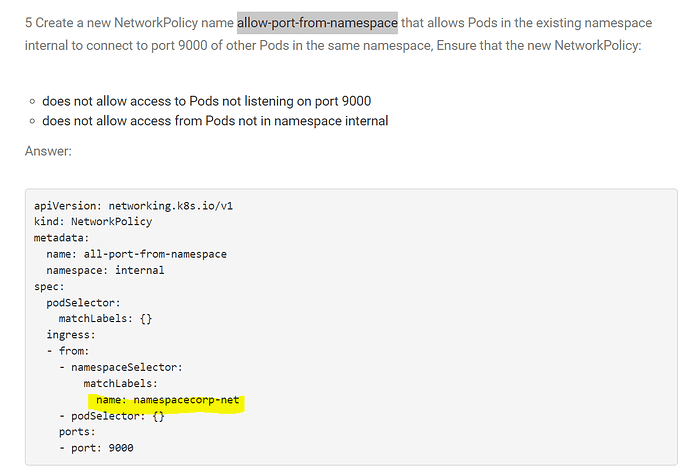
Zxc:
Could someone confirm this answer is correct? The question is a bit tricky, and the internal namespace should be selected in the namespace option. It is correct what I said
Alistair Mackay:
Hi @Zxc
What I see here is
• Any pod in any namespace labelled namespacecorp-net on port 9000 - Allow
• Any pod in namespace internal on port 9000 - Allow
• Anything else - Deny
The first rule could allow access from namespaces other than internal if they have the given label.
Looks to me like the first rule is surplus to requirement.
Alistair Mackay:
To better understand network policies, use https://editor.cilium.io/
You can upload a policy document to it by pressing the up-arrow button at top of the YAML pane.,
Radoslaw Czajkowski:
this is indeed tricky as it requires 2 rules
Radoslaw Czajkowski:
for the first rule - egress to port 9000 for all pods in namespace internal
Radoslaw Czajkowski:
for the second rule - ingress from all pods in the internal namespace
Aneek Bera:
According to the requirements of the topic, we can know that this is the rule of ingress, and it is in the same ns, and there is no need to specify labels, so the contents related to labels and egress can be deleted.
Aneek Bera:
Here is the yaml file:
apiVersion: <http://networking.k8s.io/v1|networking.k8s.io/v1>
kind: NetworkPolicy
metadata:
name: allow-port-from-namespace
namespace: my-app
spec:
podSelector:
matchLabels:
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
ports:
- protocol: TCP
port: 9200
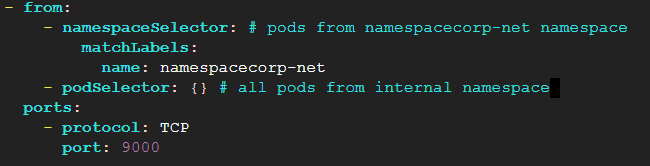
Ceci Ivanov:
i think the identation is wrong
should it be like that?
Alistair Mackay:
@Ceci Ivanov What makes you think the indentation is wrong?
Alistair Mackay:
ingress:
- from:
- namespaceSelector:
and
ingress:
- from:
- namespaceSelector:
are both valid indentation for YAML arrays
Ceci Ivanov:
what exactly is the rule it’s just must be 2 spaces after each line?
when some spec is child of another?
Alistair Mackay:
@Ceci Ivanov Please read https://github.com/kodekloudhub/community-faq/blob/main/yaml-faq.md