madhusmita:
Hi, I am trying Create a network policy to allow traffic from the Internal application only to the payroll-service and db-service.
Use the spec given on the below. You might want to enable ingress traffic to the pod to test your rules in the UI.
• Policy Name: internal-policy
• Policy Type: Egress
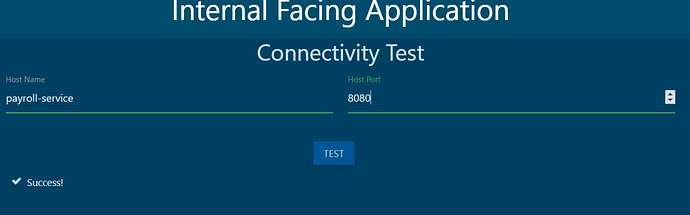
• Egress Allow: payroll
• Payroll Port: 8080
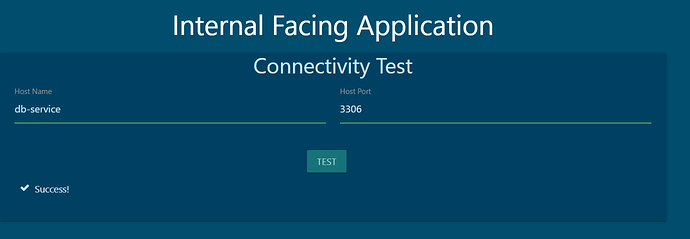
• Egress Allow: mysql
• MySQL Port: 3306
The yaml file:
apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
But the internal application is not connecting to payroll and mysql app. What am I doing wrong?
Sundeep Y:
if u are manually testing the connectivity from internal to payroll or mysql , you should enable ingress to internal to perform ur testing
madhusmita:
manually testing means? I am testing from the given UI.
unnivkn:
May I know you created netpol correctly ? I mean the labels are correct ? k get po -n <namespace> --show-labels
unnivkn:
you should test UI from :
internal —to (egress)—> payroll
internal —to (egress)—> mysql
Reverse senario won’t work.
madhusmita:
root@controlplane:~# kubectl get po -n default --show-labels
NAME READY STATUS RESTARTS AGE LABELS
external 1/1 Running 0 37m name=external
internal 1/1 Running 0 37m name=internal
mysql 1/1 Running 0 37m name=mysql
payroll 1/1 Running 0 37m name=payroll
madhusmita:
root@controlplane:~# kubectl describe netpol internal-policy
Name: internal-policy
Namespace: default
Created on: 2021-08-21 19:22:43 +0000 UTC
Labels: <none>
Annotations: <none>
Spec:
PodSelector: name=internal
Not affecting ingress traffic
Allowing egress traffic:
To Port: 3306/TCP
To:
PodSelector: name=mysql
----------
To Port: 8080/TCP
To:
PodSelector: name=payroll
Policy Types: Egress
root@controlplane:~#
madhusmita:
@unnivkn: could you please check what is wrong in the netpol yaml?
unnivkn:
@madhusmita please try this. you can refer solution tab as well.
unnivkn:
apiVersion: http://networking.k8s.io/v1|networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
-
Egress
egress:
-
to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
-
to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
-
ports:
- port: 53
protocol: UDP
- port: 53
protocol: TCP
madhusmita:
what is the need of - ports:
- port: 53
protocol: UDP
- port: 53
protocol: TCP
?
unnivkn:
Please refer the solution tab
unnivkn:
hope this make sense to you
madhusmita:
got it. Thank you so much.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
- ports:
- protocol: UDP
port: 53
- protocol: TCP
port: 53
@Vivek-Ragupathy The first thing to do – and this is crucial – is to get your YAML correctly formatted. If you don’t, your YAML will be garbled and it won’t be possible to test your answer. So, use the </> key to create a code block
So your YAML will be
- properly indented.
- dashes will not be changed into buttons.
- Quote marks like ' and " will not be turned into smart quotes.