Starting from October 10, 2024, the Certified Kubernetes Security Specialist (CKS) exam will undergo several significant updates to ensure that certified professionals possess the most current skills to secure Kubernetes environments. The changes, aimed at keeping pace with evolving security practices, are reflected across all domains of the exam. These updates are critical for candidates looking to ensure they are equipped to handle the security challenges in modern Kubernetes environments.
This post will outline each domain of the updated CKS exam, detailing what’s new and what to focus on in preparation for the exam. The goal is to provide a clear understanding of the updates and help candidates effectively plan their study strategy.
Before moving on, you can watch the full video that explains the changes in the CKS certification domains here.
Certified Kubernetes Security Specialist (CKS)
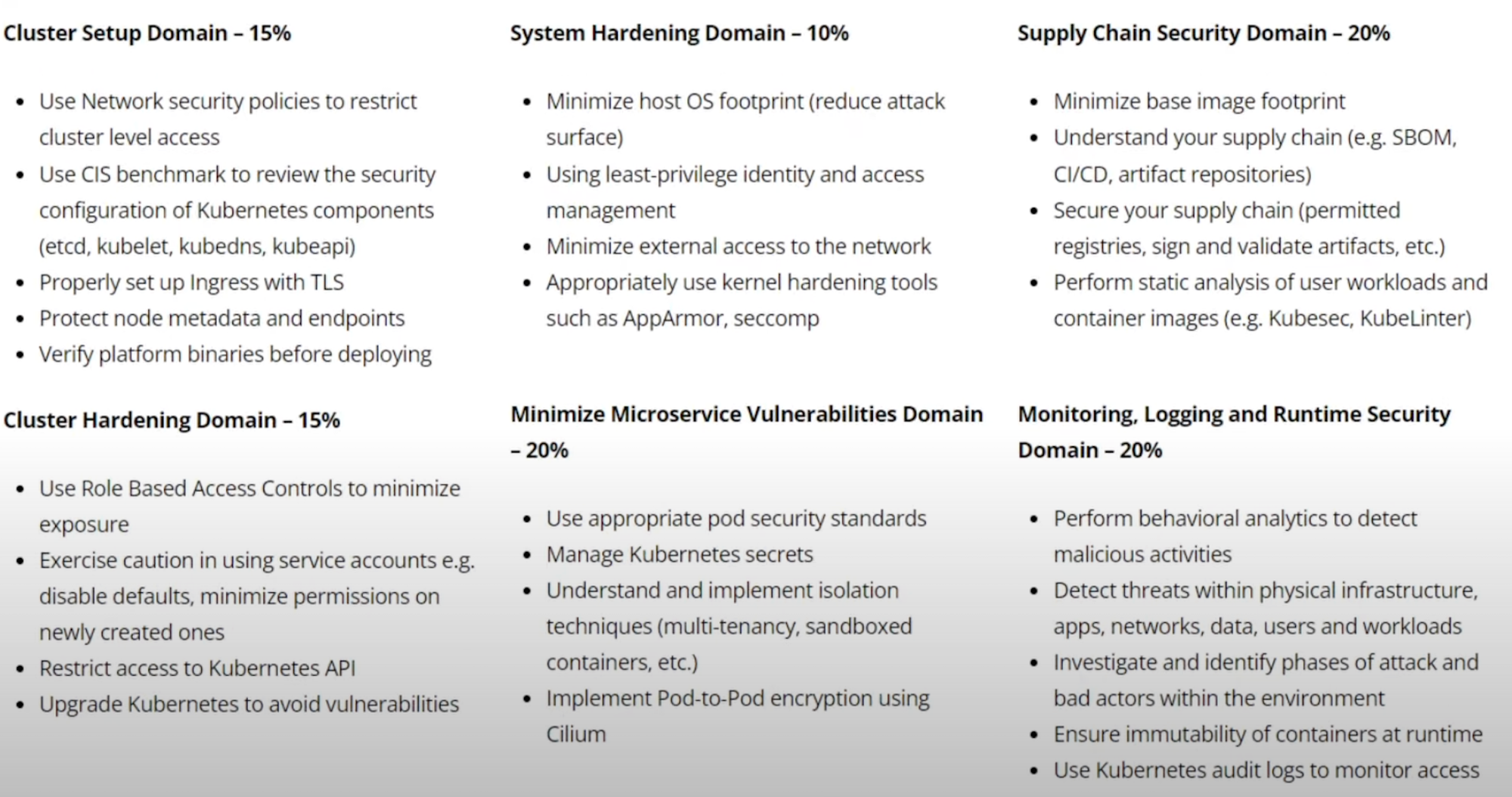
1. Cluster Setup Domain Updates (Weightage Increased from 10% to 15%)
The Cluster Setup domain sees a notable increase in its weight from 10% to 15%, indicating its growing importance in securing Kubernetes clusters.
