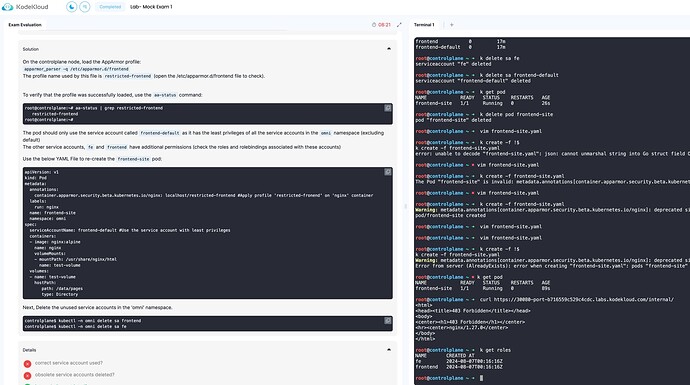
I’m doing the CKS mock exams part and I’ve stumbled into a question that is written misleadingly:
A pod has been created in the
omninamespace. However, there are a couple of issues with it.
The pod has been created with more permissions than it needs.
It allows read access in the directory
/usr/share/nginx/html/internalcausing anInternal Siteto be accessed publicly.To check this, click on the button called
Site(above the terminal) and add/internal/to the end of the URL.
Use the below recommendations to fix this.
Use the AppArmor profile created at
/etc/apparmor.d/frontendto restrict the internal site.There are several service accounts created in the
omninamespace. Apply the principle of least privilege and use the service account with the minimum privileges (excluding thedefaultservice account).Once the pod is recreated with the correct service account, delete the other unused service accounts in
omninamespace (excluding thedefaultservice account).You can recreate the pod but do not create a new service accounts and do not use the default service account.
As far as I understand, serviceaccount have no privileges at all.
Serviceaccounts are bound using rolebindings to roles and these roles define the privileges that the bound serviceaccount would have.
So when I tested the question, it failed saying that the service account with the least privileges is frontend-default while infact, this serviceaccount is not bound to any role which means it has no privileges. Am I wrong in the way I see it?
This is the explanation for this question: