Hi folks,
as we know in v1.25 there is a token auto-attach process that is a little bit changed.
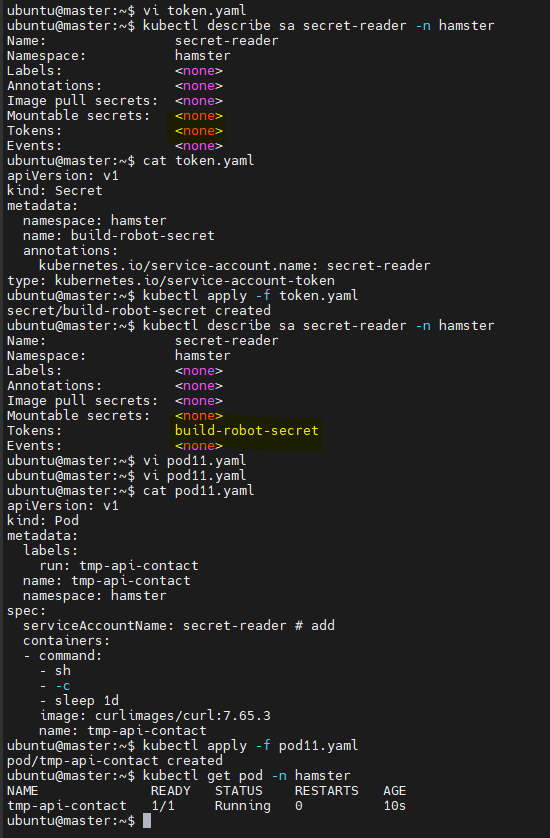
so if I create a ServiceAccount secret-reader in Namespace hamster. Create a Pod of image curlimages/curl:7.65.3 named tmp-api-contact which uses this ServiceAccount.
I did the same thing
I create SA then i create a secret as we need to manually attach the token to SA
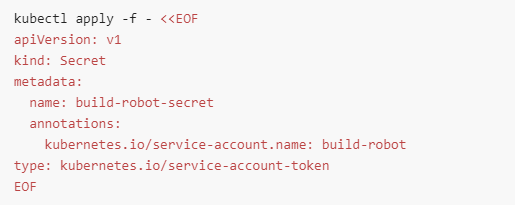
then I got a token that is attached to my SA
but now from the pod
I am not able to access anything
Hello @abhineetsaxena05,
Can you share all manifest files here?
Thanks,
Trung.
sure @trung-kodekloud
this is the step that I followed
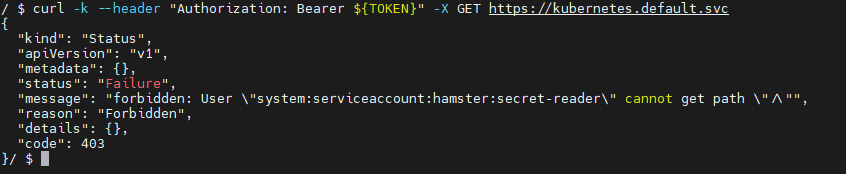
then I go into the pod and run k8s API like so
but when i interact with k8s with API i got 403
Hi @abhineetsaxena05
You do not need to create a secret in 1.24+. Only create a service account:
k create sa build-robot-sa
And use it in the pod
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: test-pod
name: test-pod
spec:
serviceAccount: build-robot-sa
containers:
- image: curlimages/curl:7.65.3
name: test-pod
command:
- sleep
- "3600"
Exec into the pod, and find the token (which is a bearer token)
k exec -it test-pod -- sh
cat /var/run/secrets/kubernetes.io/serviceaccount/token
Of course, you will need to create a role with some permissions and bind it to the service account before you can do anything useful.
To use the token with curl
curl -k -H "Authorization: Bearer $(cat /var/run/secrets/kubernetes.io/serviceaccount/token)" https://kubernetes.default.svc/api/...
okay, that makes sense!
so this is mean when I create SA it is having no role
but can I get to know what role is applied to the default service account?
The default SA has no role assigned to it. If you need to give a pod API server permissions, you should always create a specific SA for the pod, and bind your own custom roles to it.