Ary:
Hello together,
iam a little bit confused about the service account and token section (Video 164/165 Service Account and Service Account Updates).
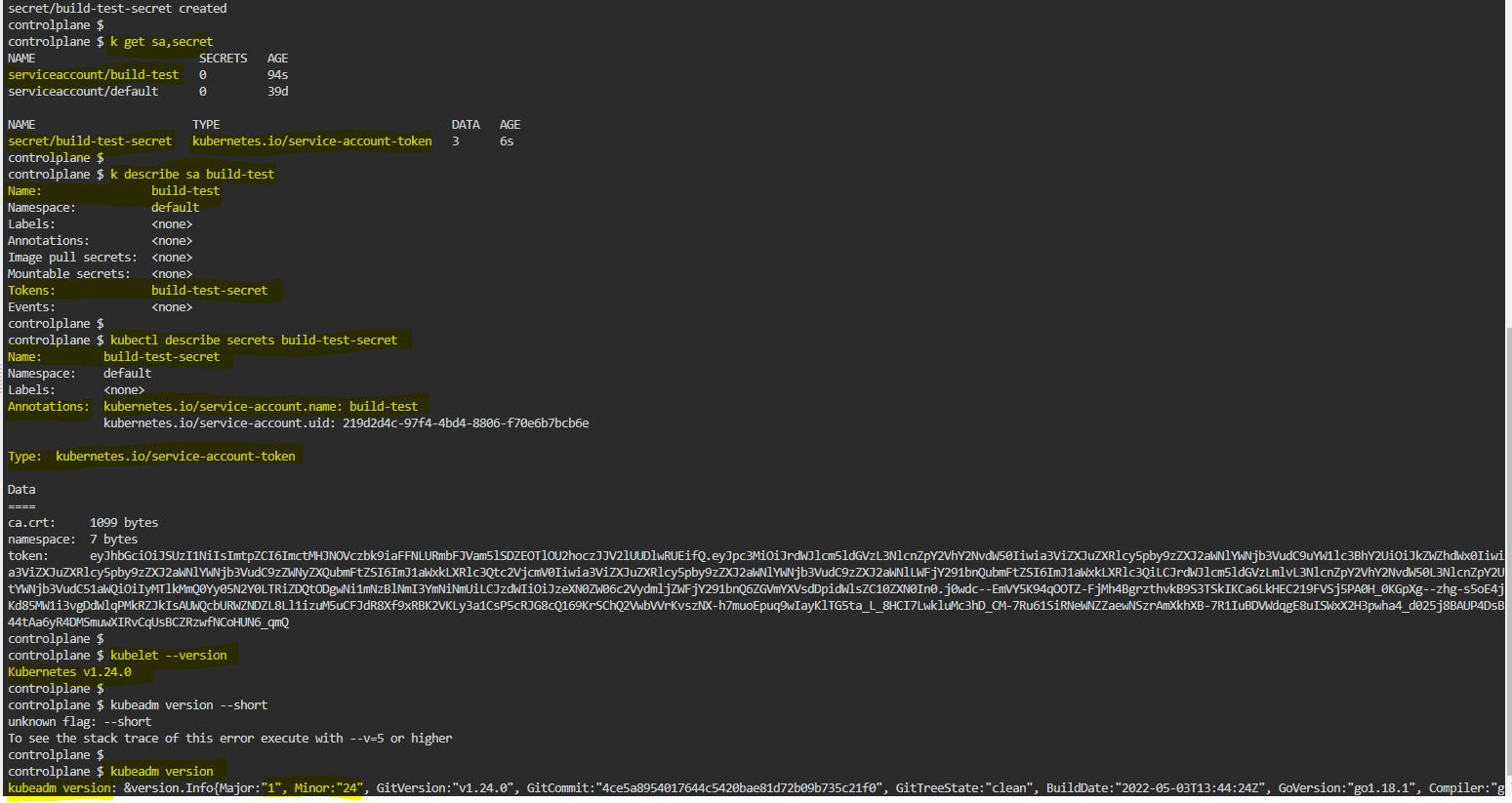
In video 164, there was a unlimited token generated while creating the service account. I can watch this Token via kubectl describe serviceaccount. Within video 165, where token are not longer automaticly created within the creation of a serviceaccount.
