Genko:
Hello. I have a question about official documentation. For me network policies only work if I put dash before -to AND before -ports, is it typo in documentation or some special case?
Aswin Venkat:
@Genko you need to understand the YAML.
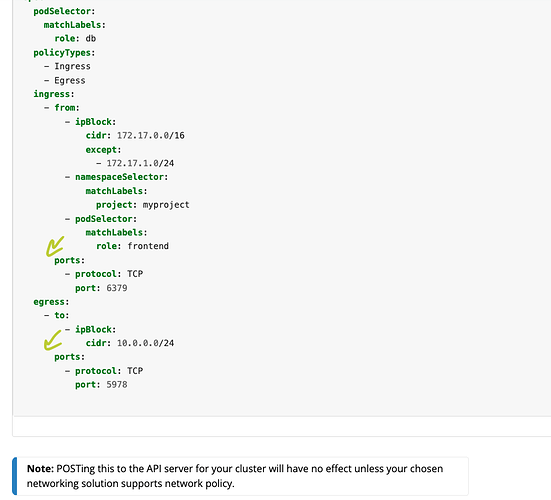
in the above image , it can be
- to
ports
or
- ports
to
they both are under same object , so either ports or to should start with - symbol. the same for from object.
Genko:
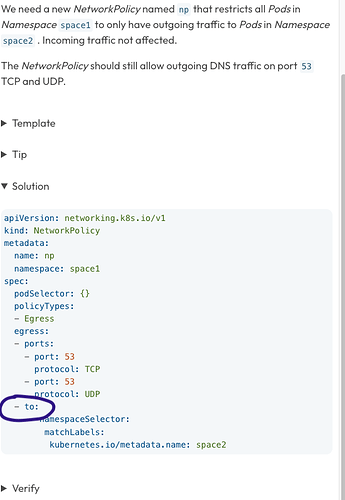
@Aswin Venkat you didn’t get it, I know yaml and that this is an object. Look at this solution from Killerkoda
Aswin Venkat:
@Genko the solution is correct only , there is necessary that the object should contain both the ports and to attribute.
So there are 2 different options objects in the picture. First one doesn’t contain to , only ports , which means the port is opened to all (no restriction)
Genko:
look at the doc reference describing NetworkPolicies https://kubernetes.io/docs/reference/kubernetes-api/policy-resources/network-policy-v1/
Aswin Venkat:
@Genko port 53 is open to all , that’s why there is no “to” mentioned
Genko:
it MUST have dash according to official reference on original picture before -ports
Genko:
there’s NO *egress.*to.ports
Aswin Venkat:
@Genko the solution in the picture is correct as per my knowledge.
The first object allows all egress to 53 port.
The second object will restrict all egress to space2 namespace.
It gives correct answer to the question that is asked.
Genko:
@Aswin Venkat ofcourse its correct, I have showed you correct one to compare with original one
Genko:
there are two types of rules possible NetworkPolicyPeer or NetworkPolicyPort, and on this image the yaml is incorrect https://kodekloud.slack.com/archives/CHMV3P9NV/p1695650574999779
Alistair Mackay:
➜ ~ k explain netpol.spec.ingress
KIND: NetworkPolicy
VERSION: <http://networking.k8s.io/v1|networking.k8s.io/v1>
RESOURCE: ingress <[]Object>
DESCRIPTION:
List of ingress rules to be applied to the selected pods. Traffic is
allowed to a pod if there are no NetworkPolicies selecting the pod (and
cluster policy otherwise allows the traffic), OR if the traffic source is
the pod's local node, OR if the traffic matches at least one ingress rule
across all of the NetworkPolicy objects whose podSelector matches the pod.
If this field is empty then this NetworkPolicy does not allow any traffic
(and serves solely to ensure that the pods it selects are isolated by
default)
NetworkPolicyIngressRule describes a particular set of traffic that is
allowed to the pods matched by a NetworkPolicySpec's podSelector. The
traffic must match both ports and from.
FIELDS:
from <[]Object>
List of sources which should be able to access the pods selected for this
rule. Items in this list are combined using a logical OR operation. If this
field is empty or missing, this rule matches all sources (traffic not
restricted by source). If this field is present and contains at least one
item, this rule allows traffic only if the traffic matches at least one
item in the from list.
ports <[]Object>
List of ports which should be made accessible on the pods selected for this
rule. Each item in this list is combined using a logical OR. If this field
is empty or missing, this rule matches all ports (traffic not restricted by
port). If this field is present and contains at least one item, then this
rule allows traffic only if the traffic matches at least one port in the
list.
What this tells us that below
spec:
ingress:
follows a list of object. The structure of the ingress object is two fields from and ports. Both are optional, meaning that each rule in the list beginning with - may have either ports only, from only or both. If both are present, the order is not significant…
Egress works similarly, but the rule object has to field instead of from
Genko:
Ok so we have list of NetworkPolicyIngressRule rules, each of them may have both or one of two keys -ports or -from/to. On the first picture it has object with both keys from/ports for ingress and to/ports for egress. On second picture it has two rules with one key -ports and one key -to
Genko:
so and -ports key applies for all selected pods in namespaces or for -from/to key
Alistair Mackay:
ports applies to what is selected by the rule. With no from or to it is a rule that applies to everything the policy is attached to. This is why the DNS egress policy only has ports - it allows egress only on the DNS ports, but to anywhere.
Alistair Mackay:
Remember also that a network policy applies to PODS, those pods being matched by the initial podSelector that is not part of the rules. Network polices are simple firewalls for pods, not namespaces or subnets. They govern what goes into and out of the pods to which it applies
Alistair Mackay:
The concept of netpols seems the most difficult thing to grasp for nearly everyone, but once you understand them properly they do make sense.
Alistair Mackay:
Recommended: https://kodekloud.com/courses/learn-by-doing-kubernetes-network-policies/