Alex Tsmokalyuk:
Hi there! I have created “deny all egress traffic” using config here https://kubernetes.io/docs/concepts/services-networking/network-policies/#default-deny-all-egress-traffic and still can curl from one pod to another. the pods are in custom namespace, the netpol is also created for this namespace. What am I doing wrong?
Aneek Bera:
Can u show the details?
Aneek Bera:
Pls show the netpol created. The pod ip addresses, svc, etc.
Alex Tsmokalyuk:
> k describe netpol default-deny-egress
> Name: default-deny-egress
> Namespace: project-snake
> Created on: 2023-01-01 13:49:45 -0500 EST
> Labels: <none>
> Annotations: <none>
> Spec:
> PodSelector: <none> (Allowing the specific traffic to all pods in this namespace)
> Not affecting ingress traffic
> Allowing egress traffic:
> <none> (Selected pods are isolated for egress connectivity)
> Policy Types: Egress
Alex Tsmokalyuk:
> k get po -L APP -n project-snake
> NAME READY STATUS RESTARTS AGE APP
> backend-0 1/1 Running 0 75m backend
> db1-0 1/1 Running 0 75m db1
> db2-0 1/1 Running 0 75m db2
> vault-0 1/1 Running 0 75m vault
Alex Tsmokalyuk:
> k exec backend-0 – curl -s 10.244.1.3:80
>
> <html>
> <head>
> <title>Welcome to nginx!</title>
> <style>
> html { color-scheme: light dark; }
> body { width: 35em; margin: 0 auto;
> font-family: Tahoma, Verdana, Arial, sans-serif; }
> </style>
> </head>
> <body>
> <h1>Welcome to nginx!</h1>
> <p>If you see this page, the nginx web server is successfully installed and
> working. Further configuration is required.</p>
Alex Tsmokalyuk:
> k get po -L APP -n project-snake -owide
> NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES APP
> backend-0 1/1 Running 0 76m 10.244.1.2 node01 <none> <none> backend
> db1-0 1/1 Running 0 76m 10.244.1.3 node01 <none> <none> db1
> db2-0 1/1 Running 0 76m 10.244.1.4 node01 <none> <none> db2
> vault-0 1/1 Running 0 76m 10.244.1.5 node01 <none> <none> vault
Aneek Bera:
curl comamnd?
Alex Tsmokalyuk:
provided above: k exec podname – curl
unnivkn:
Hi @Alex Tsmokalyuk please try this step by step ::
k run frontend --image=nginx --expose --port=80
k run backend --image=nginx --expose --port=80
k get po,svc
–change svc name to frontend-svc & backend-svc
k edit svc frontend
k edit svc backend
k exec frontend – curl backend-svc
–wkg
k exec backend – curl frontend-svc
–wkg
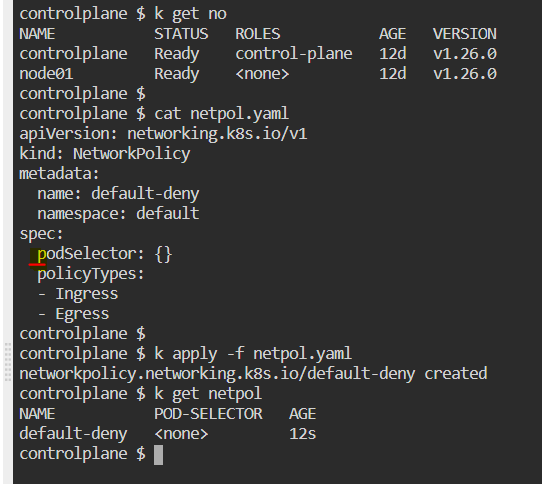
vim default-deny
apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: dafault-deny
namespace: default
spec:
PodSelector: {}
policyTypes:
- Ingress
- Egress
k apply -f default-deny
k get netpol
k exec frontend – curl backend-svc
–blocking
k exec backend – curl frontend-svc
–blocking
Alex Tsmokalyuk:
apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny
namespace: default
spec:
PodSelector: {}
policyTypes:
- Ingress
- Egress
Alex Tsmokalyuk:
k create -f netpol.yaml
Error from server (BadRequest): error when creating “netpol.yaml”: NetworkPolicy in version “v1” cannot be handled as a NetworkPolicy: strict decoding error: unknown field “spec.PodSelector”
Alex Tsmokalyuk:
oh, of course, what a simple mistake xD thank you!
Aneek Bera:
ahh…see
Alex Tsmokalyuk:
> ontrolplane ~ ➜ k get svc -owide
> NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
> backend-svc ClusterIP 10.108.123.59 <none> 80/TCP 21s run=backend
> frontend-svc ClusterIP 10.106.109.254 <none> 80/TCP 59s run=frontend
> kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 53m <none>
>
> controlplane ~ ➜
>
> controlplane ~ ➜
>
> controlplane ~ ➜ k exec frontend – curl backend-svc
> % Total % Received % Xferd Average Speed Time Time Time Current
> Dload Upload Total Spent Left Speed
> 0 0 0 0 0 0 0 0 --:–:-- 0:00:04 --:–:-- 0^C
>
> controlplane ~ ![]() k exec backend – curl frontend-svc
k exec backend – curl frontend-svc
> % Total % Received % Xferd Average Speed Time Time Time Current
> Dload Upload Total Spent Left Speed
> 0 0 0 0 0 0 0 0 --:–:-- 0:00:01 --:–:-- 0^C
>
> controlplane ~ ![]()
Alex Tsmokalyuk:
> controlplane ~ ![]() k describe netpol default-deny
k describe netpol default-deny
> Name: default-deny
> Namespace: default
> Created on: 2023-01-03 16:30:33 -0500 EST
> Labels: <none>
> Annotations: <none>
> Spec:
> PodSelector: <none> (Allowing the specific traffic to all pods in this namespace)
> Allowing ingress traffic:
> <none> (Selected pods are isolated for ingress connectivity)
> Allowing egress traffic:
> <none> (Selected pods are isolated for egress connectivity)
> Policy Types: Ingress, Egress
Alex Tsmokalyuk:
access denied before and after adding netpol
Aneek Bera:
awesome