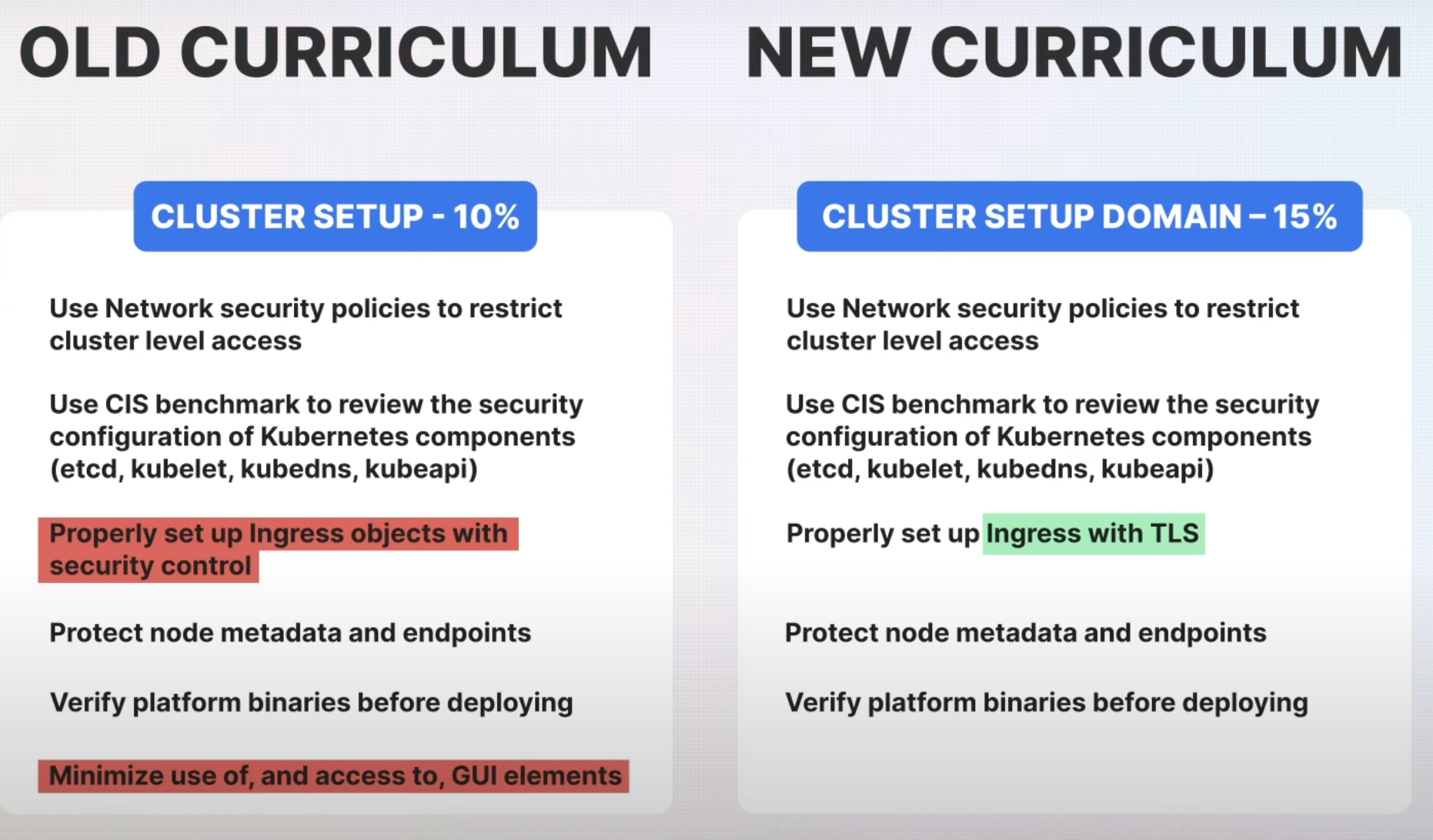
- Network Security Policies: The focus on configuring network security policies to restrict cluster-level access continues. This practice remains essential for isolating and protecting the Kubernetes cluster from unauthorized access.