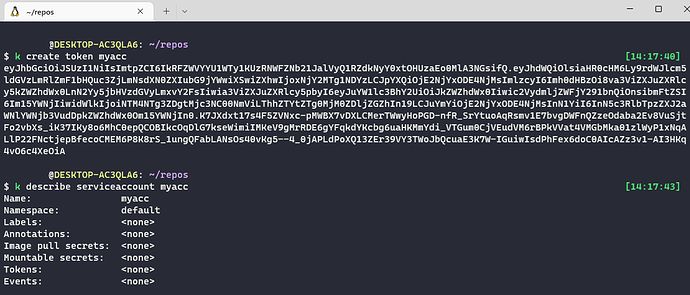
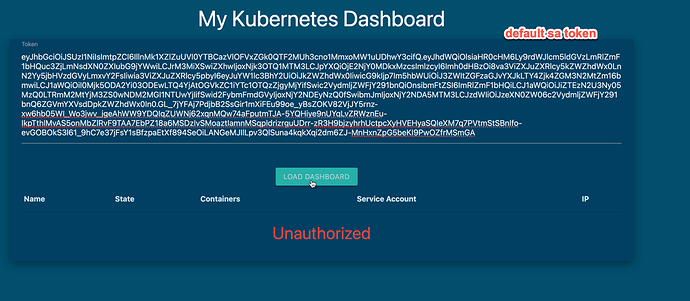
When i create now a token manually, i got the token on the command line, but i cant see the token in the serviceaccount description. It says “Tokens: <none>” (see screenshot 1).
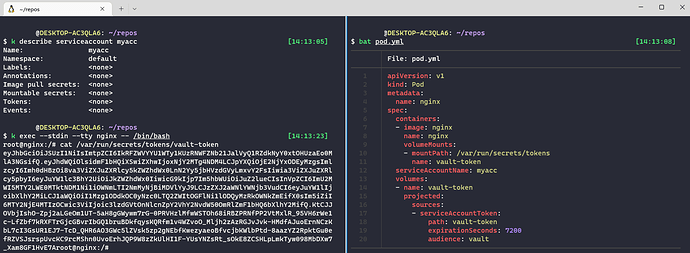
When i create a Token as a vault-token via volume mount together with a pod (see screenshot 2) , i can access the generated token inside the pod, but the the service account still shows “Token: <none>”.
This leads me to the questions:
- is this normal? If yes:
- where i can see a list of all current tokens which are assoicated with my service account? From the service account description it looks like if i had never created any tokens.
Hopes thant makes sense… maybe i missed something but i dont know what.
Iam glad for any help 
