The Nautilus DevOps team has been tasked with demonstrating the use of VPC Peering to enable communication between two VPCs. One VPC will be a private VPC that contains a private EC2 instance, while the other will be the default public VPC containing a publicly accessible EC2 instance.
- There is already an existing EC2 instance in the public vpc/subnet:
- Name:
xfusion-public-ec2
- There is already an existing Private VPC:
- Name:
xfusion-private-vpc - CIDR:
10.1.0.0/16
- There is already an existing Subnet in
xfusion-private-vpc:
- Name:
xfusion-private-subnet - CIDR:
10.1.1.0/24
- There is already an existing EC2 instance in the private subnet:
- Name:
xfusion-private-ec2
- Create a Peering Connection between the Default VPC and the Private VPC:
- VPC Peering Connection Name:
xfusion-vpc-peering
- Configure Route Tables to enable communication between the two VPCs.
- Ensure the private EC2 instance is accessible from the public EC2 instance.
- Test the Connection:
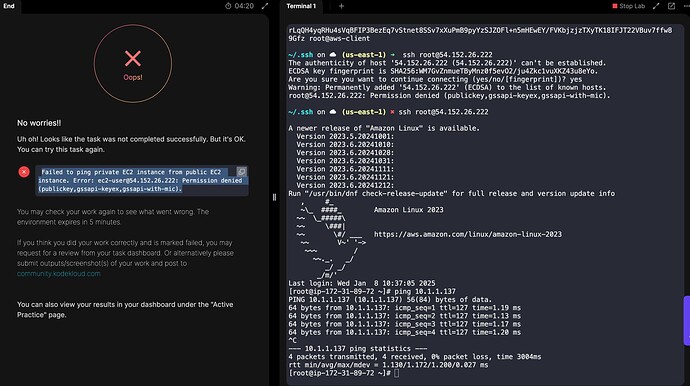
- Add
/root/.ssh/id_rsa.pubpublic key to the public EC2 instance’sec2-user’sauthorized_keysto make sure we are able to ssh into this instance from AWS client host. You may also need to update the security group of the private EC2 instance to allow ICMP traffic from the public/default VPC CIDR. This will enable you to ping the private instance from the public instance. - SSH into the public EC2 instance and ensure that you can ping the private EC2 instance.
Use below given AWS Credentials: (You can run the showcreds command on aws-client host to retrieve these credentials)
Console URL https://211125603807.signin.aws.amazon.com/consol
I was able to acheive almost 90% of the task
Can u help me on how to acheive this
7) Test the Connection:
- Add
/root/.ssh/id_rsa.pubpublic key to the public EC2 instance’sec2-user’sauthorized_keysto make sure we are able to ssh into this instance from AWS client host. You may also need to update the security group of the private EC2 instance to allow ICMP traffic from the public/default VPC CIDR. This will enable you to ping the private instance from the public instance.