- CIS Benchmarks: Using CIS (Center for Internet Security) benchmarks to review the security configurations of key Kubernetes components (such as etcd, kubelet, kubeapi, and kubedns) is still a critical component of this domain. Adhering to these benchmarks ensures the cluster is secured according to industry standards.
- Ingress Setup with TLS: One of the major updates is the emphasis on setting up ingress with Transport Layer Security (TLS). TLS is essential for encrypting data in transit and ensuring secure communication between services and clients.
- Node Metadata Protection: Protecting node metadata and endpoints remains a priority, with the continued recommendation to verify platform binaries before deployment. However, the previous guideline to minimize GUI access has been removed, shifting the focus towards more specific and actionable security measures.
2. Cluster Hardening Domain (15% Weightage, No Major Changes)
The Cluster Hardening domain remains critical in protecting the Kubernetes cluster from potential threats, with its weight unchanged at 15%.
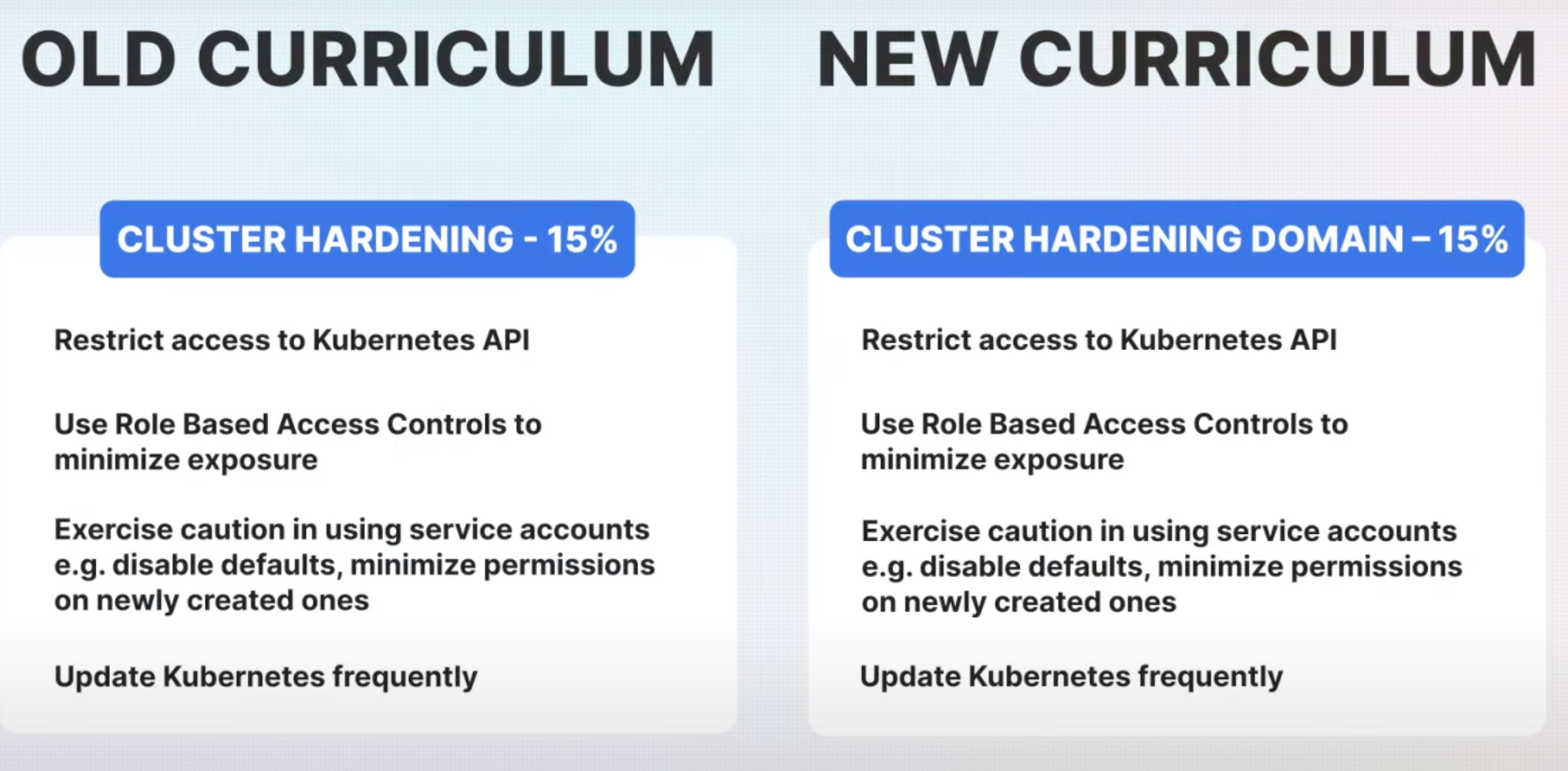
- Restricting API Access: This domain emphasizes restricting access to the Kubernetes API to ensure that only authorized users can interact with the cluster.
