You've probably heard names like Cilium, Calico, Falco, and Hubble being tossed around.
But have you ever paused to think about what's under the hood of these cool tools? I bet most of you haven't. Don't sweat it; I'm here to break down all the eBPF Essentials for DevOps Professionals in the easiest way possible, using a fun example. Ready to dive in?
After JavaScript Made Websites Come Alive
Before the advent of JavaScript, web pages were static entities. They merely displayed content without much interaction. However, with JavaScript, web developers gained the ability to create responsive, interactive, and dynamic web applications. The web was no longer just about viewing content; it was about experiencing it. Web applications could now react in real time, engage users in unprecedented ways, and offer rich, app-like experiences directly within browsers.
Have you ever thought about the Linux Kernel? It's been known to be hard to change or add new things to it. But imagine if there was an easy way to make changes to the kernel, similar to how JavaScript made websites more interactive.
Think about this: What if every time you made a new folder in Linux, something immediately jumped into action? Like, right after you use the mkdir command, a tool could spot it, gather info on the new folder, and tell you all about it.
By listening to what's happening in Linux as it happens, we can do so much more. This could help with tasks, make our systems smarter, and open up many cool possibilities.
To get a clearer picture, let's consider an example:
I've got this Python program – let's call it the mysterious "X" python program(hello_ebpf.py). I'm going to run it on my Ubuntu terminal.
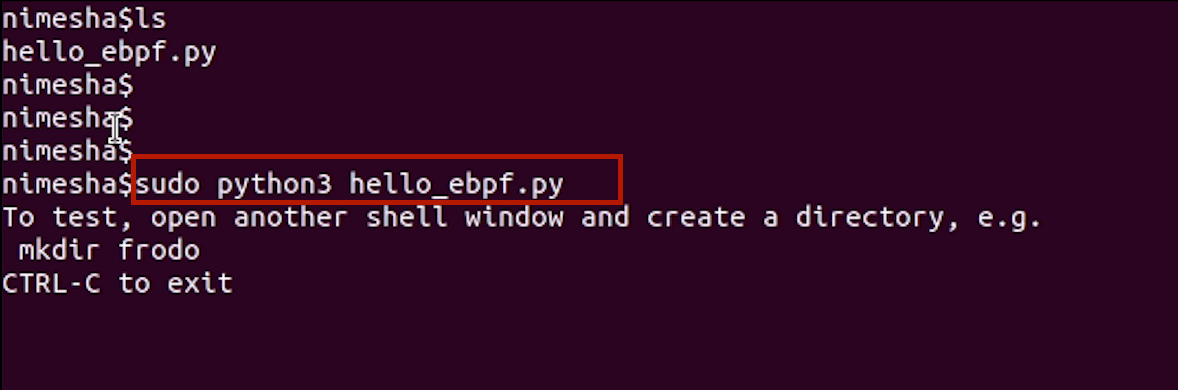
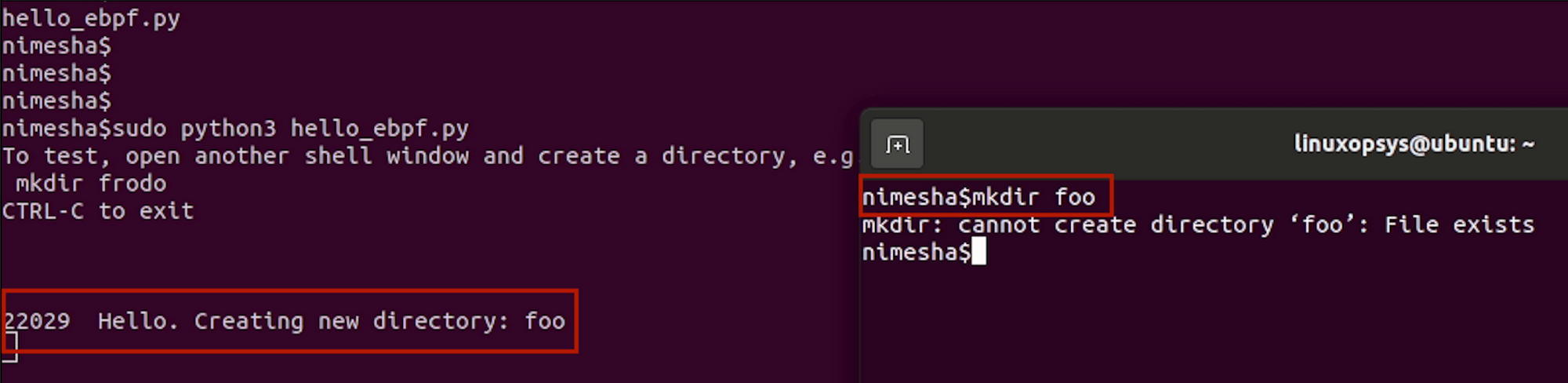
Alright, it's running. Now, I'll open a second terminal on the same machine and create a directory named "foo." Let's keep an eye on the first terminal. Wow, just like we imagined, it reacted!
