Within the challenge, requirement:
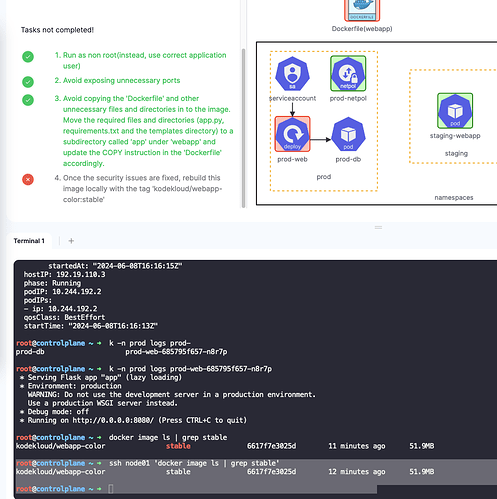
Once the security issues are fixed, rebuild this image locally with the tag ‘kodekloud/webapp-color:stable’
root@controlplane ~ ➜ docker image ls | grep stable
kodekloud/webapp-color stable 6617f7e3025d 11 minutes ago 51.9MB
root@controlplane ~ ➜ ssh node01 'docker image ls | grep stable'
kodekloud/webapp-color stable 6617f7e3025d 12 minutes ago 51.9MB
Pods have been successfully deployed with this image.
But check for this requirement is always failed. anything wrong with it?
What’s your YAML look like in the pods in the staging and dev namespaces? You not only have to rebuild the image; you also have to reference it in the two pods.
this image was adopted by pods in namespace ‘dev’ / ‘staging’
root@controlplane ~ ✖ k -n dev get pods dev-webapp -o json | jq '.spec.containers[].image'
"kodekloud/webapp-color:stable"
root@controlplane ~ ➜ k -n staging get pods staging-webapp -o json | jq '.spec.containers[].image'
"kodekloud/webapp-color:stable"
root@controlplane ~ ➜ cat dev-webapp.yaml | grep image
image: kodekloud/webapp-color:stable
imagePullPolicy: Never
root@controlplane ~ ➜ cat staging-webapp.yaml | grep image
image: kodekloud/webapp-color:stable
imagePullPolicy: Never
also has issue with another requirement:
The deployment has a secret hardcoded. Instead, create a secret called ‘prod-db’ for all the hardcoded values and consume the secret values as environment variables within the deployment.
root@controlplane ~ ➜ k -n prod get deployments.apps prod-web -o json | jq '.spec.template.spec.containers[].env'
[
{
"name": "DB_Host",
"valueFrom": {
"secretKeyRef": {
"key": "DB_Host",
"name": "prod-db"
}
}
},
{
"name": "DB_User",
"valueFrom": {
"secretKeyRef": {
"key": "DB_User",
"name": "prod-db"
}
}
},
{
"name": "DB_Password",
"valueFrom": {
"secretKeyRef": {
"key": "DB_Password",
"name": "prod-db"
}
}
}
]
root@controlplane ~ ➜ k -n prod get secrets prod-db -o yaml
apiVersion: v1
data:
DB_Host: cHJvZC1kYg==
DB_Password: cGFzd3Jk
DB_User: cm9vdAo=
kind: Secret
metadata:
creationTimestamp: "2024-06-08T16:11:51Z"
name: prod-db
namespace: prod
resourceVersion: "13449"
uid: 5e524ec5-f5f0-4e3a-af00-cf1a45648dd2
type: Opaque
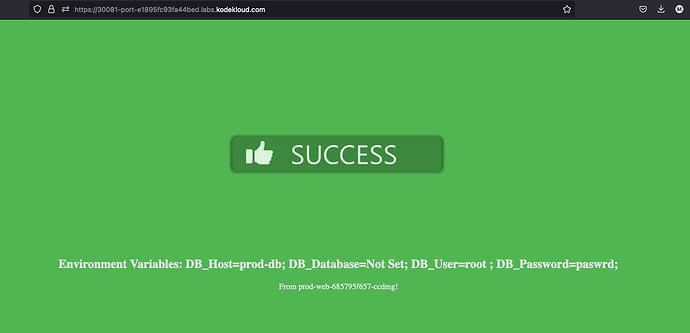
From web console test, all is fine
But check failed as shown in above screenshot.
The challenges, like all of our labs, use automatic graders, so sometimes a solution will work, but won’t be a solution that the grader programs recognize as correct. It’s worth checking the solutions in the KodeKloud CKS repo to see how your solution differs from the one the grader expects. At worse, you’ll learn a different way to solve the same problem than the one you used.