- RBAC Policies: The use of Role-Based Access Controls (RBAC) is encouraged to minimize exposure and ensure that users and services have only the necessary permissions.
- Service Account Management: Managing service accounts carefully is still critical, as they can be a potential attack vector if misconfigured.
- Frequent Kubernetes Updates: Keeping the Kubernetes version up to date is emphasized to avoid vulnerabilities that could be exploited in older versions.
Overall, no major changes are introduced here, but the importance of strong role-based access and API control cannot be understated.
3. System Hardening Domain (Weightage Reduced from 15% to 10%)
The System Hardening domain focuses on reducing the attack surface at the system level, with a slight reduction in its weight from 15% to 10%. However, the key practices remain consistent with the previous curriculum.
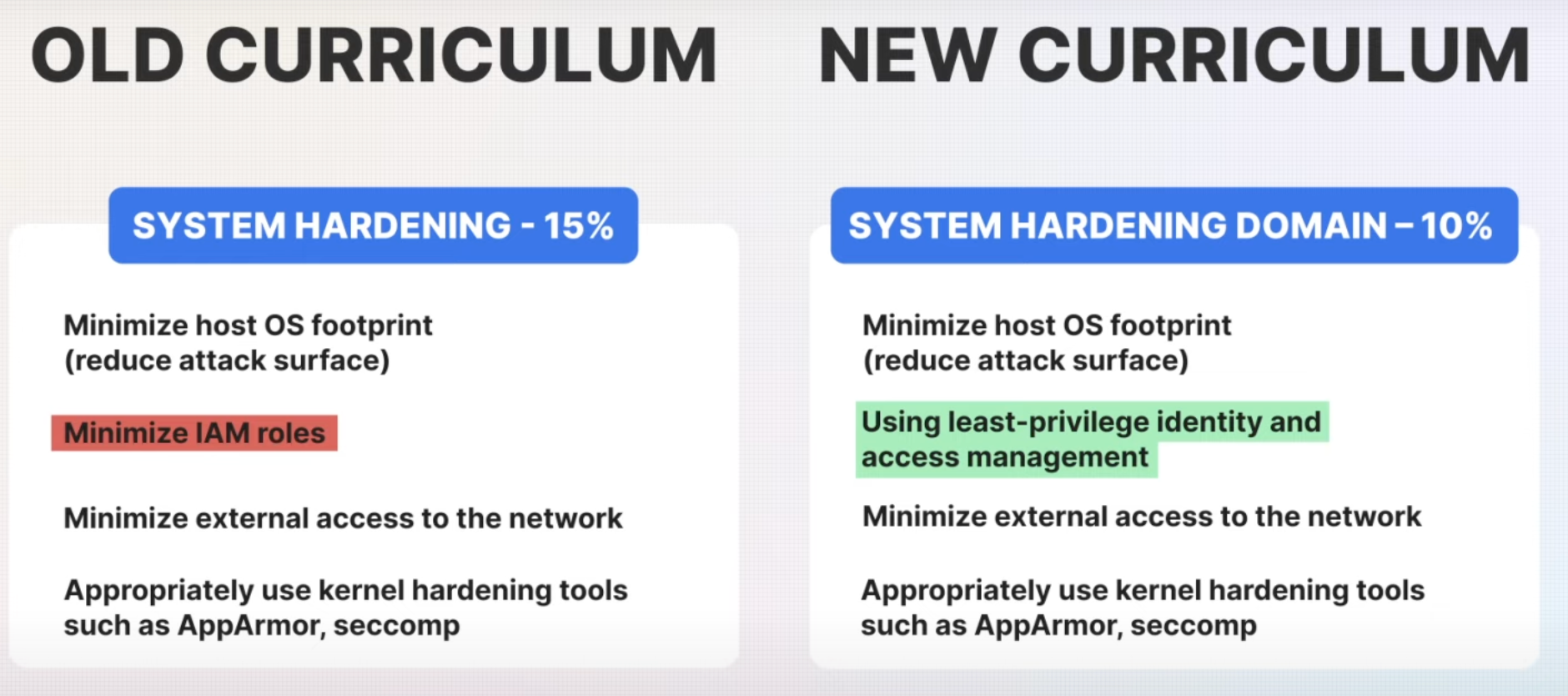
- Minimizing OS Footprint: Reducing the host operating system (OS) footprint to essential components remains a best practice. This helps in eliminating unnecessary software that could be exploited by attackers.
