you don’t specify egress rule, then egress is not allowed (only return traffic from the ingress rule)
joeypiccola:
I think I understand, so if I have a network policy with both policyTypes:
policyTypes:
- ingress
- egress
… and I do not define any egress exceptions then the pod will only be able to send return traffic associated with what was permitted via the ingress exceptions?