Hi,
Can anyone help me on this. This task is getting failed and I am not sure where I am doing wrong.
The Nautilus DevOps team is expanding their Azure infrastructure and requires the setup of a private Virtual Network (VNet) along with a subnet. This VNet and subnet configuration will ensure that resources deployed within them remain isolated from external networks and can only communicate within the VNet. Additionally, the team needs to provision a Virtual Machine (VM) under the newly created private VNet. This VM should be accessible from within the VNet only, allowing for secure communication and resource management within the Azure environment.
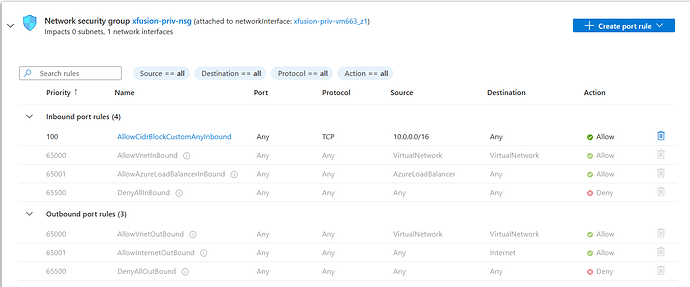
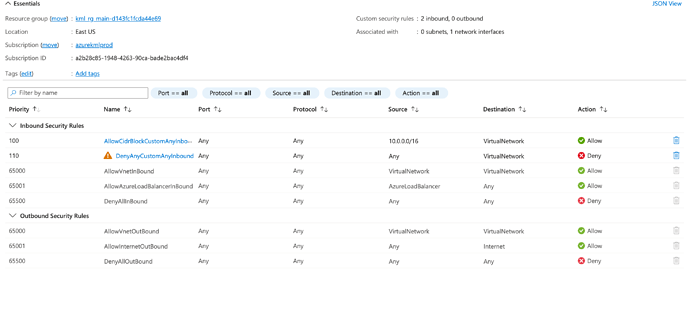
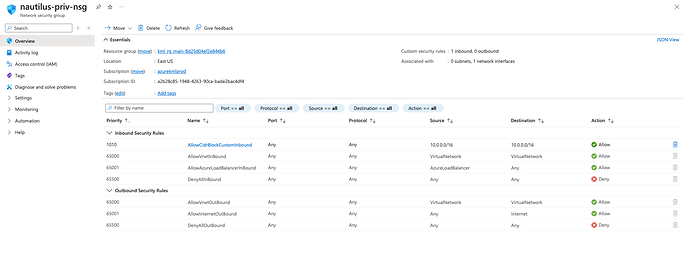
The name of the VNet must be xfusion-priv-vnet, create a subnet named xfusion-priv-subnet under the same. Further, create a Virtual Machine named xfusion-priv-vm under this VNet. Additionally, create a Network Security Group (NSG) named xfusion-priv-nsg, and ensure that the NSG rules for the VM allow access only from within the VNet’s CIDR block. Ensure all resources are created in the East US region.
Please see attached snip of NSG rules, I am allowing access only from within vnet. I tested this by creating another vm and also I am not able to access the vm from my local machine. I further disabled public ip. Please suggest if am missing anything.
Error: NSG ‘xfusion-priv-nsg’ does not allow access from the VNet’s CIDR block ‘10.0.0.0/16’
Thank You
I have the same issue and I’d like to understand how to resolve it.
@raymond.baoly Could you please advise how task can be completed?
In nsg create inbound rule
denyinbound
source : internet(service tag)
destination : any
action : deny
tried this as well. Didn’t work. please mention the steps done if the task is completed to cross check.
under priority replace 100 with 300 and check if not, add inbound deny rule priority 301 any any deny it will work out
Is this issue resolved or not give feedback
As for me I still can’t pass it.
This is the last task left in Level 2.
Being stuck on this task for couple of hours, would you please explain the inbound rules to add to the network security group with all the details (priority, protocol…). I have the same issue and your suggestion didn’t work or maybe I didn’t understand it very well. I thought the inbound rule to allow access from the vnet CIDR will be sufficient but the task failed each time. Thank you for further clarification.
Hi,
This is a valid issue, and there is an internal ticket for it. I’ll update you on the status once it’s fixed.
1 Like
Hi,
Is there any update on this as I’m having the same problem? I’ve created a custom inbound allow rule for the CIDR range on the VNET and the a deny rule underneath for everything else. I get a task failure of " NSG ‘devops-priv-nsg’ does not allow access from the VNet’s CIDR block ‘10.0.0.0/16’" when clearly, it’s in place. I gather this is an internal problem with your test script.
Secondly as a general comment I do think you need to make the detail in some of your tasks clearer. A lot of the them are quite ambiguous, this isn’t realistic in the working world. For instance with this question there isn’t any port details at all and it’s assumed all port access (at least I am assuming this). If I received this ticket at work I would reject it and ask for more detail.
Many thanks
Steve
Hii did you complete task? if complete please share the steps
Hi,
is there any news about this request ?
I have the same problem
Best Regards
Hi @raymond.baoly please update on the request.
Hi guys,
The team just updated it, and the validation is working as expected. I checked it, and it’s working fine on my end. Please try again.
1 Like
I can confirm that I was able to pass it now.