Kodekloud Engineer:
Terrform Level 4, Task 2 with title Implementing Local Variables Using Terraform
lab link: https://engineer.kodekloud.com/task?id=690aee0fb572684d84d32aa3
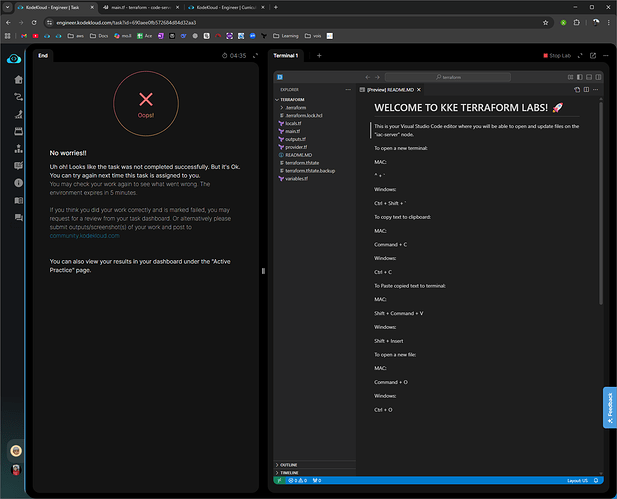
fails without giving any feedback
Thanks for your detailed feedback. It is a valid issue, and the team is working on it. I’ll keep you updated.
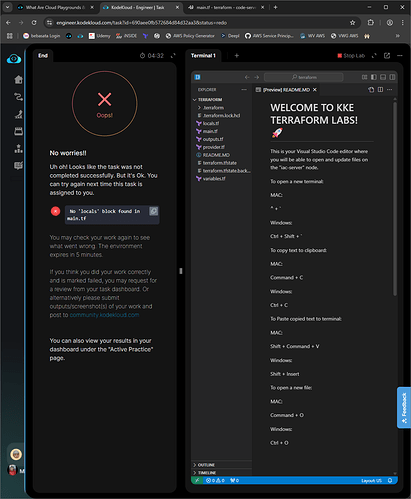
First I have a feedback that locals block should be in the main.tf despite it’s not stated in the task (I’ve created a separate file for it )
then I moved it to the main.tf, and again failed without any feedback
locals {
project = “xfusion”
environment = “dev”
prefix = “${local.project}-${local.environment}”
tags = {
Project = local.prefix
Environment = local.environment
Owner = “Moustafa”
Team = “Moustafa”
}
}
resource “aws_sns_topic” “user_updates” {
name = “${local.prefix}-topic”
tags = merge(local.tags, {
Name = “${local.prefix}-topic”
})
}
resource “aws_sqs_queue” “user_updates_queue” {
name = “${local.prefix}-queue”
tags = merge(local.tags, {
Name = “${local.prefix}-queue”
})
}
resource “aws_sns_topic_subscription” “user_updates_sqs_target” {
topic_arn = aws_sns_topic.user_updates.arn
protocol = “sqs”
endpoint = aws_sqs_queue.user_updates_queue.arn
depends_on = [aws_sns_topic.user_updates]
}
resource “aws_dynamodb_table” “basic-dynamodb-table” {
name = “${local.prefix}-events”
billing_mode = “PROVISIONED”
read_capacity = 5
write_capacity = 5
hash_key = “event_id”
attribute {
name = “event_id”
type = “S”
}
tags = merge(local.tags, {
Name = “${local.prefix}-events”
})
}
resource “aws_iam_role” “iam_role” {
name = “${local.prefix}-role”
assume_role_policy = jsonencode({
Version = “2012-10-17”
Statement = [
{
Action = “sts:AssumeRole”
Effect = “Allow”
Sid = “”
Principal = {
Service = “ec2.amazonaws.com”
}
},
]
})
dynamic “inline_policy” {
for_each = zipmap(range(length(var.KKE_IAM_ACTIONS)), var.KKE_IAM_ACTIONS)
content {
name = “test${inline_policy.key}”
policy = <<EOT
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Action”: [
“${inline_policy.value}”
],
“Effect”: “Allow”,
“Resource”: “*”
}
]
}
EOT
}
}
tags = merge(local.tags, {
Name = “${local.prefix}-role”
})
}
resource “aws_cloudwatch_metric_alarm” “foobar” {
alarm_name = “${local.prefix}-alarm”
comparison_operator = “GreaterThanOrEqualToThreshold”
evaluation_periods = 2
metric_name = “ApproximateNumberOfMessagesVisible”
namespace = “AWS/SQS”
period = 120
statistic = “Average”
threshold = 50
alarm_description = “Numbe of messages in the queue”
insufficient_data_actions = []
tags = merge(local.tags, {
Name = “${local.prefix}-alarm”
})
}
