Hello Team,
I was looking for some assistance on trivy scan of docker images which something i’m trying to achieve in jenkins, here’s the details
- i’ve installed trivy on the jenkins server and now if i want to scan the docker images and hence i’ve installed docker aswell on this server now if the script fails with exitcode 1 then it should try to fix with old images is there way to identify this process in the jenkins can you share me if any script to identify this?
trivy can generate a lot of output, so it’s handy to use grep to get to the “bottom line”. I typically do something like this in the shell:
trivy image -s CRITICAL nginx 2>/dev/null | grep Total
If all you’re doing is determining if there’s a problem with an image, this will suffice.
Thanks, for your quick response, i’ve used this in the jenkins file
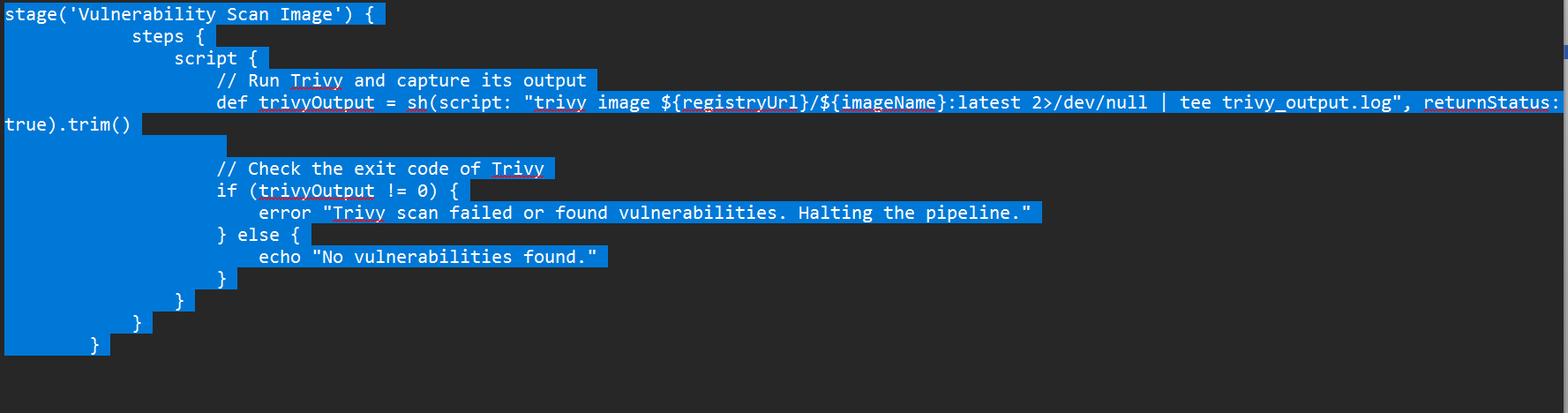
here’s the script
stage(‘Vulnerability Scan Image’) {
steps {
script {
// Run Trivy and capture its output
def trivyOutput = sh(script: “trivy image ${registryUrl}/${imageName}:latest 2>/dev/null | tee trivy_output.log”, returnStatus: true).trim()
// Check the exit code of Trivy
if (trivyOutput != 0) {
error "Trivy scan failed or found vulnerabilities. Halting the pipeline."
} else {
echo "No vulnerabilities found."
}
}
}
}
while testing this pipeline is failing however, i’m not able to get the overall report of that critical vulnerablity its showing as
Final trivy scan results:
Total : 0 (Critical : 0)
Total: 2 (Critical: 2)
echo
No critical vulnerabilities found
Error: Trivy scan failed or found vulnerabilities. halting the pipeline finished failure.
how to find that 2 critical vulnerabilitie?
I’m out of practice with Jenkins, although I’m pretty current with Trivy. To help us help you, take a look at this tutorial on entering code in Discourse, so we can debug what you’re doing.
As for figuring out what the vulnerabilities are: before you start coding in Jenkins, take a look at the raw output that Trivy emits; you should be able to see how CVE are printed, and you can then figure out how in bash to extract the text you need.
Thanks Rob, it worked me for i’m able to tweak with the trivy scan, Thanks for your support. Appreciate it
Thanks
Avinash
No problem! Happy to help.