cristiano ronaldoo:
Hello Guys , I am a bit confused between the 2 files here : cant get the role of kubeconfig for each core component pod
like the what is the diff between :
-kubeconfig=/etc/kubernetes/kubelet.conf --config=/var/lib/kubelet/config.yaml
Hasan Alsaedi:
Maybe this k8s docs can help https://kubernetes.io/docs/setup/production-environment/tools/kubeadm/kubelet-integration/#workflow-when-using-kubeadm-init
Aneek Bera:
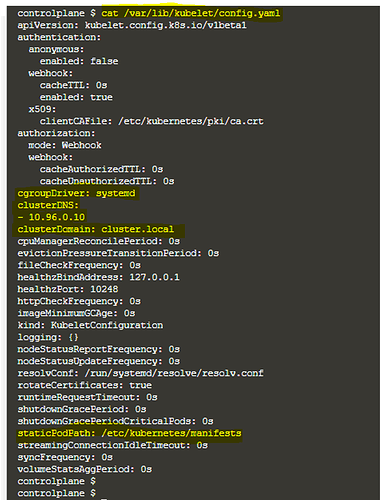
config.yaml file sets kubelet parameters. e.g.
apiVersion: <http://kubelet.config.k8s.io/v1beta1|kubelet.config.k8s.io/v1beta1>
authentication:
anonymous:
enabled: false
webhook:
cacheTTL: 0s
enabled: true
x509:
clientCAFile: /etc/kubernetes/pki/ca.crt
authorization:
mode: Webhook
webhook:
cacheAuthorizedTTL: 0s
cacheUnauthorizedTTL: 0s
cgroupDriver: cgroupfs
clusterDNS:
- 10.96.0.10
clusterDomain: cluster.local
cpuManagerReconcilePeriod: 0s
evictionPressureTransitionPeriod: 0s
fileCheckFrequency: 0s
healthzBindAddress: 127.0.0.1
healthzPort: 10248
httpCheckFrequency: 0s
imageMinimumGCAge: 0s
kind: KubeletConfiguration
logging: {}
nodeStatusReportFrequency: 0s
nodeStatusUpdateFrequency: 0s
resolvConf: /run/systemd/resolve/resolv.conf
rotateCertificates: true
runtimeRequestTimeout: 0s
shutdownGracePeriod: 0s
shutdownGracePeriodCriticalPods: 0s
staticPodPath: /etc/kubernetes/manifests
streamingConnectionIdleTimeout: 0s
syncFrequency: 0s
volumeStatsAggPeriod: 0s
Once the cluster info are known, the file bootstrap-kubelet.conf is written, thus allowing kubelet to do TLS Bootstrapping.
The TLS bootstrap mechanism uses the shared token to temporarily authenticate with the Kubernetes API server to submit a certificate signing request (CSR) for a locally created key pair.
The request is then automatically approved and the operation completes saving ca.crt file and kubelet.conf file to be used by kubelet for joining the cluster, whilebootstrap-kubelet.conf is deleted.