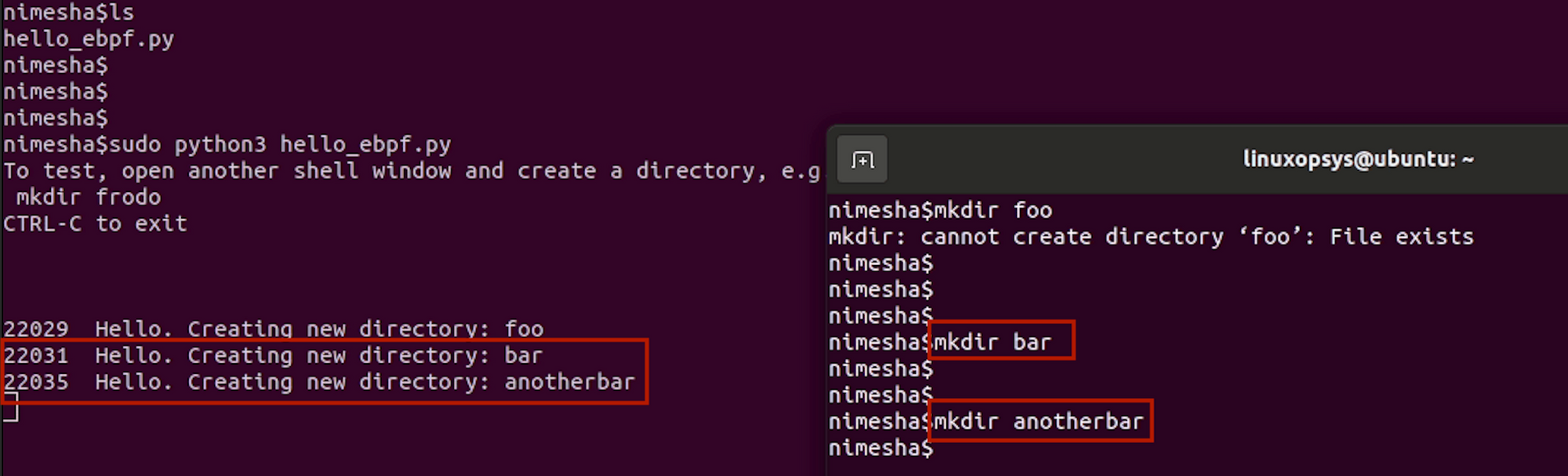
Let's try again. I'll make another couple of folders named "bar" and "anotherbar", And there it goes! Right after creating each folder, the other terminal shows a fancy "hello" message with the folder name.
It's all happening for real!
Wondering how that trick worked? Let's dive in.
Say hello to eBPF

I. Understanding eBPF
Understanding the Linux Kernel
At the heart of your Linux operating system sits the kernel. It's like a mediator between the applications you use and the physical hardware of your computer. Whenever an app needs to do something with the hardware, like access memory or manage files, it talks to the kernel. We don't usually see this interaction because it happens behind the scenes, and programming languages handle it for us.
Why Changing the Kernel Isn’t Easy
Changing the Linux kernel is a massive task. It's not just about writing code; it's also about convincing the Linux community (especially its creator, Linus Torvalds) that your change benefits everyone. The kernel itself is enormous – about 30 million lines of code! Even if your code does make it in, it could be years before it's widely used, as Linux distributions often use older kernel versions for stability and security.

The Challenge with Kernel Modules
One way to change the kernel is by using kernel modules. These can be loaded and unloaded as needed. But there's a catch: kernel programming is tricky. If something goes wrong, it could crash the entire system. Plus, there are security concerns. We must be sure that a kernel module won't be exploited for malicious purposes.
Enter eBPF: A Safer, More Flexible Approach
This is where eBPF (extended Berkeley Packet Filter) shines. It lets us safely and dynamically inject new features into the kernel. Unlike traditional methods, eBPF programs are checked rigorously by the eBPF verifier for safety before they're allowed to run. This verification process makes sure eBPF programs won't crash the system or access unauthorized memory areas.
eBPF in Action
With eBPF, you can quickly and safely add new functions to the kernel. Imagine wanting to track every time a folder is created or file is opened on your system, just as we discussed earlier in this blog. Using eBPF, you can write a program to do just that and load it into the kernel. It starts working right away, monitoring all file-open or file-create activities, regardless of when the processes were started.
II. Writing eBPF Programs
What is eBPF?
eBPF, which stands for extended Berkeley Packet Filter, is a Linux kernel technology that allows users to run custom programs within the kernel space without changing the kernel code. This offers an incredible advantage, enabling functionalities like performance analysis, network monitoring, and security.
Programming eBPF: Language Choices
While the kernel takes eBPF programs in bytecode, writing bytecode by hand is tedious. Instead, developers generally use higher-level languages. As of now, the best choices for writing eBPF programs are:
- C: Compiled using clang/llvm, it’s the most widely adopted language, given that the Linux kernel itself is written in C.
- Rust: A newer addition, but gaining traction due to its safety features.
Kernel vs. User Space Code
For eBPF tools, there are typically two parts:
- Kernel Space (eBPF program): This runs within the kernel.
- User Space Code: This interacts with the eBPF program, passing in configurations, and displaying the eBPF program's data. It can be written in languages like C, Go, Rust, or Python.