- Least-Privilege IAM: The previous guidance on minimizing IAM roles has been refined to emphasize the principle of least-privilege identity and access management (IAM). This ensures that users and services only have the permissions necessary to perform their tasks.
- Restricting Network Access: Minimizing external access to the cluster’s network reduces the risk of external attacks.
- Kernel Hardening Tools: The use of tools like AppArmor and seccomp continues to be a crucial practice for enforcing security policies that limit the capabilities of processes running on the system.
4. Minimizing Microservice Vulnerabilities (20% Weightage)
The Minimizing Microservice Vulnerabilities domain retains its weight at 20%, but several key updates have been introduced to align with modern security practices.
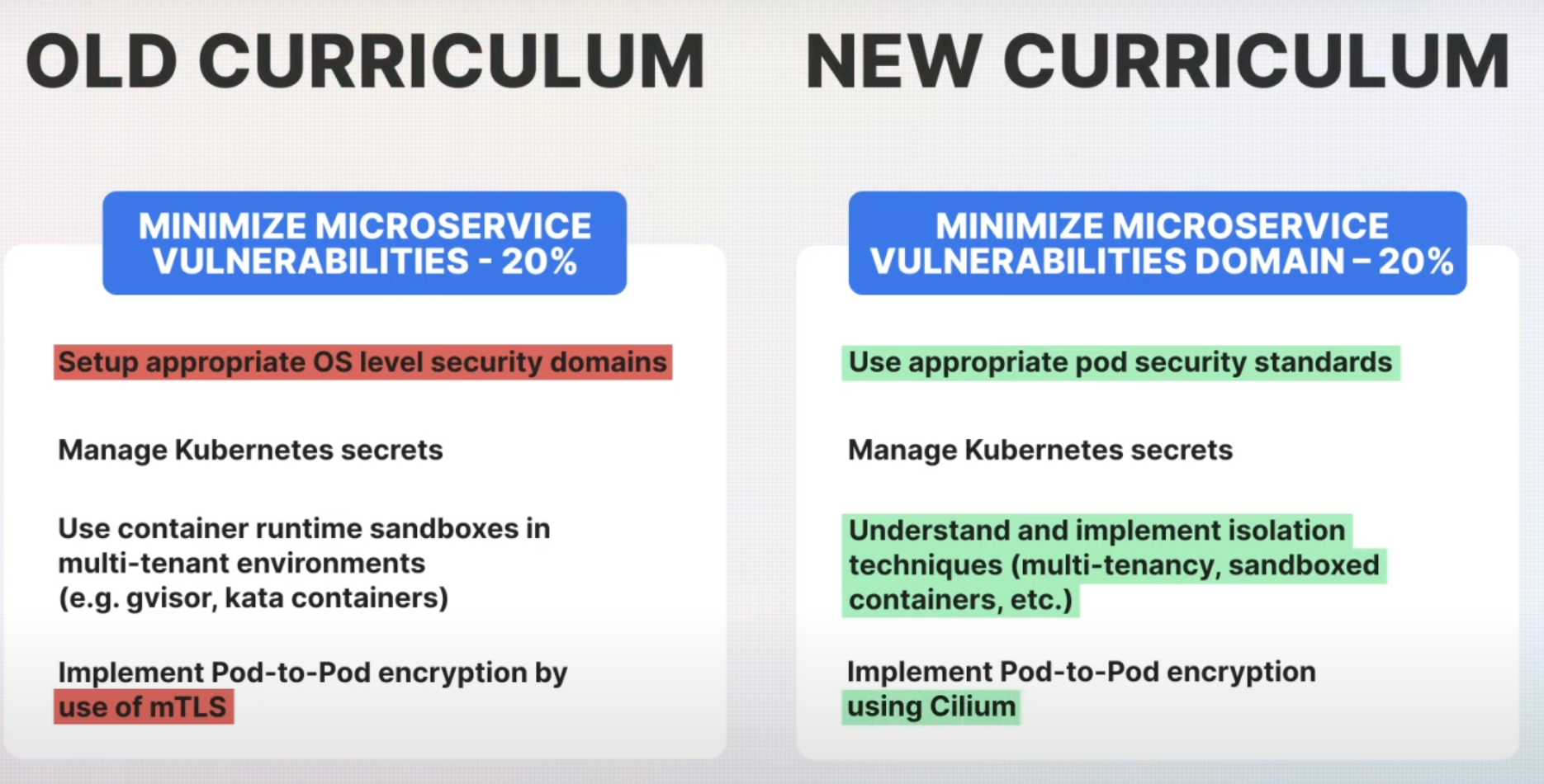
- Pod Security Standards: A shift in focus from OS-level security domains to using pod security standards is a significant change. Pod security standards define policies that restrict what pods can do, ensuring they operate with the least privilege required.
