Hello Everyone.
here comes my first post in this community.
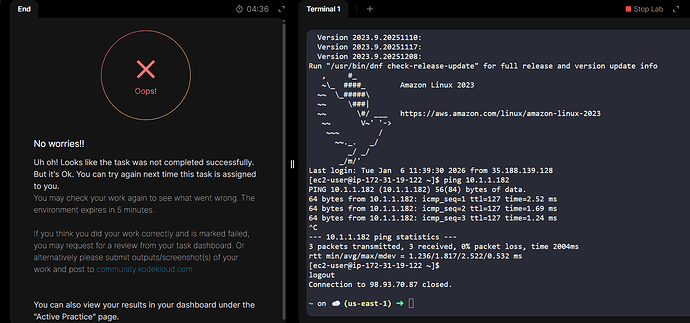
I was wondering what can be an issue with this one? ![]()
SSH Public key is saved on public EC2 instance so I can connect with it without any password. Also I can ping private EC2 by its IP address.
What struck me is that there is no error message. Why is that?
The process I was following is this:
-
save ids of two vpcs to be connected
DEFAULT_VPC_ID=$(aws ec2 describe-vpcs --filters “Name=is-default,Values=true” --query “Vpcs[0].VpcId” --output text)
PRIVATE_VPC_ID=$(aws ec2 describe-vpcs --filters “Name=tag:Name,Values=devops-private-vpc” --query “Vpcs[0].VpcId” --output text) -
create a request for peering connection
PEER_CONNECTION_ID=$(aws ec2 create-vpc-peering-connection --vpc-id $DEFAULT_VPC_ID --peer-vpc-id $PRIVATE_VPC_ID --query ‘VpcPeeringConnection.VpcPeeringConnectionId’ --output text) -
accept the connection
aws ec2 accept-vpc-peering-connection --vpc-peering-connection-id $PEER_CONNECTION_ID -
get route table ids
DEFAULT_ROUTE_TABLE_ID=$(aws ec2 describe-route-tables --filters “Name=vpc-id,Values=$DEFAULT_VPC_ID” --query “RouteTables[0].RouteTableId” --output text)
PRIVATE_ROUTE_TABLE_ID=$(aws ec2 describe-route-tables --filters “Name=vpc-id,Values=$PRIVATE_VPC_ID” --query “RouteTables[0].RouteTableId” --output text) -
get cidr for both vpcs
DEFAULT_CIDR=$(aws ec2 describe-vpcs --vpc-ids $DEFAULT_VPC_ID --query “Vpcs[0].CidrBlock” --output text)
PRIVATE_CIDR=$(aws ec2 describe-vpcs --vpc-ids $PRIVATE_VPC_ID --query “Vpcs[0].CidrBlock” --output text) -
update route table of requester vpc
aws ec2 create-route --route-table-id $DEFAULT_ROUTE_TABLE_ID --destination-cidr-block $PRIVATE_CIDR --vpc-peering-connection-id $PEER_CONNECTION_ID
aws ec2 create-route --route-table-id $PRIVATE_ROUTE_TABLE_ID --destination-cidr-block $DEFAULT_CIDR --vpc-peering-connection-id $PEER_CONNECTION_ID -
get public instance information
DEFAULT_INSTANCE_ID=$(aws ec2 describe-instances --filters “Name=tag:Name,Values=devops-public-ec2” --query “Reservations[].Instances[].InstanceId” --output text)
DEFAULT_INSTANCE_IP=$(aws ec2 describe-instances --instance-ids $DEFAULT_INSTANCE_ID --query “Reservations[].Instances[].PublicIpAddress” --output text) -
get private instance id
PRIVATE_INSTANCE_ID=$(aws ec2 describe-instances --filters “Name=tag:Name,Values=devops-private-ec2” --query “Reservations[].Instances[].InstanceId” --output text) -
get SG ID for public instance
DEFAULT_SG_ID=$(aws ec2 describe-instances --instance-ids $DEFAULT_INSTANCE_ID --query “Reservations[0].Instances[0].SecurityGroups[0].GroupId” --output text) -
open port 22 (ssh)
aws ec2 authorize-security-group-ingress --group-id $DEFAULT_SG_ID --protocol tcp --port 22 --cidr 0.0.0.0/0 -
copy ssh key from host to public instance
aws ec2-instance-connect send-ssh-public-key --instance-id $DEFAULT_INSTANCE_ID --instance-os-user ec2-user --ssh-public-key file://~/.ssh/id_rsa.pub -
get security group of private instance
PRIVATE_SG_ID=$(aws ec2 describe-instances --instance-ids $PRIVATE_INSTANCE_ID --query “Reservations[0].Instances[0].SecurityGroups[0].GroupId” --output text) -
allow ICMP traffic to private ec2
aws ec2 authorize-security-group-ingress --group-id $PRIVATE_SG_ID --protocol icmp --port -1 --cidr $DEFAULT_CIDR -
copy tempo
aws ec2-instance-connect send-ssh-public-key --instance-id $DEFAULT_INSTANCE_ID --instance-os-user ec2-user --ssh-public-key file://~/.ssh/id_rsa.pub -
get ssh public key
cat ~/.ssh/id_rsa.pub -
connect with instance
ssh ec2-user@$DEFAULT_INSTANCE_IP -
once on ec2
nano ~/.ssh/authorized_keys
paste ssh public key