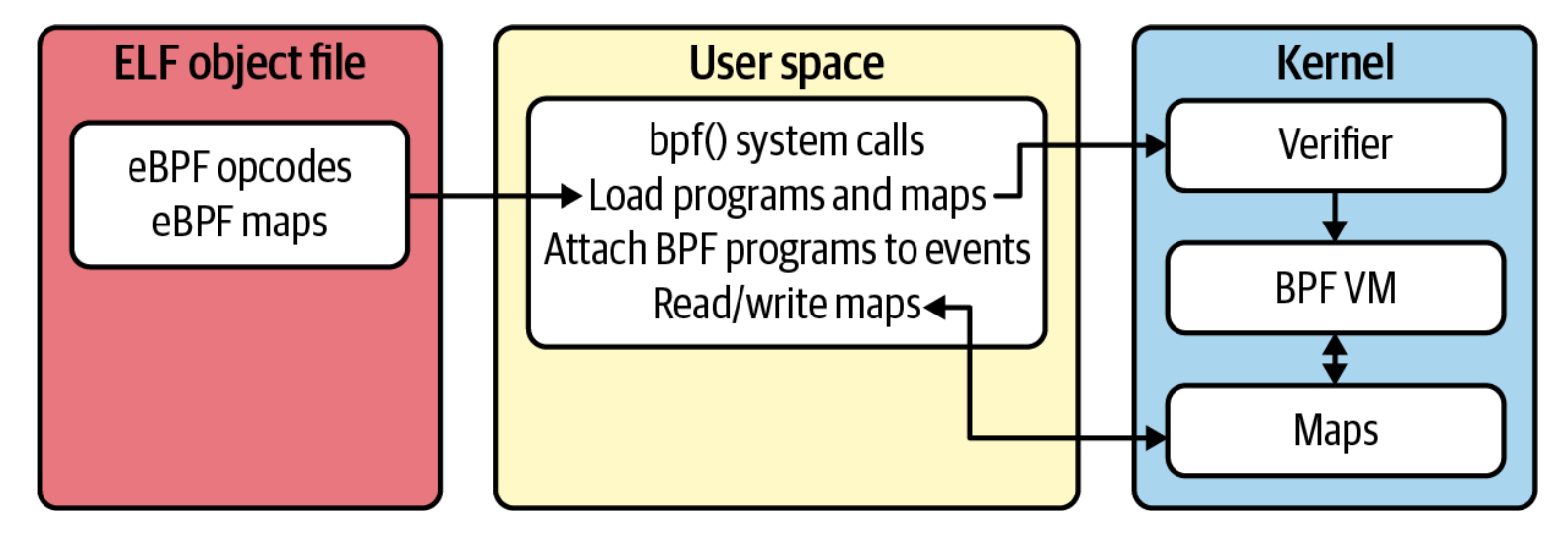
Attaching eBPF Programs to Events
Once an eBPF program is in the kernel, it needs an event to trigger it. Commonly used triggers include:
- Entry/Exit from functions using mechanisms like kprobes and fentry/fexit.
- Tracepoints within the kernel.
- Perf Events for performance data collection.
- Linux Security Module Interface for security policies.
- Network Interfaces with eXpress Data Path (XDP) for efficient networking functionality.
- Socket interactions and other network operations.
eBPF Maps: Bridging Kernel and User Space
eBPF Maps are key-value stores that allow data passage between eBPF programs and the user space. They're crucial for:
- Storing metrics and data about an event.
- Holding configuration details.
- Allowing coordination of information across multiple kernel events.
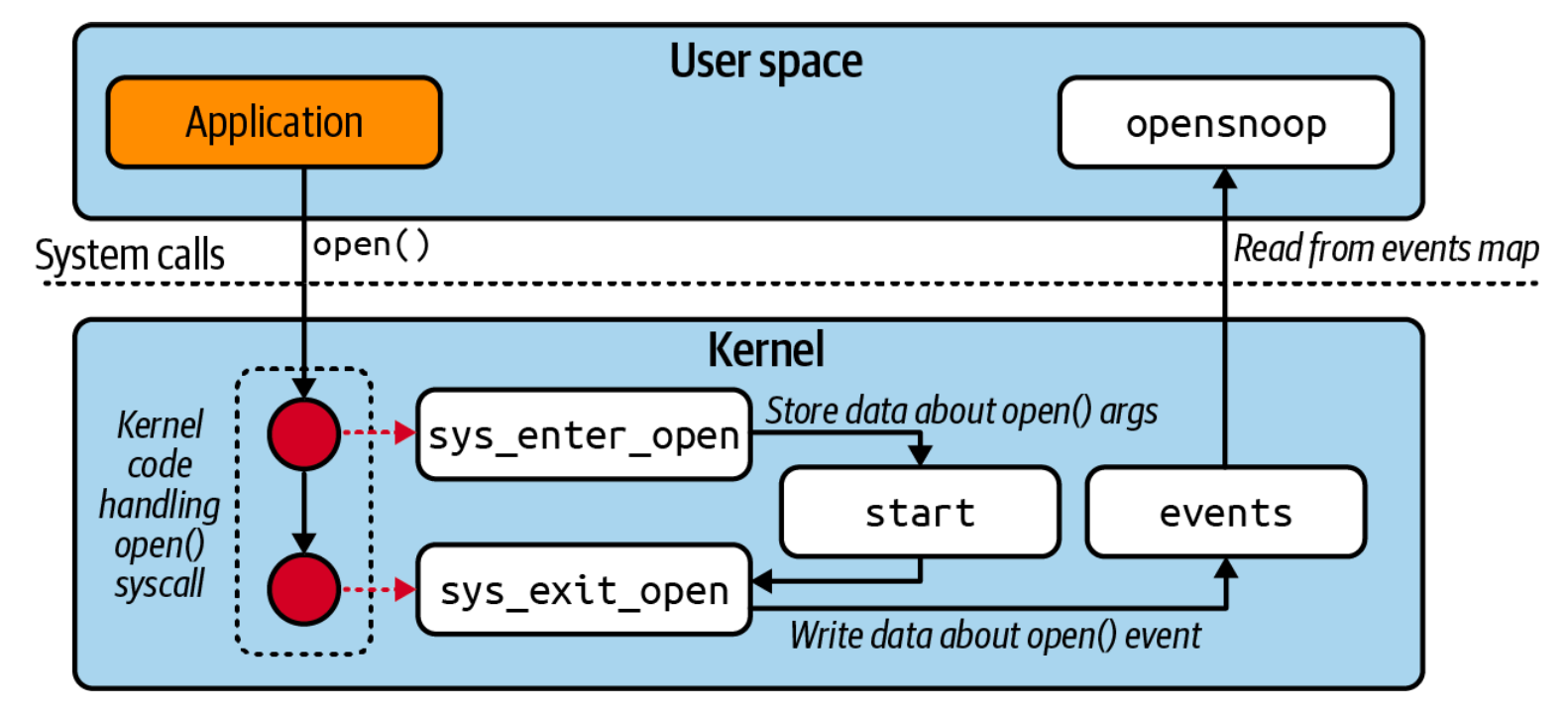
A Glimpse into Opensnoop: An eBPF Example
