Basavraj Devpuje:
A small question for clarification:
If we have a ClusterRole to read Secrets: (which is a namespaced resource)
apiVersion: <http://rbac.authorization.k8s.io/v1|rbac.authorization.k8s.io/v1>
kind: ClusterRole
metadata:
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "watch", "list"]
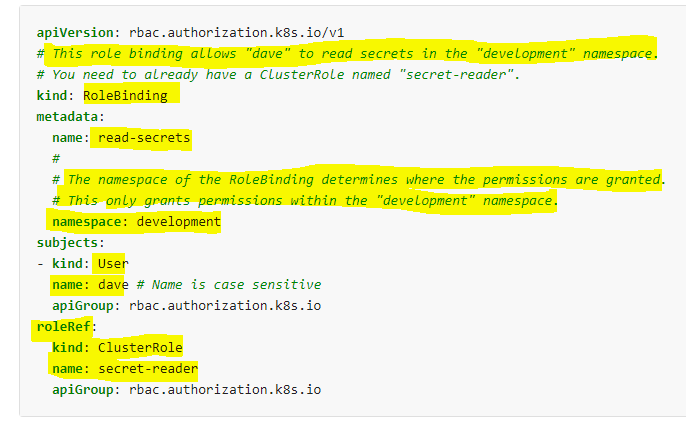
And have a RoleBinding referring to the ClusterRole
apiVersion: <http://rbac.authorization.k8s.io/v1|rbac.authorization.k8s.io/v1>
kind: RoleBinding
metadata:
name: read-secrets
namespace: development
subjects:
- kind: User
name: sam
apiGroup: <http://rbac.authorization.k8s.io|rbac.authorization.k8s.io>
roleRef:
kind: ClusterRole
name: secret-reader
apiGroup: <http://rbac.authorization.k8s.io|rbac.authorization.k8s.io>
Here the RoleBinding is referring to the ClusterRole for secrets which is a “namespaced” resource (secret).
Does this mean the user can read the Secrets from ALL NAMESPACES? (As we can’t specify namespaces in ClusterRole) though the namespace: developement is mentioned in RoleBinding.