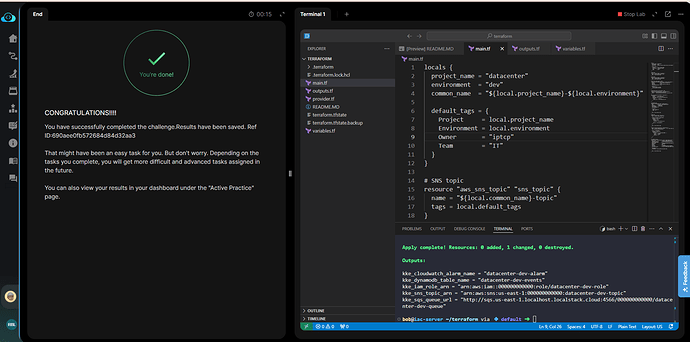
I’m experiencing the same issue with your main.tf. The cause is unclear, but it may be related to validation. I will follow up with the team. Meanwhile, please use my solution and try again.
locals {
project_name = "datacenter"
environment = "dev"
common_name = "${local.project_name}-${local.environment}"
default_tags = {
Project = local.project_name
Environment = local.environment
Owner = "iptcp"
Team = "IT"
}
}
# SNS topic
resource "aws_sns_topic" "sns_topic" {
name = "${local.common_name}-topic"
tags = local.default_tags
}
# SQS queue
resource "aws_sqs_queue" "sqs_queue" {
name = "${local.common_name}-queue"
tags = local.default_tags
}
# SNS topic subscription to SQS
resource "aws_sns_topic_subscription" "queue_subscription" {
endpoint = aws_sqs_queue.sqs_queue.arn
protocol = "sqs"
topic_arn = aws_sns_topic.sns_topic.arn
raw_message_delivery = true
depends_on = [
aws_sns_topic.sns_topic,
aws_sqs_queue.sqs_queue
]
}
# SQS queue policy to allow SNS -> SQS
resource "aws_sqs_queue_policy" "sqs_queue_policy" {
queue_url = aws_sqs_queue.sqs_queue.url
policy = data.aws_iam_policy_document.sqs_policy.json
}
data "aws_iam_policy_document" "sqs_policy" {
statement {
actions = ["SQS:SendMessage"]
resources = [aws_sqs_queue.sqs_queue.arn]
principals {
type = "Service"
identifiers = ["sns.amazonaws.com"]
}
}
}
# DynamoDB Table
resource "aws_dynamodb_table" "dynamo_table" {
name = "${local.common_name}-events"
hash_key = "event_id"
billing_mode = "PROVISIONED"
read_capacity = 5
write_capacity = 5
attribute {
name = "event_id"
type = "S"
}
tags = local.default_tags
}
# IAM role
resource "aws_iam_role" "iam_role" {
name = "${local.common_name}-role"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [{
Effect = "Allow"
Principal = {
Service = "sns.amazonaws.com"
}
Action = "sts:AssumeRole"
}]
})
tags = local.default_tags
}
resource "aws_iam_role_policy" "inline_policy" {
name = "${local.common_name}-policy"
role = aws_iam_role.iam_role.id
policy = jsonencode({
Version = "2012-10-17"
Statement = [
for action in var.KKE_IAM_ACTIONS : {
Effect = "Allow"
Action = action
Resource = "*"
}
]
})
}
# CloudWatch alarm
resource "aws_cloudwatch_metric_alarm" "queue_depth_alarm" {
alarm_name = "${local.common_name}-alarm"
comparison_operator = "GreaterThanOrEqualToThreshold"
evaluation_periods = 1
metric_name = "ApproximateNumberOfMessagesVisible"
namespace = "AWS/SQS"
period = 60
statistic = "Maximum"
threshold = var.KKE_QUEUE_DEPTH_THRESHOLD
alarm_description = "Alarm for SQS queue depth exceeding threshold"
dimensions = {
QueueName = aws_sqs_queue.sqs_queue.name
}
tags = local.default_tags
}