Opensnoop is a tool that displays files being opened by any process. It works by attaching eBPF programs to the open() and openat() system calls, collecting data, and then presenting it to the user.
III. The Rise of Cloud-Native and eBPF
Cloud-native computing has revolutionized the tech industry, with Kubernetes leading the way. In this blog, we'll explore why eBPF, a kernel-level technology, shines in this new environment. Let's start with some basics.
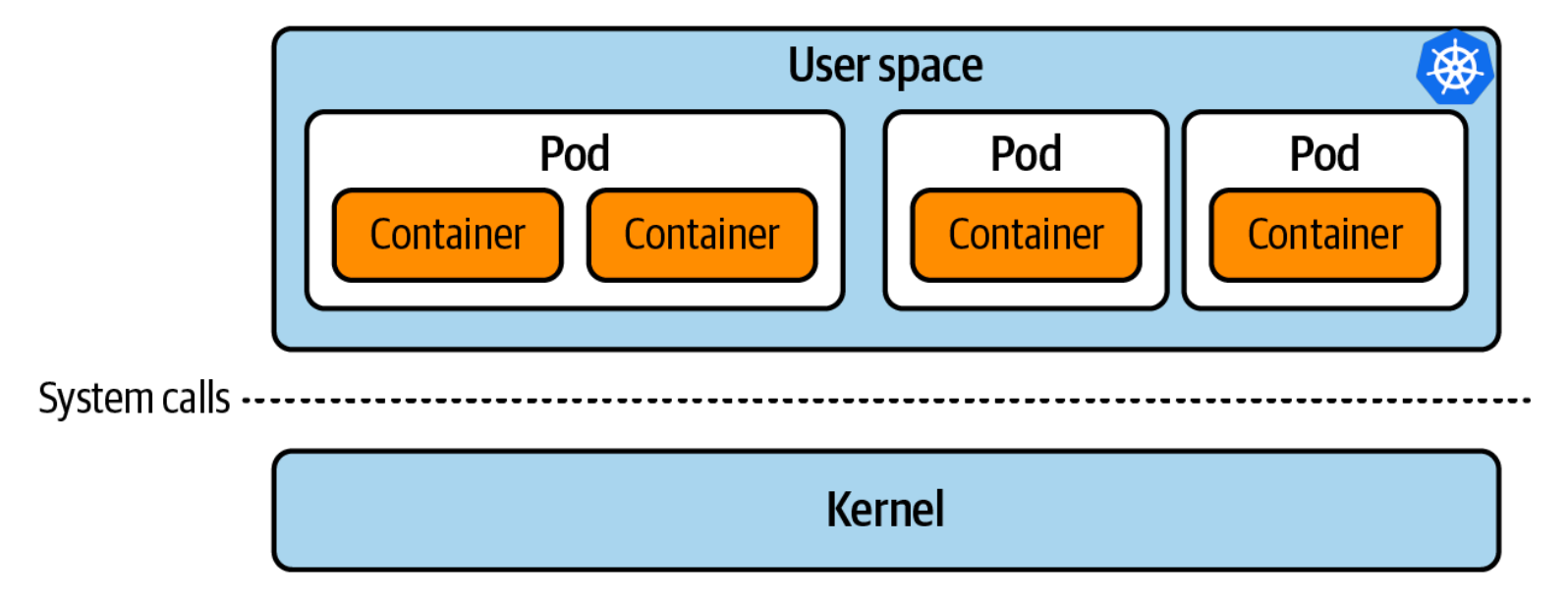
One Kernel Rules Them All
A core principle to grasp is that every machine (or virtual machine) has just one kernel. All containers on that machine share this kernel. This is important because by tapping into the kernel using eBPF, you get insights into every piece of application code running on that machine. Think of it as having a master switch that can control and monitor everything on the machine.
