Jean-Marie Lallemand:
Hi
Question regarding CKA / 154 - Practice Test - Cluster Roles and Role Bindings
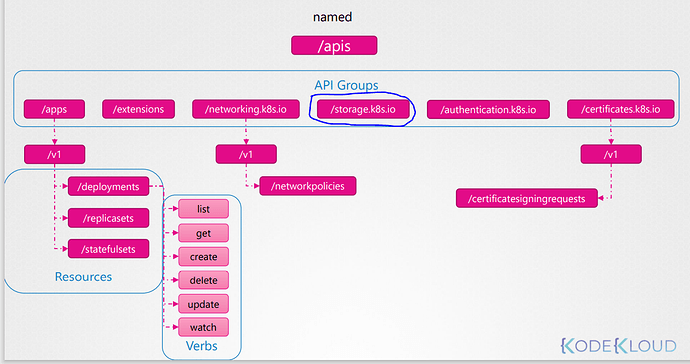
Why for ressources “storageclasses” we need to declare :
- apiGroups:["<http://storage.k8s.io|storage.k8s.io>"] ?
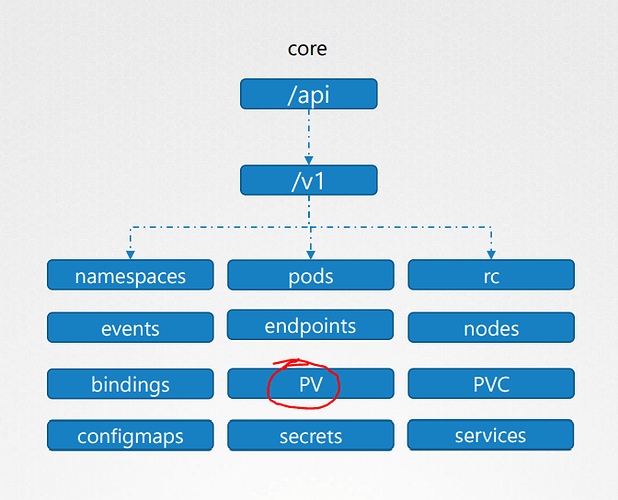
While for ressources “persistentvolumes” we keep :
- apiGroups: [""]
If we keep - apiGroups: [“”] for “storageclasses”, kubectl auth can-i get storageclasses --as michelle give us “No”, although rule seems correct:
k describe clusterrole storage-admin
Name: storage-admin
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
persistentvolumes [] [] [get list watch create delete]
storageclasses [] [] [get list watch create delete]
But if we declare apiGroups:[“http://storage.k8s.io|storage.k8s.io”], , kubectl auth can-i get storageclasses --as michelle give us “Yes”
k describe clusterrole storage-admin
Name: storage-admin
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
persistentvolumes [] [] [get watch list create delete]
<http://storageclasses.storage.k8s.io|storageclasses.storage.k8s.io> [] [] [get watch list create delete]
Thanks for your help
Regards