- Managing Kubernetes Secrets: Managing Kubernetes secrets securely remains essential. This involves securely storing and accessing sensitive information like API keys, tokens, and passwords.
- Isolation Techniques: The recommendation to use container runtime sandboxes has been expanded to a broader focus on implementing isolation techniques. This includes using multi-tenancy and sandboxed containers, among other methods.
- Pod-to-Pod Encryption with Cilium: Another important update is the specific mention of using Cilium for pod-to-pod encryption. Cilium enhances Kubernetes security by providing advanced networking and security policies, including robust encryption capabilities.
5. Supply Chain Security (20% Weightage)
The Supply Chain Security domain remains critical with a consistent weightage of 20%. Several updates have been made to incorporate modern tools and methodologies.
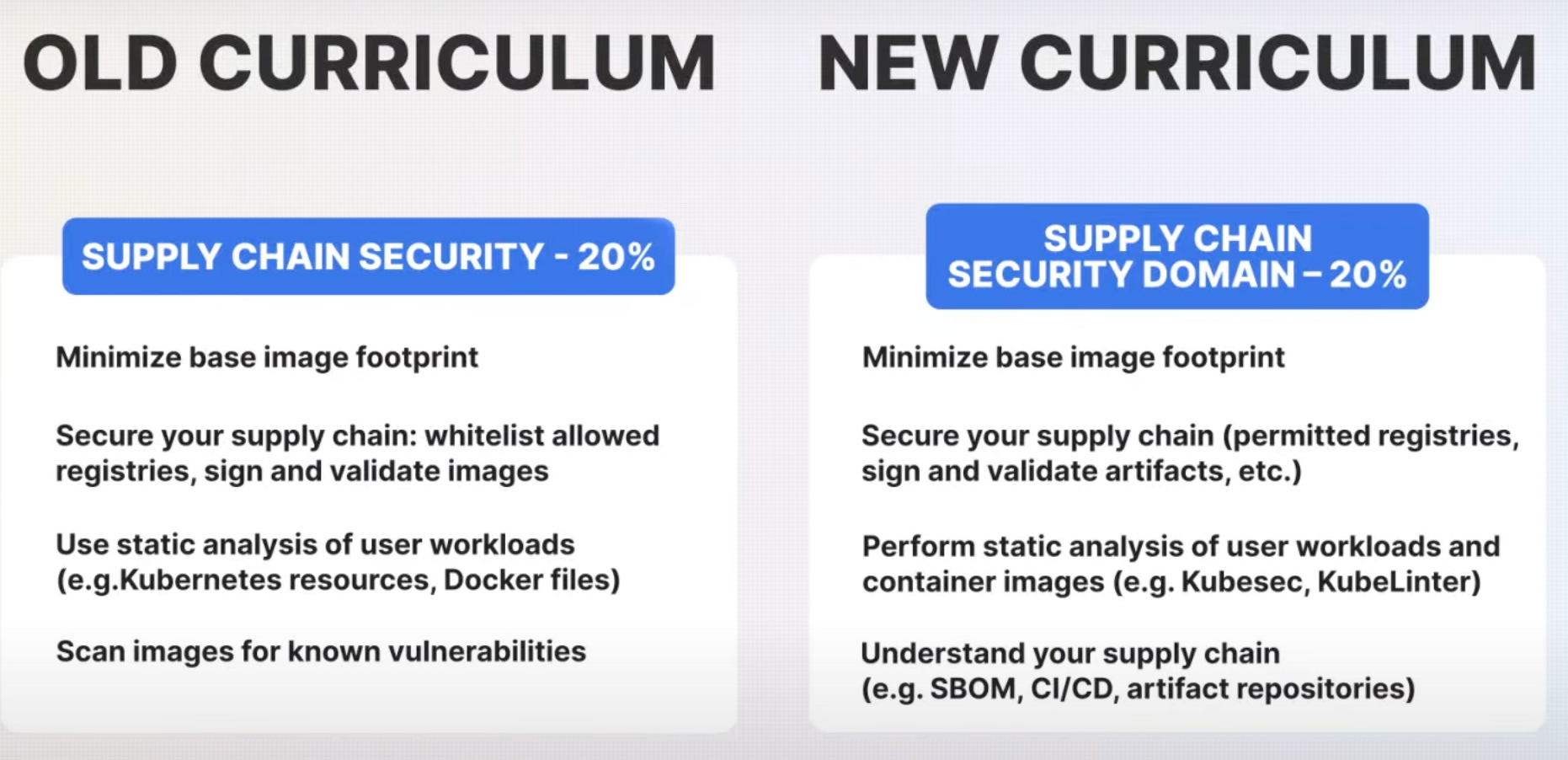
- Software Bill of Materials (SBOM): A significant addition is the focus on understanding the software bill of materials (SBOM). An SBOM is a detailed list of all components within a software product, helping in identifying vulnerabilities in third-party components.
- Kubesec and KubeLinter: Tools like Kubesec and KubeLinter have been introduced to enhance the security of Kubernetes configurations. Kubesec evaluates resource configurations for best practices, while KubeLinter analyzes YAML files and Helm charts for potential security risks.
- CI/CD Security: Securing the CI/CD pipeline is emphasized, ensuring that software builds and deployments are secure from vulnerabilities.
6. Monitoring, Logging, and Runtime Security (20% Weightage)
The Monitoring, Logging, and Runtime Security domain retains its weight at 20%, with slight rewording but no major changes. This domain is essential for maintaining the security and integrity of a Kubernetes environment through comprehensive monitoring and logging practices.