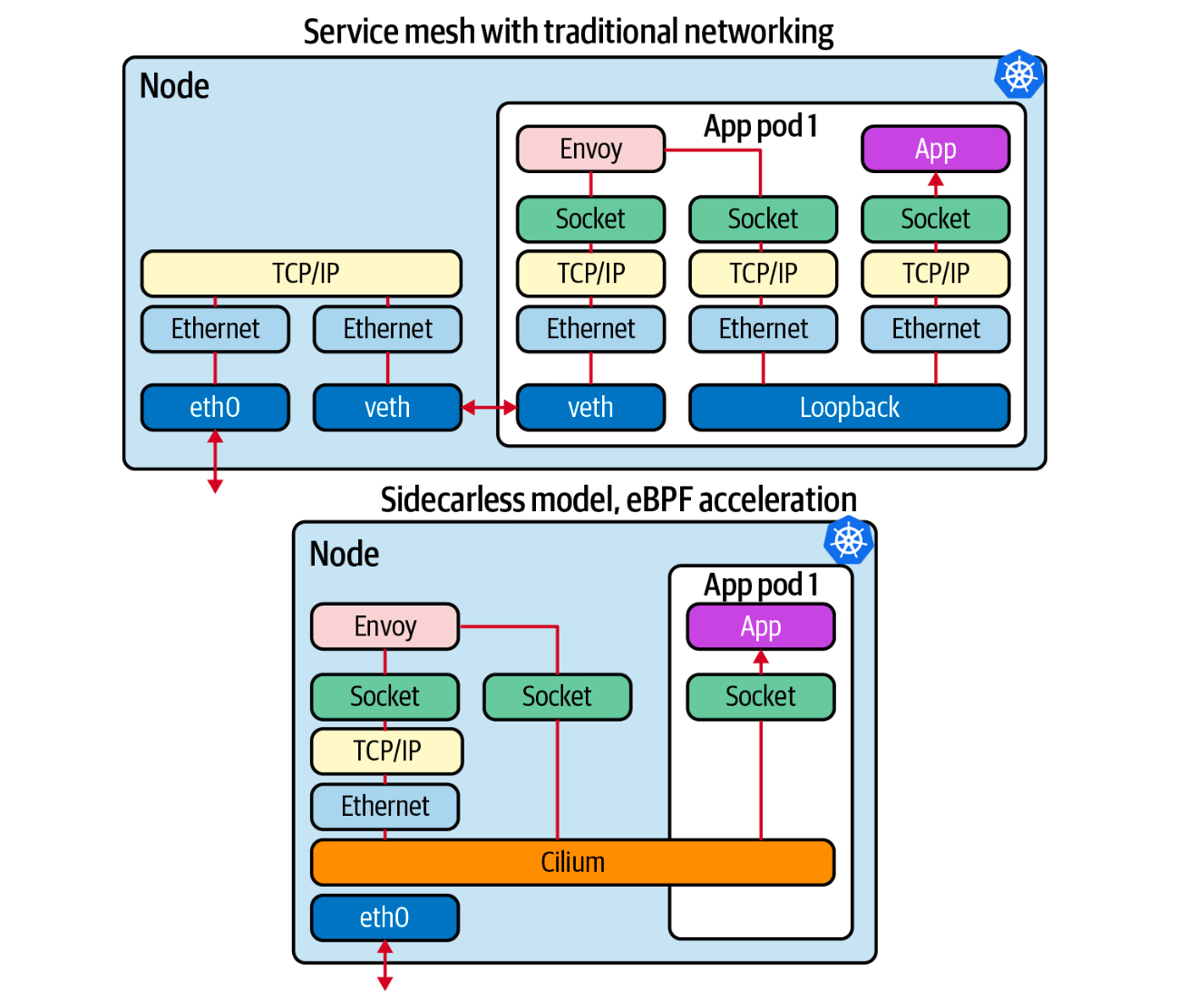
Comparing eBPF to the Sidecar Approach
Before eBPF's rise, Kubernetes tooling primarily relied on the sidecar model. This model adds an instrumentation container within the same pod as the application. While it was revolutionary at the time, it has its drawbacks:
- Resource Consumption: Every sidecar uses resources. Multiply this by many pods, and the consumption becomes significant.
- Coverage Concerns: Sidecars can't guarantee full instrumentation. Imagine a rogue application, like a cryptocurrency miner, launched by an attacker. This rogue pod might not have your sidecar tools, making it invisible to your monitoring.
