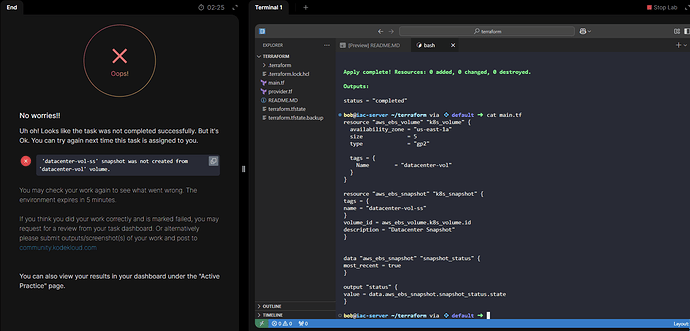
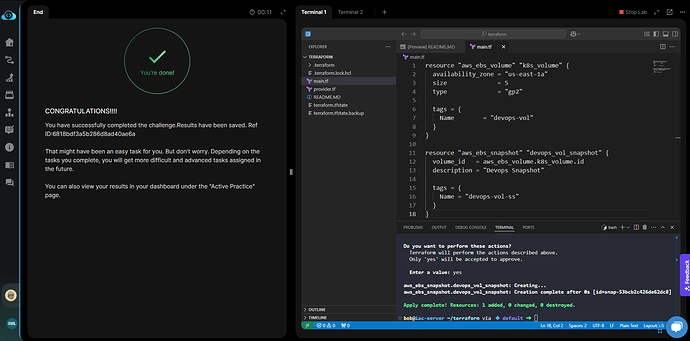
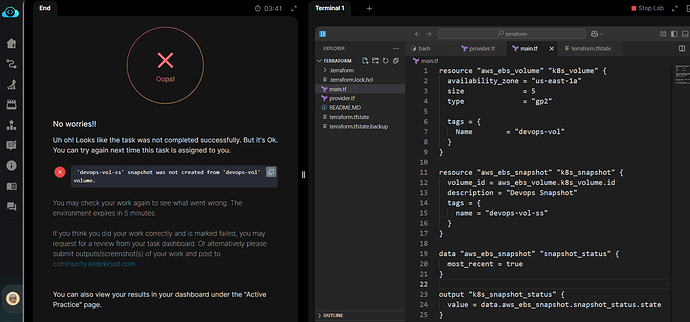
I believe there’s an issue with this one as you can clearly see the main.tf file and that the ID was referenced from the previously created volume, and that the “status” was “Completed”.
Hi @besnija,
It’s working properly on my end. Please make sure the snapshot’s name and description are correct.
Create a snapshot of an existing volume named devops-vol in us-east-1 region using terraform.
-
The name of the snapshot must be
devops-vol-ss. -
The description must be
Devops Snapshot. -
Make sure the snapshot status is
completedbefore submitting the task.
terraform state list
data.aws_ebs_snapshot.snapshot_status
aws_ebs_snapshot.k8s_snapshot
aws_ebs_volume.k8s_volume
bob@iac-server ~/terraform via 💠 default ➜ terraform show
# data.aws_ebs_snapshot.snapshot_status:
data "aws_ebs_snapshot" "snapshot_status" {
arn = "arn:aws:ec2:us-east-1::snapshot/snap-2a1a31d2a527e7f8b"
data_encryption_key_id = null
description = "Auto-created snapshot for AMI ami-03cf127a"
encrypted = false
id = "snap-2a1a31d2a527e7f8b"
kms_key_id = null
most_recent = true
outpost_arn = null
owner_alias = null
owner_id = "801119661308"
snapshot_id = "snap-2a1a31d2a527e7f8b"
start_time = "2025-06-13T14:13:05Z"
state = "completed"
storage_tier = null
tags = {}
volume_id = "vol-367a1e4d9be6870e2"
volume_size = 15
}
# aws_ebs_snapshot.k8s_snapshot:
resource "aws_ebs_snapshot" "k8s_snapshot" {
arn = "arn:aws:ec2:us-east-1::snapshot/snap-a871fbf915572b207"
data_encryption_key_id = null
description = "Devops Snapshot"
encrypted = false
id = "snap-a871fbf915572b207"
kms_key_id = null
outpost_arn = null
owner_alias = null
owner_id = "000000000000"
storage_tier = null
tags = {
"name" = "devops-vol-ss"
}
tags_all = {
"name" = "devops-vol-ss"
}
volume_id = "vol-f08bff3a29b2d4886"
volume_size = 5
}
# aws_ebs_volume.k8s_volume:
resource "aws_ebs_volume" "k8s_volume" {
arn = "arn:aws:ec2:us-east-1::volume/vol-f08bff3a29b2d4886"
availability_zone = "us-east-1a"
encrypted = false
final_snapshot = false
id = "vol-f08bff3a29b2d4886"
iops = 0
kms_key_id = null
multi_attach_enabled = false
outpost_arn = null
size = 5
snapshot_id = null
tags = {
"Name" = "devops-vol"
}
tags_all = {
"Name" = "devops-vol"
}
throughput = 0
type = "gp2"
}
Outputs:
k8s_snapshot_status = "completed"
tf.state full
{
"version": 4,
"terraform_version": "1.11.0",
"serial": 3,
"lineage": "816f0721-05ba-5226-e50c-187efbe06d00",
"outputs": {
"k8s_snapshot_status": {
"value": "completed",
"type": "string"
}
},
"resources": [
{
"mode": "data",
"type": "aws_ebs_snapshot",
"name": "snapshot_status",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"arn": "arn:aws:ec2:us-east-1::snapshot/snap-2a1a31d2a527e7f8b",
"data_encryption_key_id": "",
"description": "Auto-created snapshot for AMI ami-03cf127a",
"encrypted": false,
"filter": null,
"id": "snap-2a1a31d2a527e7f8b",
"kms_key_id": "",
"most_recent": true,
"outpost_arn": "",
"owner_alias": "",
"owner_id": "801119661308",
"owners": null,
"restorable_by_user_ids": null,
"snapshot_id": "snap-2a1a31d2a527e7f8b",
