Hi Team, I am stuck at one of the Kubernetes Networking Question. Please help me if i am wrong:
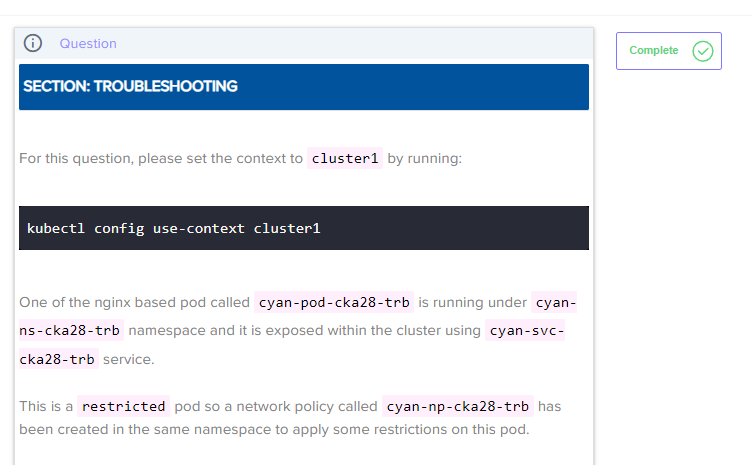
One of the nginx based pod called cyan-pod-cka28-trb is running under cyan-ns-cka28-trb namespace and it is exposed within the cluster using cyan-svc-cka28-trb service.
This is a restricted pod so a network policy called cyan-np-cka28-trb has been created in the same namespace to apply some restrictions on this pod.
Two other pods called cyan-white-cka28-trb1 and cyan-black-cka28-trb are also running in the default namespace.
The nginx based app running on the cyan-pod-cka28-trb pod is exposed internally on the default nginx port (80).
Expectation: This app should only be accessible from the cyan-white-cka28-trb1 pod.
Problem: This app is not accessible from anywhere.
Troubleshoot this issue and fix the connectivity as per the requirement listed above.
Note: You can exec into cyan-white-cka28-trb and cyan-black-cka28-trb pods and test connectivity using the curl utility.
You may update the network policy, but make sure it is not deleted from the cyan-ns-cka28-trb namespace.
Below is Solution from me :
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
creationTimestamp: “2023-10-24T06:43:34Z”
generation: 1
name: cyan-np-cka28-trb
namespace: cyan-ns-cka28-trb
resourceVersion: “4416”
uid: 83bb1453-325f-4f50-99d7-298a53e4c73b
spec:
egress:
- ports:
- port: 80
protocol: TCP
to:
- ipBlock:
cidr: 0.0.0.0/0
ingress:
- from:
- namespaceSelector:
matchLabels:
kubernetes.io/metadata.name: default
podSelector:
matchLabels:
app: cyan-white-cka28-trb
ports:
- port: 80
protocol: TCP
podSelector: {}
policyTypes:
- Ingress
- Egress
status: {}
====================================
Is it correct?
Hard to tell
since you didn't post it as code and all the formatting is lost!
This particular question is asked about so frequently that we have published a worked solution
ohh sorry, Let me post it as a snapshot.
What you need to do when posting YAML is to put it in a code block so that it is properly formatted text - not screenshot, and not like you did above
Type the three backticks above and below pasted YAML, then
```
apiVersion: networking.k8s.io/v1](http://networking.k8s.io/v1)
kind: NetworkPolicy
metadata:
creationTimestamp: “2023-10-24T06:43:34Z”
generation: 1
name: cyan-np-cka28-trb
namespace: cyan-ns-cka28-trb
resourceVersion: “4416”
uid: 83bb1453-325f-4f50-99d7-298a53e4c73b
```
will come out like this
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
creationTimestamp: “2023-10-24T06:43:34Z”
generation: 1
name: cyan-np-cka28-trb
namespace: cyan-ns-cka28-trb
resourceVersion: “4416”
uid: 83bb1453-325f-4f50-99d7-298a53e4c73b
Below is the Solution from myside. I think this is correct. Correct if i am wrong. Please verify Kodecloud Solution:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
creationTimestamp: "2023-10-24T17:31:52Z"
generation: 1
name: cyan-np-cka28-trb
namespace: cyan-ns-cka28-trb
resourceVersion: "4635"
uid: 85761821-bdff-4c01-a75d-8b3e7913b55e
spec:
egress:
- ports:
- port: 80
protocol: TCP
to:
- ipBlock:
cidr: 0.0.0.0/0
ingress:
- from:
- namespaceSelector:
matchLabels:
kubernetes.io/metadata.name: default
podSelector:
matchLabels:
app: cyan-white-cka28-trb
ports:
- port: 80
protocol: TCP
podSelector:
matchLabels:
app: cyan-app-cka28-trb
policyTypes:
- Ingress
- Egress
status: {}
That’s better! It is now legible and I can paste it to the labs!
Let me check it now.
Ok, your policy does work and it does correctly allow traffic from white and not from black. However you did change the egress policy which is not required to solve the question.
The explanation of the solution is in the link in the post above
1 Like