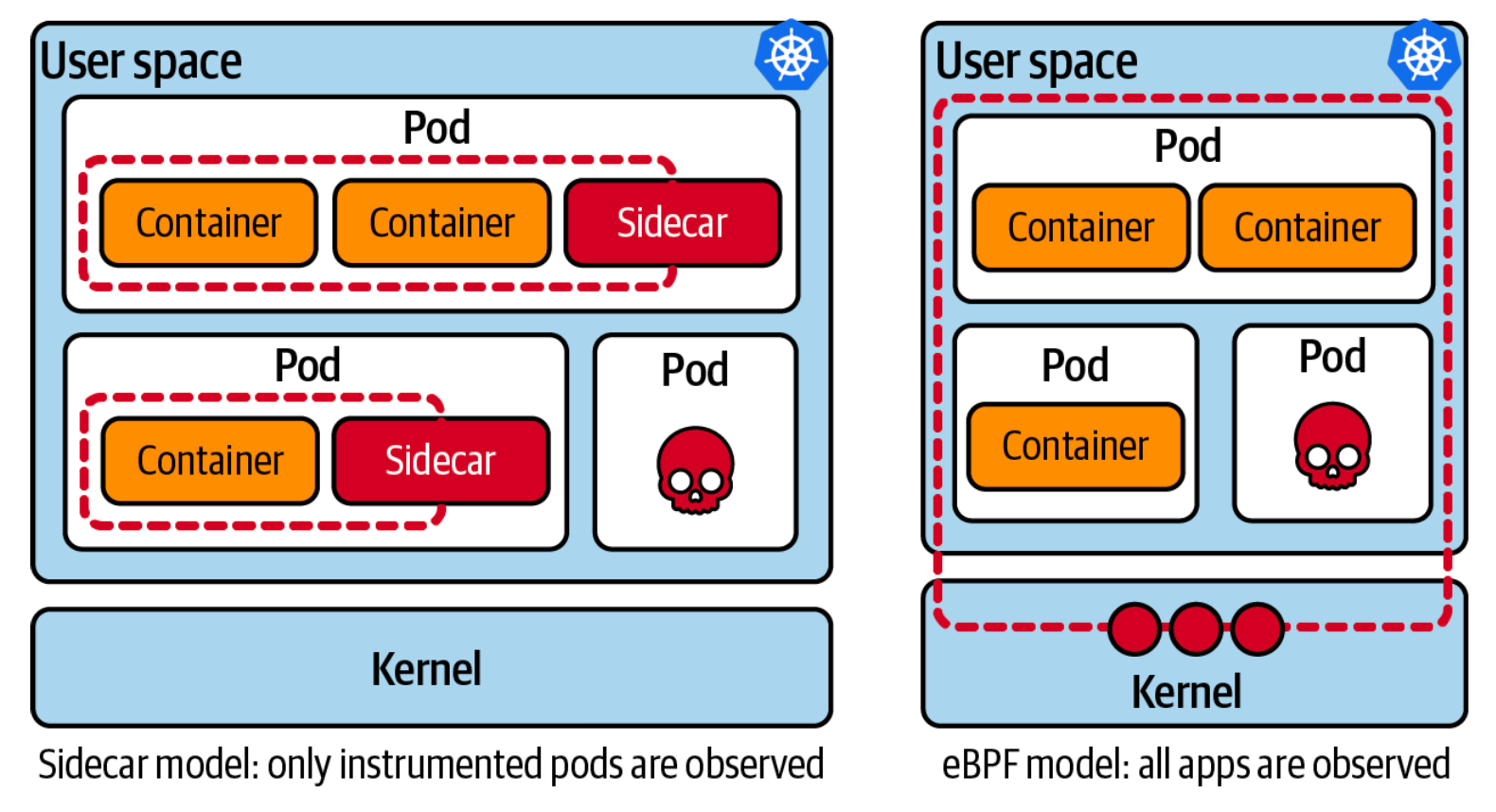
In contrast, with eBPF, this rogue application can't hide. It shares the kernel with legitimate pods. Once you deploy eBPF, it sees everything.
Understanding eBPF and Process Isolation
You might wonder, if eBPF can see everything, doesn't that pose a security risk? It's a valid concern, but here's why eBPF is still safe:
- Kernel's Role: Remember, the kernel doesn't know about "containers" or "pods." It only knows processes. Linux uses cgroups and namespaces to keep processes from interfering with each other. Your safety relies on the kernel doing its job right.
- eBPF's Strict Guard: eBPF programs go through a strict check (by the eBPF verifier) to ensure they can't misbehave. This makes eBPF more restrictive than regular kernel code.
To put it simply, your system's security hinges on the kernel. If someone breaks out of a container, they've essentially gained access to the entire machine. eBPF doesn't change that risk; it just provides a more efficient way to monitor and manage it.
IV. eBPF for Enhanced Cloud-Native Tools"
In this part, we'll be exploring the powerful eBPF-based tools that are currently reshaping the landscapes of networking, observability, and security in cloud-native deployments. Whether you're a system administrator, a developer, or simply an enthusiast, understanding these tools will give you a competitive edge in the evolving world of cloud-native computing.
eBPF in Networking
Load Balancing with eBPF
eBPF's capability to inspect and modify network packets has reshaped networking. For instance:
- Facebook's Katran: A testament to eBPF's scalability, Facebook's layer 4 load balancer, has proven eBPF's potential in massive networks.
- Cloudflare’s Unimog & Cilium: These tools utilize eBPF to efficiently redirect network packets, skipping the need for them to pass through the entire networking stack.
Kubernetes and eBPF
Kubernetes has embraced eBPF, most notably through the CNCF project Cilium. This tool simplifies routing, turning it into a straightforward lookup in eBPF, enhancing performance and scalability.