Karim:
Hi @Ary this confused me for a while…The way I understood it is that there is a TokenRequestAPI upon pod creation that creates this token regardless of the service account you have configured. If I understand correctly, the objective is to get these tokens more secure and get them to be time bound. This token will be mounted as a projected volume to the pod.
unnivkn:
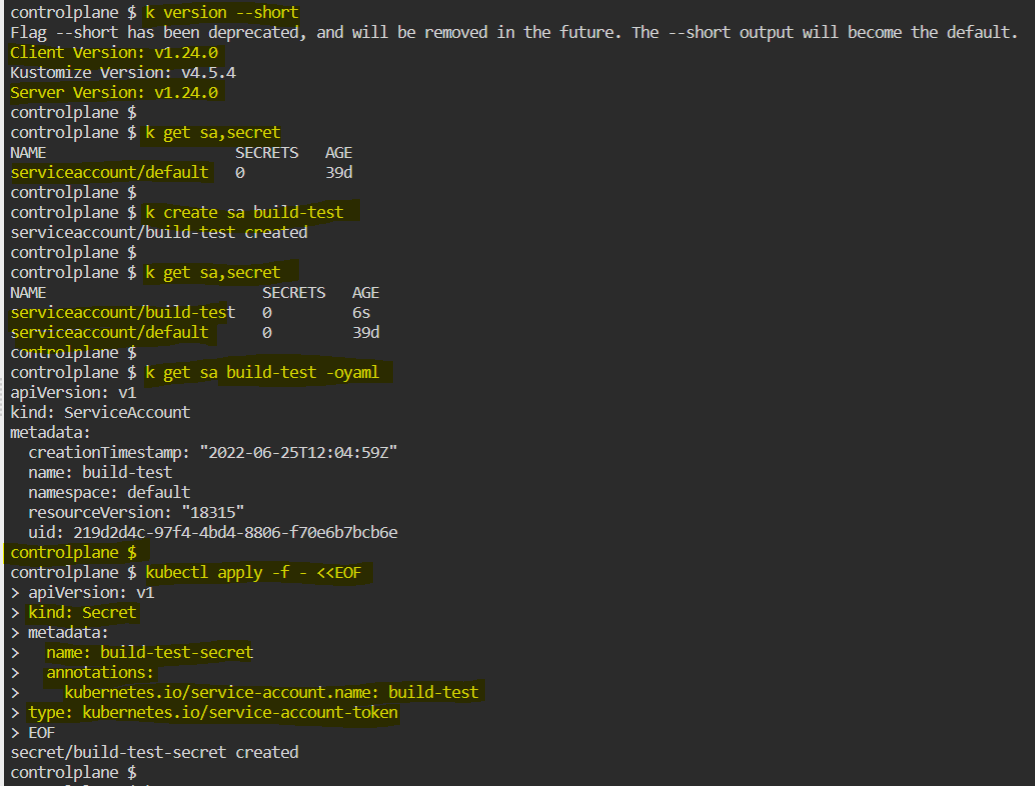
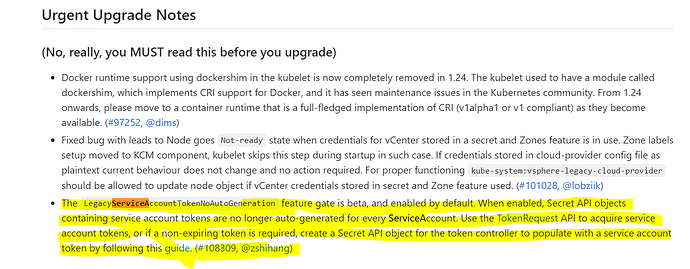
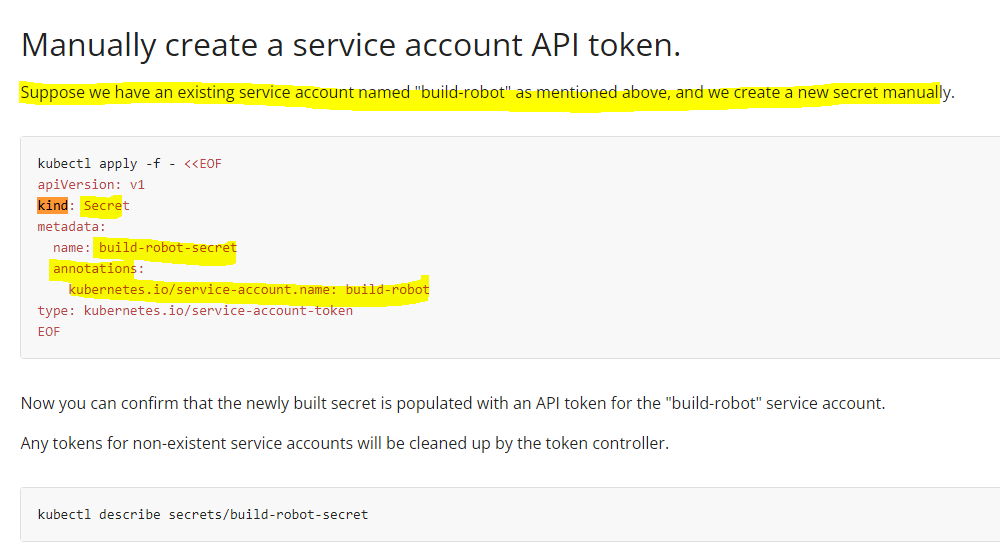
Hi @Ary and @Karim video-164 may be talking about the SA with k8s version till 1.23 . Till version 1.23 service Account creation will automatically create secrets. From k8s version 1.24 on words SA won’t create secrets automatically, instead we have to create a secret & add the existing SA details in it, before it creates.
