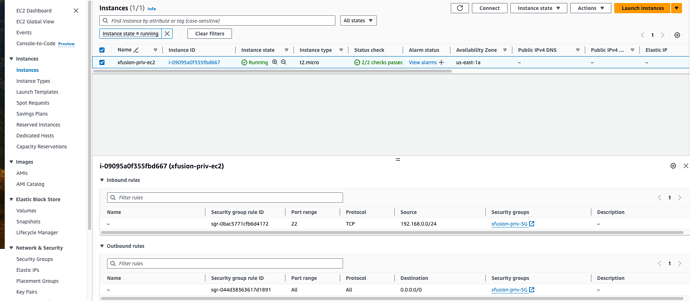
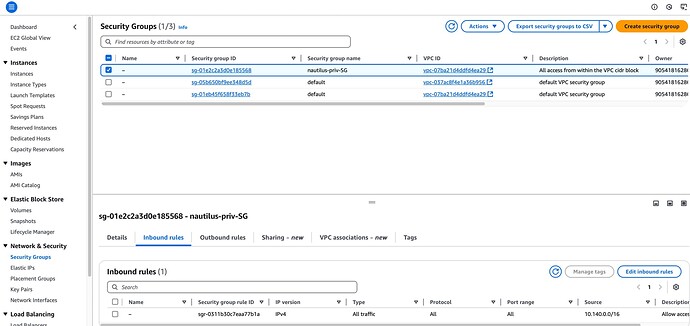
I’m having the same issue with this lab as well.
Current behaviour: Lab failed due to “The security group does not allow access from the VPC’s CIDR block”.
Private VPC and private subnet CIDR: 192.168.0.0/24
Private ACL:
- Inbound: Allow all from 192.168.0.0/24, priority 100
- Outbound: Allow all to 192.168.0.0/24, priority 100
Security group:
- 1 Inbound rule: Allow all traffic from 192.168.0.0/24
- 1 Outound rule: Allow all traffic to 192.168.0.0/24
Instance:
- Amazon Linux AMI with t2.micro free tier with no key pair.
I’m a bit lost here so any advice or clues towards the solution would be highly appreciated.
Thanks!
Additional information
$ aws ec2 describe-vpcs --vpc-ids vpc-03dbb92a274fd56f3
Summary
{
"Vpcs": [
{
"OwnerId": "590184057482",
"InstanceTenancy": "default",
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-02bcfffa1182dc90e",
"CidrBlock": "192.168.0.0/24",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": false,
"Tags": [
{
"Key": "Name",
"Value": "xfusion-priv-vpc"
}
],
"VpcId": "vpc-03dbb92a274fd56f3",
"State": "available",
"CidrBlock": "192.168.0.0/24",
"DhcpOptionsId": "dopt-0e7ffd6f34e1f7826"
}
]
}
$ aws ec2 describe-subnets --subnet-ids subnet-08950500b683c966d
Summary
{
"Subnets": [
{
"AvailabilityZoneId": "use1-az5",
"MapCustomerOwnedIpOnLaunch": false,
"OwnerId": "590184057482",
"AssignIpv6AddressOnCreation": false,
"Ipv6CidrBlockAssociationSet": [],
"Tags": [
{
"Key": "Name",
"Value": "xfusion-priv-subnet"
}
],
"SubnetArn": "arn:aws:ec2:us-east-1:590184057482:subnet/subnet-08950500b683c966d",
"EnableDns64": false,
"Ipv6Native": false,
"PrivateDnsNameOptionsOnLaunch": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
},
"SubnetId": "subnet-08950500b683c966d",
"State": "available",
"VpcId": "vpc-03dbb92a274fd56f3",
"CidrBlock": "192.168.0.0/24",
"AvailableIpAddressCount": 251,
"AvailabilityZone": "us-east-1f",
"DefaultForAz": false,
"MapPublicIpOnLaunch": false
}
]
}
$ aws ec2 describe-network-acls --network-acl-ids acl-045b011f3eb7938f7
Summary
{
"NetworkAcls": [
{
"Associations": [
{
"NetworkAclAssociationId": "aclassoc-032d5d96be391e758",
"NetworkAclId": "acl-045b011f3eb7938f7",
"SubnetId": "subnet-08950500b683c966d"
}
],
"Entries": [
{
"CidrBlock": "192.168.0.0/24",
"Egress": true,
"Protocol": "-1",
"RuleAction": "allow",
"RuleNumber": 100
},
{
"CidrBlock": "0.0.0.0/0",
"Egress": true,
"Protocol": "-1",
"RuleAction": "deny",
"RuleNumber": 32767
},
{
"CidrBlock": "192.168.0.0/24",
"Egress": false,
"Protocol": "-1",
"RuleAction": "allow",
"RuleNumber": 100
},
{
"CidrBlock": "0.0.0.0/0",
"Egress": false,
"Protocol": "-1",
"RuleAction": "deny",
"RuleNumber": 32767
}
],
"IsDefault": true,
"NetworkAclId": "acl-045b011f3eb7938f7",
"Tags": [],
"VpcId": "vpc-03dbb92a274fd56f3",
"OwnerId": "590184057482"
}
]
}
$ aws ec2 describe-route-tables --route-table-ids rtb-05490223b61fde3e5
Summary
{
"RouteTables": [
{
"Associations": [
{
"Main": true,
"RouteTableAssociationId": "rtbassoc-0467e6524f6fedbf3",
"RouteTableId": "rtb-05490223b61fde3e5",
"AssociationState": {
"State": "associated"
}
}
],
"PropagatingVgws": [],
"RouteTableId": "rtb-05490223b61fde3e5",
"Routes": [
{
"DestinationCidrBlock": "192.168.0.0/24",
"GatewayId": "local",
"Origin": "CreateRouteTable",
"State": "active"
}
],
"Tags": [],
"VpcId": "vpc-03dbb92a274fd56f3",
"OwnerId": "590184057482"
}
]
}