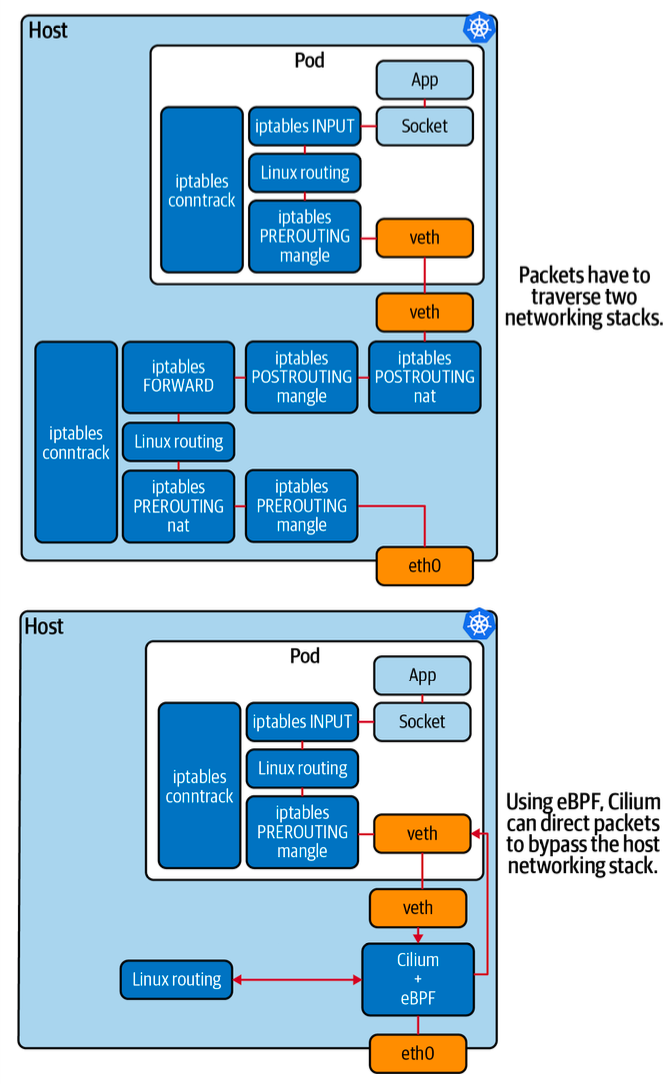
Service Mesh: A New Approach
Service mesh tools often use proxies to manage application traffic. eBPF offers a more efficient approach, connecting pod applications to a single proxy, leading to a more streamlined system.
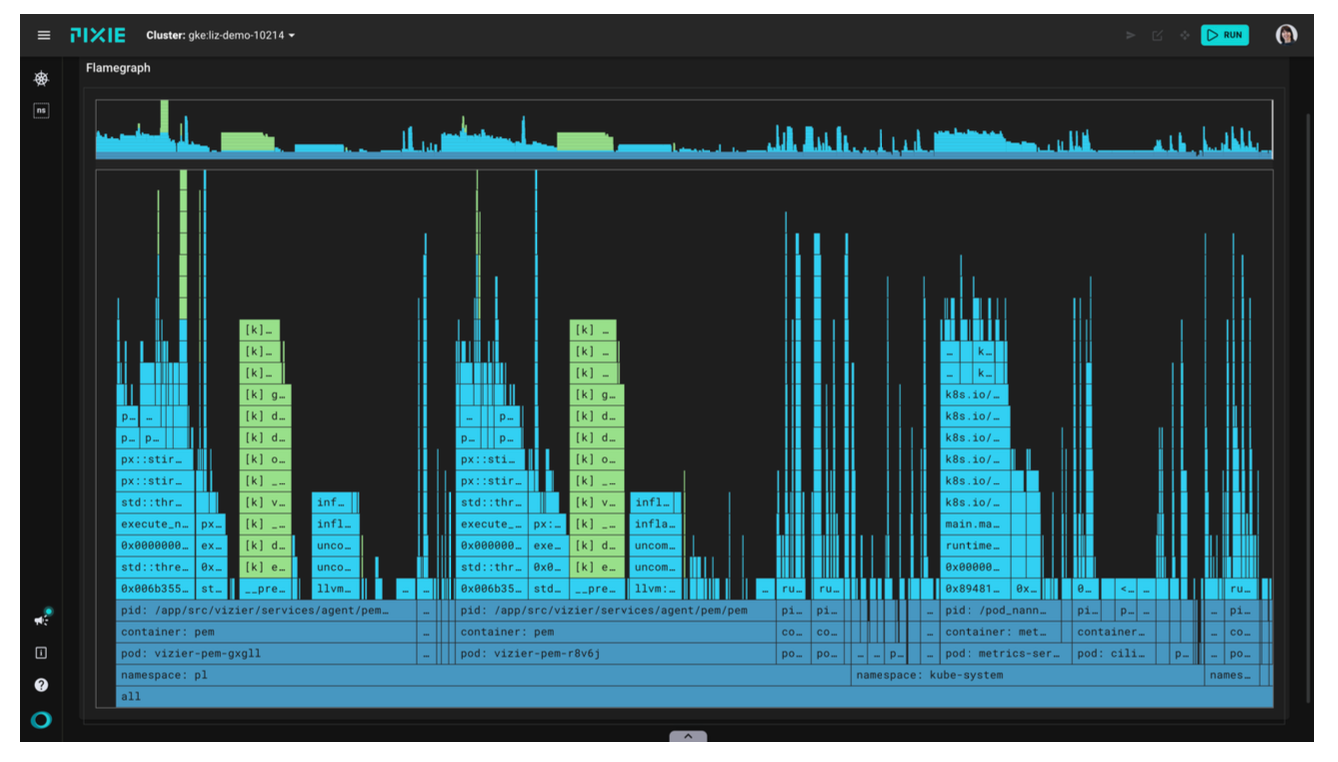
Observability: Seeing All with eBPF
eBPF grants complete visibility into machine operations. Here's a glimpse of what's possible:
- BCC and Inspektor Gadget: Tools like these enable the detailed monitoring of metrics at scale.