fyr: https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/#manually-create-a-service-account-api-token
Ary:
Thanks a lot @Karim @unnivkn
Chandu:
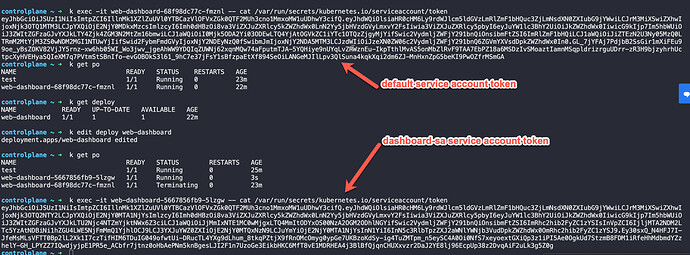
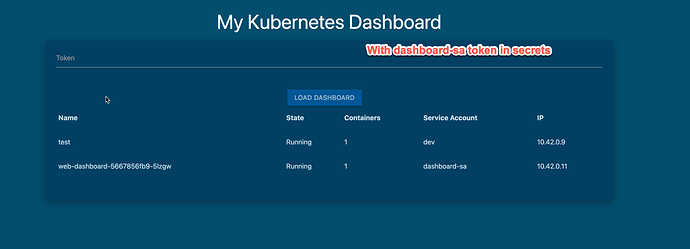
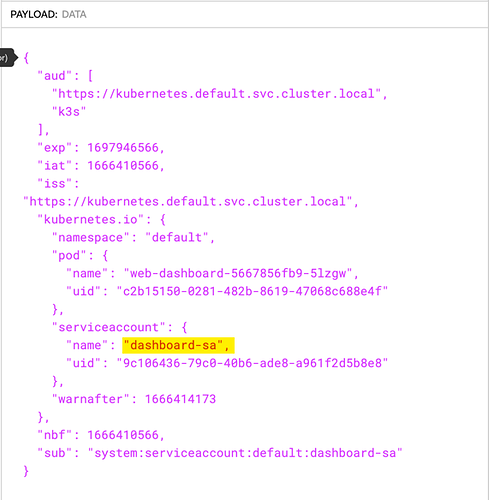
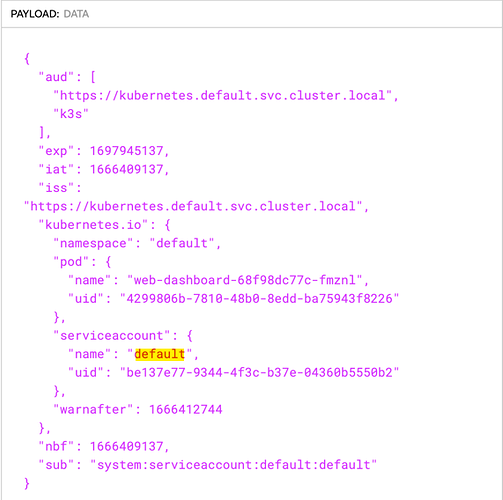
This is what I understand so far… I am doing the configuration and serviceaccount lab. In that question 12-13 is about sa. so, I tried to give a token in the browser before changing the sa from default to the dashboard-sa. So, when I tried to give it in the browser it failed. Whereas, when I changed the sa of the deploy which has right permissions to access the pod info, it created a token on it’s own and grabbed it from the pod and put in the browser it worked fine. So, that means no matter if you create a token or not, the SA will create a token a token and puts in the secrets path. But, my question is since the token is already present in the secrets path why do we need to run the command k create token dashboard-sa ?
Steps I have followed with ss:
- cat the token with default svc account
- put the token in the url to access the dashboard. Which didn’t work and it is expected
- create an sa dashboard-sa and changed the deployment to use the newly created sa. But not created a token manually. I assume at the pod creation not sure how the tokens get created. But, the same way the token associated with the dashboard-sa token got created.
- I grabbed the token from secrets and put it in the dashboard and worked fine. Moreover, I don’t really need to put the token in the browser. Since it is already in secrets location.
Chandu:
@Alistair Mackay Can you please help me understand this?
unnivkn:
Hi @Chandu I agree with you, the way you tested, good job. We may perform a task in multiple ways… Hopefully it may be the k8s cluster v1.23 or lower. Once the cluster upgraded to higher version, secrets and token may not created along with the SA.
Chandu:
Hi @unnivkn. Thank you so much for your help. I really appreciate it. It is really motivating people like me, who have no experience with the kubernetes. That being said, my point here is not about the task. But, about the understanding of sa. My point is not about the cluster version as well. From my testing what I see is we don’t need to explicitly create token. When we create an sa and attach it to a pod, the token gets created automatically. But, what is the use of k create token service_account_name ? Since the token creation already happening with the pod creation itself. I hope I am making sense here.
Alistair Mackay:
The key takeaways with SA are
• Kubernetes version < 1.24 - Creating a service account also creates a secret with a token in it. This token has no time constraint and will be shared by all pods that use the SA.
• Kubernetes version >= 1.24 - Creating a service account does not create a secret. When you associate a SA with a pod, then a projected volume is mounted inside the pod. The projection overlays the token API such that the API will rotate the token approx every hour. It may be also that the token is unique for every pod using the SA. Would need to do an experiment to find out - easily done, so an exercise for the reader 
Chandu:
Thank you @Alistair Mackay. One last question here: Why do we need to create a token manually using k create token service_account_name command as token creation is taken care by k8s itself? What are the benefits/disadvantages of creating it manually vs let pod create a token on it own?
Alistair Mackay:
I can’t really see a use case for that. Maybe to retain backward compatibility. Better if a pod needs a token to let it happen automatically.
Chandu:
Thank you so much both of you @Alistair Mackay and @unnivkn for your inputs on my questions. This is great
![]()