$ aws ec2 describe-security-groups --group-ids sg-04c576daac030d5a3
Summary
{
"SecurityGroups": [
{
"GroupId": "sg-04c576daac030d5a3",
"IpPermissionsEgress": [
{
"IpProtocol": "-1",
"UserIdGroupPairs": [],
"IpRanges": [
{
"CidrIp": "192.168.0.0/24"
}
],
"Ipv6Ranges": [],
"PrefixListIds": []
}
],
"VpcId": "vpc-03dbb92a274fd56f3",
"OwnerId": "590184057482",
"GroupName": "xfusion-priv-ec2-sc",
"Description": "Allows connection from/to the resources of the private VPC",
"IpPermissions": [
{
"IpProtocol": "-1",
"UserIdGroupPairs": [],
"IpRanges": [
{
"CidrIp": "192.168.0.0/24"
}
],
"Ipv6Ranges": [],
"PrefixListIds": []
}
]
}
]
}
$ aws ec2 describe-instances --instance-ids i-0141c37ce7a20360d
Summary
{
"Reservations": [
{
"ReservationId": "r-094910fa5f8f8d144",
"OwnerId": "590184057482",
"Groups": [],
"Instances": [
{
"Architecture": "x86_64",
"BlockDeviceMappings": [
{
"DeviceName": "/dev/xvda",
"Ebs": {
"AttachTime": "2025-01-17T15:42:08.000Z",
"DeleteOnTermination": true,
"Status": "attached",
"VolumeId": "vol-0e1ae864f1ae90b57"
}
}
],
"ClientToken": "2735df82-d138-4584-b959-9fb19dfaf87a",
"EbsOptimized": false,
"EnaSupport": true,
"Hypervisor": "xen",
"NetworkInterfaces": [
{
"Attachment": {
"AttachTime": "2025-01-17T15:42:08.000Z",
"AttachmentId": "eni-attach-04cc69348b98d5f2c",
"DeleteOnTermination": true,
"DeviceIndex": 0,
"Status": "attached",
"NetworkCardIndex": 0
},
"Description": "",
"Groups": [
{
"GroupId": "sg-04c576daac030d5a3",
"GroupName": "xfusion-priv-ec2-sc"
}
],
"Ipv6Addresses": [],
"MacAddress": "16:ff:e5:48:90:e3",
"NetworkInterfaceId": "eni-068c21de8b07f6023",
"OwnerId": "590184057482",
"PrivateIpAddress": "192.168.0.242",
"PrivateIpAddresses": [
{
"Primary": true,
"PrivateIpAddress": "192.168.0.242"
}
],
"SourceDestCheck": true,
"Status": "in-use",
"SubnetId": "subnet-08950500b683c966d",
"VpcId": "vpc-03dbb92a274fd56f3",
"InterfaceType": "interface"
}
],
"RootDeviceName": "/dev/xvda",
"RootDeviceType": "ebs",
"SecurityGroups": [
{
"GroupId": "sg-04c576daac030d5a3",
"GroupName": "xfusion-priv-ec2-sc"
}
],
"SourceDestCheck": true,
"Tags": [
{
"Key": "Name",
"Value": "xfusion-priv-ec2"
}
],
"VirtualizationType": "hvm",
"CpuOptions": {
"CoreCount": 1,
"ThreadsPerCore": 1
},
"CapacityReservationSpecification": {
"CapacityReservationPreference": "open"
},
"HibernationOptions": {
"Configured": false
},
"MetadataOptions": {
"State": "applied",
"HttpTokens": "required",
"HttpPutResponseHopLimit": 2,
"HttpEndpoint": "enabled",
"HttpProtocolIpv6": "disabled",
"InstanceMetadataTags": "disabled"
},
"EnclaveOptions": {
"Enabled": false
},
"BootMode": "uefi-preferred",
"PlatformDetails": "Linux/UNIX",
"UsageOperation": "RunInstances",
"UsageOperationUpdateTime": "2025-01-17T15:42:08.000Z",
"PrivateDnsNameOptions": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
},
"MaintenanceOptions": {
"AutoRecovery": "default"
},
"CurrentInstanceBootMode": "legacy-bios",
"InstanceId": "i-0141c37ce7a20360d",
"ImageId": "ami-0df8c184d5f6ae949",
"State": {
"Code": 16,
"Name": "running"
},
"PrivateDnsName": "ip-192-168-0-242.ec2.internal",
"PublicDnsName": "",
"StateTransitionReason": "",
"AmiLaunchIndex": 0,
"ProductCodes": [],
"InstanceType": "t2.micro",
"LaunchTime": "2025-01-17T15:42:08.000Z",
"Placement": {
"GroupName": "",
"Tenancy": "default",
"AvailabilityZone": "us-east-1f"
},
"Monitoring": {
"State": "disabled"
},
"SubnetId": "subnet-08950500b683c966d",
"VpcId": "vpc-03dbb92a274fd56f3",
"PrivateIpAddress": "192.168.0.242"
}
]
}
]
}