- Pixie & Parca: These projects offer visual insights into system performance, letting users understand system behavior without altering their applications.
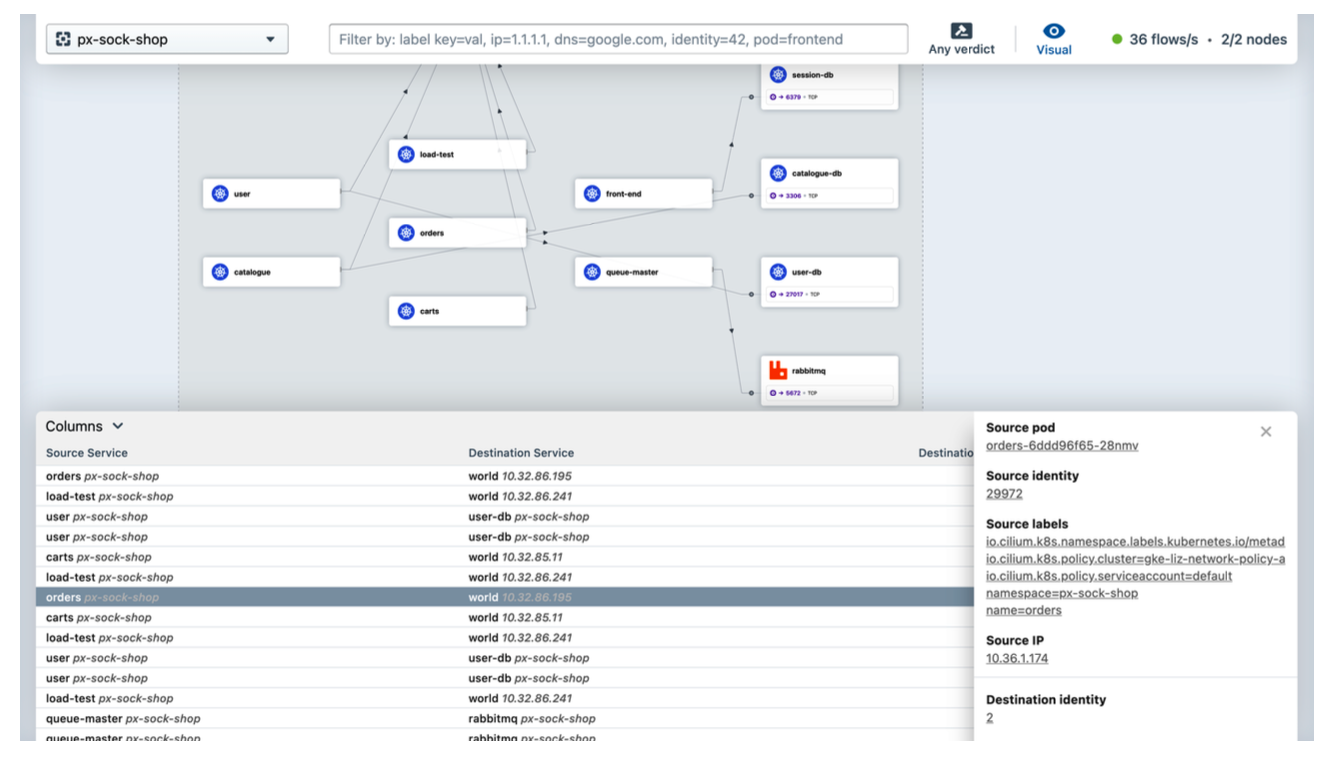
- Hubble: Part of Cilium, this tool focuses on visualizing network flows in Kubernetes clusters, offering clarity in dynamic cloud-native environments.
Security: eBPF at the Forefront
eBPF amplifies security measures in two main areas:
Network Security
By inspecting and acting upon network packets, eBPF fortifies defenses. Notably:
- DDoS protection: Cloudflare uses eBPF to swiftly detect and discard malicious traffic, safeguarding systems from overload.
- Kubernetes: Tools like Cilium and Calico enforce network policies, offering granular control over network traffic.

Runtime Security
eBPF tools, like Falco and Tracee, monitor application behaviors in real-time, detecting anomalies and potential threats. They provide insights into system operations, making it easier to detect and counteract malicious activities.
Wrapping Up on eBPF's Power
By now, you've got a glimpse into the world of eBPF and its incredible capabilities. If there's one thing to take away, it's this: eBPF is transforming the way we approach cloud-native computing.
If you're curious to dig deeper, ebpf.io is a goldmine of information.
For those eager to get their hands dirty with coding, check out beginner-friendly resources on GitHub.
For a real treat, consider attending events like the eBPF Summit and Cloud Native eBPF Day. These gatherings are perfect for hearing firsthand experiences and breakthroughs from the community.
And speaking of community, there's a vibrant Slack group that's always buzzing with eBPF discussions. So, why wait? Dive in, connect, and experience firsthand the eBPF revolution in cloud-native environments!
Coming Up...
Stay tuned! In the next blog, we'll delve deeper and explore how to write your very own eBPF program. Trust me, you won't want to miss it!
References : What is eBPF? OReilly report














Discussion