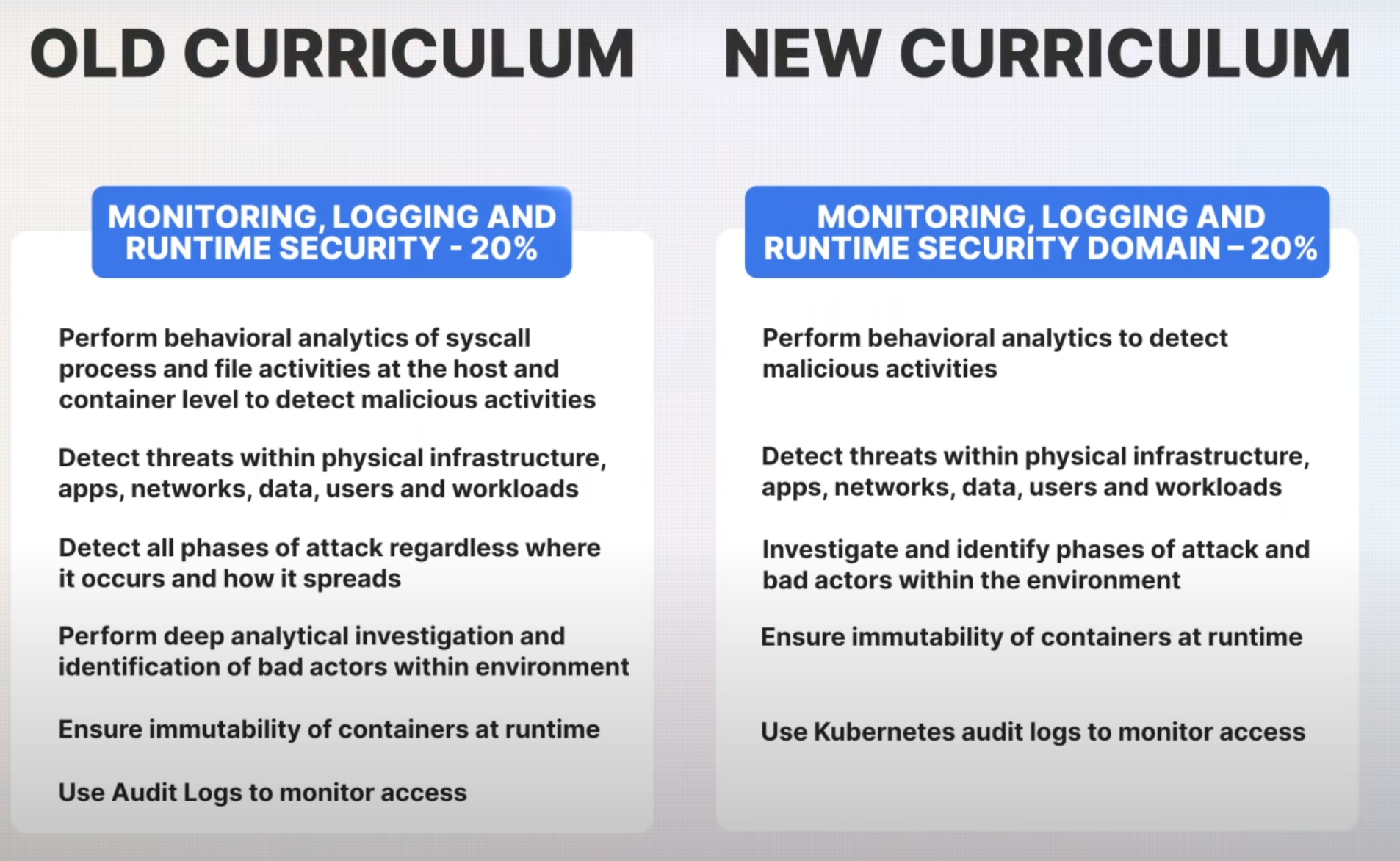
- Behavioral Analytics: Monitoring system calls, processes, and file activities at the host and container levels helps in detecting malicious activities.
- Threat Detection: Detecting threats in physical infrastructure, applications, networks, and data is crucial for comprehensive security.
- Audit Logs: The use of audit logs to monitor access and detect security breaches continues to be a key component in securing Kubernetes environments.
You might be interested in reading the following related to Kubernetes Audit Logs.

Kubectl Logs
New Prerequisite Requirements for CKS Exam
One important administrative change to the CKS exam is the new prerequisite requirements. Starting from October 10, 2024, candidates are no longer required to have an active Certified Kubernetes Administrator (CKA) certification. It is now sufficient to have passed the CKA at any point in the past, even if the certification has expired. This change simplifies the qualification process for scheduling the CKS exam.
Ace the Updated CKS Exam with KodeKloud's Comprehensive Course
To help you prepare for the Certified Kubernetes Security Specialist (CKS) exam changes, KodeKloud has fully updated its CKS course to align with the new curriculum. The course which is considered to be the best CKS course for Kubernetes security certification, is designed to ensure you are equipped with the latest Kubernetes security skills required to secure modern cloud-native environments effectively.

Kubernetes Security Certification - CKS
Here's what you can expect from KodeKloud’s updated CKS course:
- Complete Coverage of Updated Domains: The course addresses all key areas of the new CKS exam, including Cluster Setup, Cluster Hardening, System Hardening, Minimizing Microservice Vulnerabilities, Supply Chain Security, and Monitoring and Runtime Security. This ensures you are well-prepared for each exam domain.
- Hands-On Lab Exercises: Practical labs focus on real-world Kubernetes security best practices like configuring network security policies, implementing TLS encryption, managing pod security standards, and using tools like Cilium, Kubesec, and KubeLinter.
- Mock Exams: Simulated CKS mock exams will help you test your knowledge and experience a real-world exam environment, preparing you for success on the actual test day.
- Prerequisite Knowledge: The course includes foundational content to ensure you grasp essential Kubernetes concepts before diving into advanced security topics.
It is recommended to take the CKA course and certification before this one if you are new to Kubernetes and the CKS certification.

CKA exam Preparation
By taking this Kubernetes security certification course, candidates will gain the practical knowledge needed to pass the CKS exam and excel in securing Kubernetes clusters in production environments. The course is designed to help professionals enhance their Kubernetes security expertise while covering every topic required for the certification exam.
Stay ahead of the curve with KodeKloud’s latest CKS training and gain the skills to become a certified expert in Kubernetes security.
Don’t miss out on this opportunity! Enroll today using the link provided and start your journey towards becoming a Certified Kubernetes Security Specialist.
Once you pass your certification, be sure to share your achievement with us and the KodeKloud community on social media!
Good luck with your preparations and certification!


















Discussion