"snapshot_ids": null,
"start_time": "2025-06-13T14:13:05Z",
"state": "completed",
"storage_tier": "",
"tags": {},
"timeouts": null,
"volume_id": "vol-367a1e4d9be6870e2",
"volume_size": 15
},
"sensitive_attributes": []
}
]
},
{
"mode": "managed",
"type": "aws_ebs_snapshot",
"name": "k8s_snapshot",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"arn": "arn:aws:ec2:us-east-1::snapshot/snap-a871fbf915572b207",
"data_encryption_key_id": "",
"description": "Devops Snapshot",
"encrypted": false,
"id": "snap-a871fbf915572b207",
"kms_key_id": "",
"outpost_arn": "",
"owner_alias": "",
"owner_id": "000000000000",
"permanent_restore": null,
"storage_tier": "",
"tags": {
"name": "devops-vol-ss"
},
"tags_all": {
"name": "devops-vol-ss"
},
"temporary_restore_days": null,
"timeouts": null,
"volume_id": "vol-f08bff3a29b2d4886",
"volume_size": 5
},
"sensitive_attributes": [],
"private": "eyJlMmJmYjczMC1lY2FhLTExZTYtOGY4OC0zNDM2M2JjN2M0YzAiOnsiY3JlYXRlIjo2MDAwMDAwMDAwMDAsImRlbGV0ZSI6NjAwMDAwMDAwMDAwfX0=",
"dependencies": [
"aws_ebs_volume.k8s_volume"
]
}
]
},
{
"mode": "managed",
"type": "aws_ebs_volume",
"name": "k8s_volume",
"provider": "provider[\"registry.terraform.io/hashicorp/aws\"]",
"instances": [
{
"schema_version": 0,
"attributes": {
"arn": "arn:aws:ec2:us-east-1::volume/vol-f08bff3a29b2d4886",
"availability_zone": "us-east-1a",
"encrypted": false,
"final_snapshot": false,
"id": "vol-f08bff3a29b2d4886",
"iops": 0,
"kms_key_id": "",
"multi_attach_enabled": false,
"outpost_arn": "",
"size": 5,
"snapshot_id": "",
"tags": {
"Name": "devops-vol"
},
"tags_all": {
"Name": "devops-vol"
},
"throughput": 0,
"timeouts": null,
"type": "gp2"
},
"sensitive_attributes": [],
"private": "eyJlMmJmYjczMC1lY2FhLTExZTYtOGY4OC0zNDM2M2JjN2M0YzAiOnsiY3JlYXRlIjozMDAwMDAwMDAwMDAsImRlbGV0ZSI6NjAwMDAwMDAwMDAwLCJ1cGRhdGUiOjMwMDAwMDAwMDAwMH19"
}
]
}
],
"check_results": null
}
This is completely bugged…
Hi @besnija,
I still can’t reproduce the issue on my side. I also don’t see any problems with your code. Could you please try again? I don’t think it is a persistent issue.
Hello @raymond.baoly I just tried again without the data and output resource by simply mimicking what you stated in your screenshot, and following the instructions provided but without success. Is there a way to bypass this?
I cannot “skip” this one and get new tasks sadly and I would like to continue my training ![]()
Hi @besnija,
Could you please record a video showing the issue? I think it might only be happening with your account.
Hello @raymond.baoly I’ve uploaded the video to my GDrive, and you should be able to access and view it here.
Looking forward to your response.
Hi @besnija
I finally figured out why it failed. You used the wrong tag name, the display name tag for the snapshot should be ‘Name’ with a capital ‘N’, not ‘name’. Please try again.
Hello @raymond.baoly thank you very much for the solution!
It doesn’t really make much sense but whatever works is good enough ![]()
Hi @besnija
This is a rule from AWS. You can read more details in the official documentation here: Tag your Amazon EC2 resources - Amazon Elastic Compute Cloud