The file contents:
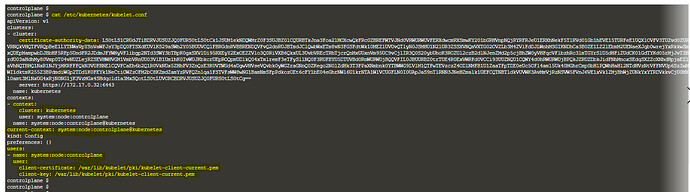
wQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeU1ERXhNekF3TXprMU5Wb1hEVE15TURFeE1UQXdNemsxTlZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTXR0CmZWSWxnUlRtUzJrcHdRWFRXMWZqNlNEeVVnL0dQZzFkWW5OejBWREZYRERYcnZWR0dXVHZWUG5HSXk3WVVhVDcKOUdUWjdUUGJKRkdNcTViMzVMeHk5dDV5REVmN3hyYWJvSlYvK2hUcncrMW1kNGJHZlZhenRtM3RLM0V1NHZsTwo5Q01jTmlLdm05WDA4Tk5xZ1hkaGY2MkJyRkVKSFpEa0oyeXdsNTBMUDdZNFJ1RnF5Tm9pNWpWMS8wbi9FNDhwCmJJMWkxQ0cyWXRxTGZMNVU1Ly9ZV3ZMR2twMkFXTUFIVDF0Y05kQWM2blpVdENyUVF1TGUydGlvOW5sQjRmUUwKUWRPSzVjUVNKamU0UFdkRWVBSkY2QVREREJrVzc1QWxvcDF4amxzZ0RXL2lZaDN6TEQyM0x0NFVuS2Z0aXNlawpOUms0UHI1aVBPWk1NMFlSY2s4Q0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPUldkQ210emh6S25BcmZzVlVXWUoyZWNyejFNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFBTnNORUlUcFE4ZkVyL2VpMTd1RUV6U1N6MjVOenBrNzNWakZSMVNJdXQxS2FvZmYwQQo2TmNDdEdmQUdQOWxFVWhzdHljWk9adm5rczlnRHd1NkxscDFiRzk3SW5UZFV4bzRYdFErQjNxVTJJZlZnVy9RCkpSQThKSXk2c0NrU1MyNlZzRkxSeXhzTGlXUHZIZnlYR1hPNnJHa1Z0ZHlTanY1V1JONTNVaEpUN1J2VXFtUmoKSHJ4Q0FMbjFtYiswUVhGUDd0Y0RzOU44OTBxSXJwaW5YRFJjVk01SmFlbXNyMGJ3SUYvcmxXakdvdXZvYTJmUgp4UmZCRFVING4zcEFwRE5oam52VUJ4SDZPcVViR1hJZE1oZTFzTFJsQVQzeVpoMVdDUG1YQjRlb0VHelRHYTNUCmlkb05ZbFJFMjhCbHNOanc5UEVtVnRLUHF4UlF0YXdGSXRxRwotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: <https://controlplane:6443>
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: system:node:controlplane
name: system:node:controlplane@kubernetes
current-context: system:node:controlplane@kubernetes
kind: Config
preferences: {}
users:
- name: system:node:controlplane
user:
client-certificate: /var/lib/kubelet/pki/kubelet-client-current.pem
client-key: /var/lib/kubelet/pki/kubelet-client-current.pem
unnivkn:
Hi @cristiano ronaldoo good question. This give me an opportunity to revisit the concepts/architecture.
–kubeconfig=/etc/kubernetes/kubelet.conf
In simple terms,
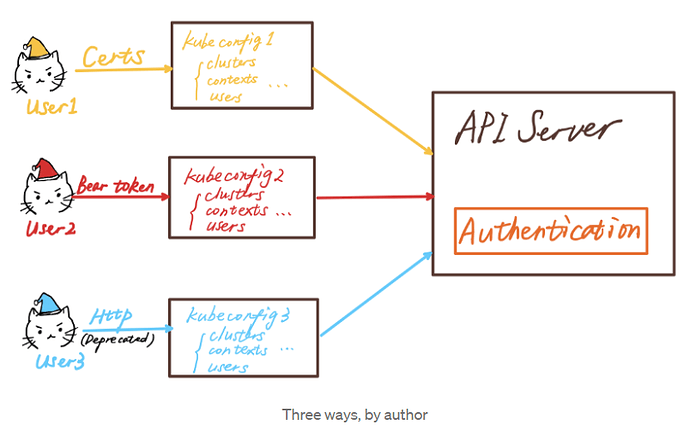
kubeconfig is used to authenticate(token, nothing but user/pwd in k8s terms) any client to kube-apiserver. In this case kubelet is the client communicates our server: kube-apiserver. Let’s say you need to do some activities on k8s cluster, then you act as client(as an admin user, so your kubeconfig may be: --kubeconfig=~/.kube/config) to kube-api server. And your authentication to kube-apiserver will be there in ~/.kube/config (refer the image).
–config=/var/lib/kubelet/config.yaml
This file is related to kubelet internal, you can see the below image of this file.
Eg: How kubelet locate the static pod yaml’s to do it’s operation, cgroupDriver, clusterDNS informations etc needed for it’s normal functionality.
hope this helps. ![]()
gopi m:
@cristiano ronaldoo Kubeconfig is like the office ID card you show to get inside (here you show it to kube-api server). And once you are in, you use your laptop/toolkit to do the actual work - and that laptop is the second config (it defines what parms you use and how you will perform the activities)